Email Whitelisting: How to Do It, When to Skip It, and What Actually Works in 2026
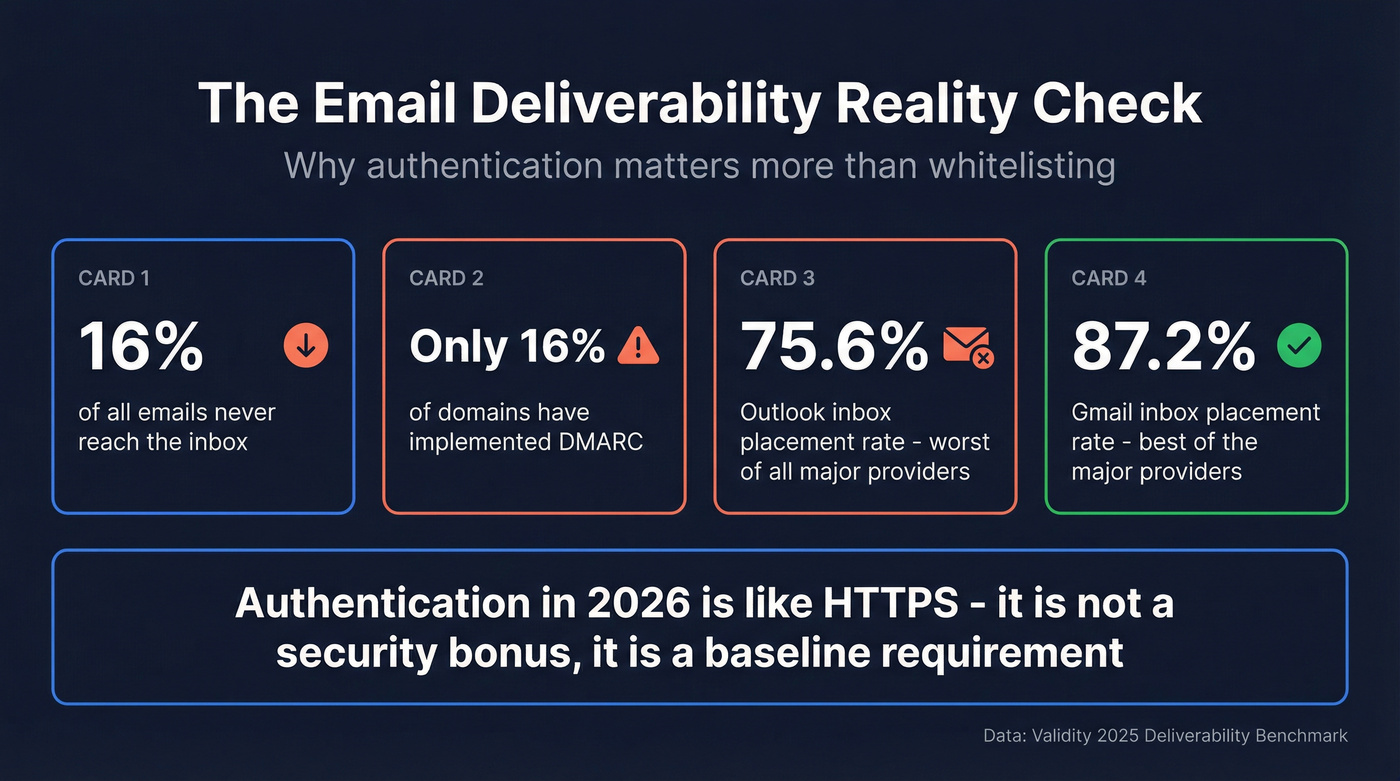
One in six emails never reaches the inbox. That's not a rounding error - it's roughly 16% of every campaign, every transactional receipt, every sales follow-up vanishing into spam folders or getting silently dropped. And the fix most people Google first - "how to whitelist an email" - is the equivalent of putting a Band-Aid on a broken pipe.
Here's the thing: email whitelisting still has a place. But in 2026, it's the last step in a deliverability strategy, not the first. The real work happens at the infrastructure level - SPF, DKIM, DMARC - and most senders haven't done it yet. Only 16% of domains have implemented DMARC. That's the actual problem.
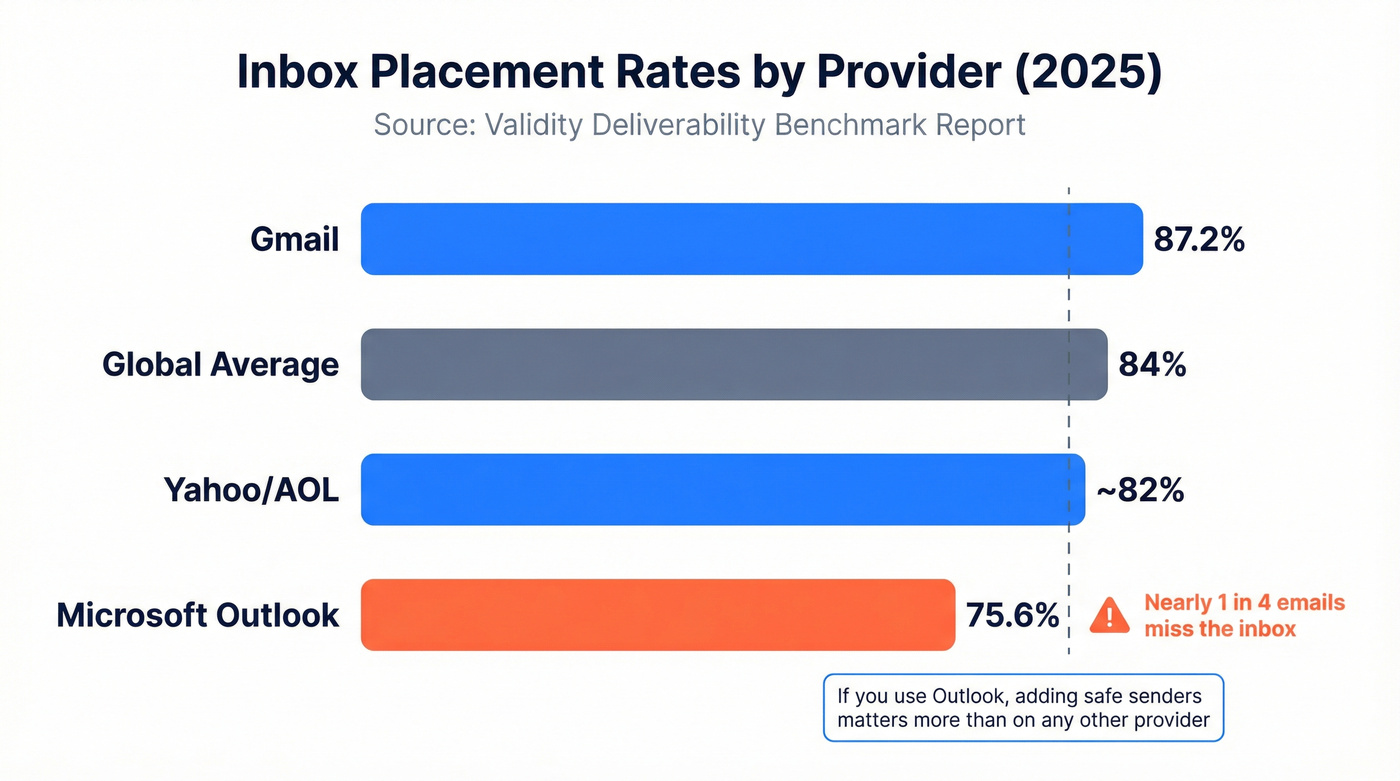
The global inbox placement average sits at roughly 84%, per Validity's most recent Deliverability Benchmark. Microsoft Outlook is the worst offender at 75.6% inbox placement - meaning nearly a quarter of emails sent to Outlook addresses either hit spam or disappear entirely. Gmail fares better at 87.2%, but even that means 1 in 8 emails miss the inbox.
Whether you're an end user trying to rescue a newsletter from spam, an IT admin fielding vendor requests, or a marketer watching open rates crater, this guide covers the actual steps - and more importantly, when those steps aren't enough.
What You Need (Quick Version)
End Users ("my emails keep going to spam")
Jump to the how-to section below. Pick your email provider, follow the steps to whitelist email addresses in under 30 seconds.
IT Admins ("a vendor asked me to whitelist them")
Tell them to fix their SPF/DKIM/DMARC first. If you genuinely need to create an organizational allowlist, jump to the enterprise admin section - but read the security risks section too.
Email Marketers ("my campaigns are landing in junk")
Whitelisting is a band-aid. Fix your authentication, clean your list, then ask subscribers to add your address to their safe sender list. Jump to the marketer section.
What Is an Email Whitelist?
An email whitelist is a list of trusted senders or domains whose messages bypass your spam filters and land directly in your inbox. Every major email provider supports it - through safe sender lists, contact additions, or filter rules.
The mechanics are simple: you tell your email client "I trust this sender," and it stops filtering their messages.
Whitelist vs. Allowlist: The industry is shifting from "whitelist/blacklist" to "allowlist/blocklist)" for inclusivity reasons. Google, Apple, Splunk, and many security vendors have adopted the newer terms. But over 90% of email security products still use "whitelist" in their interfaces and documentation. They mean the same thing. This guide uses both, because the tools do too.
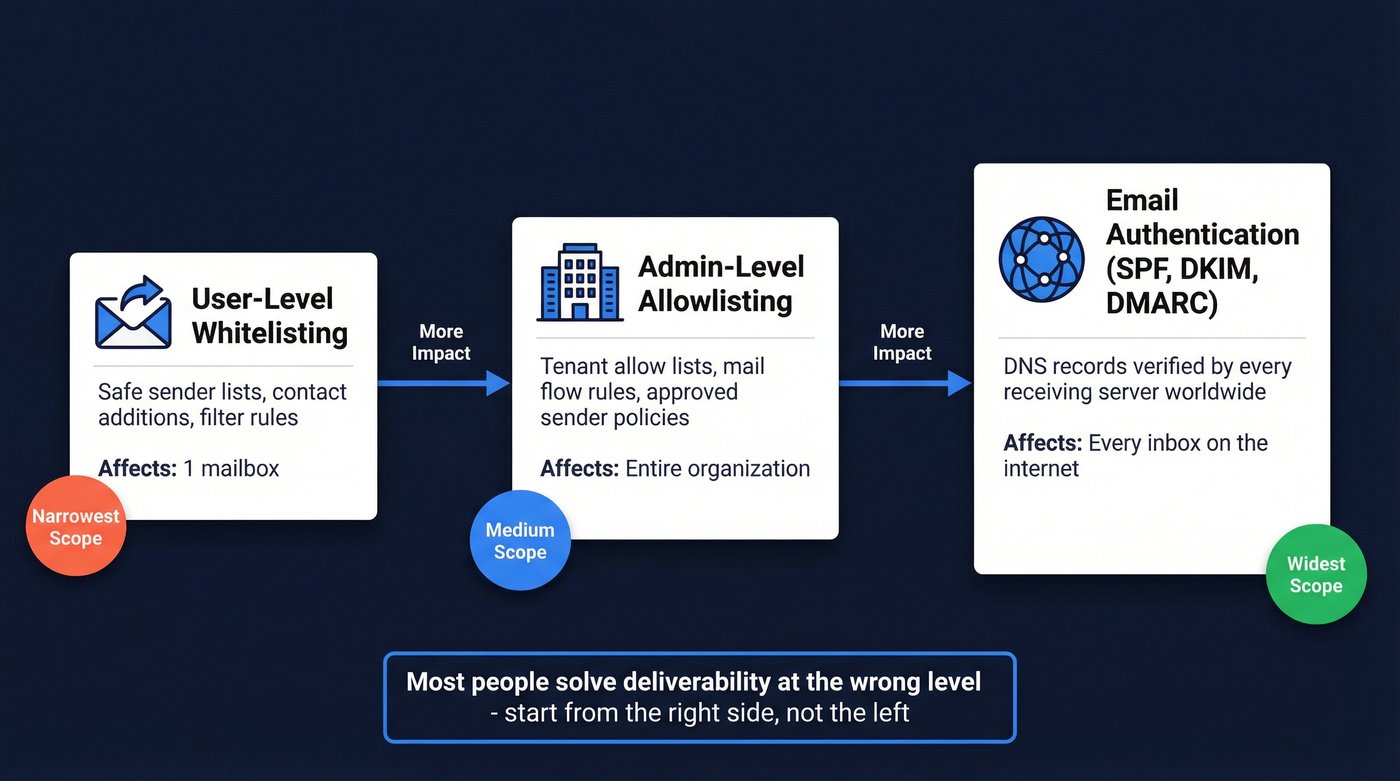
The important distinction isn't terminology. It's scope. User-level whitelisting affects one mailbox. Admin-level allowlisting affects an entire organization. And email authentication (SPF/DKIM/DMARC) works globally, across every receiving server on the internet. That hierarchy matters - and most people are solving the problem at the wrong level.

Whitelisting fixes the symptom. Bad email data is the disease. When you send to outdated or unverified addresses, you tank your sender reputation and trigger spam filters. Prospeo's 5-step verification and 7-day data refresh cycle mean 98% email accuracy - so your outreach lands in inboxes without begging recipients to whitelist you.
Skip the deliverability headaches. Start with emails that actually work.
How to Whitelist an Email Address (By Provider)
Quick-reference table before we get into the steps:
| Provider | Desktop Path | Mobile Path |
|---|---|---|
| Gmail | Settings → Filters → Create | Mark "Not Spam" |
| Outlook.com | Settings → Junk → Safe Senders | Move to Focused Inbox |
| Outlook Desktop | Home → Junk → Options | Same as Outlook.com |
| Yahoo Mail | Settings → Filters → Add | Spam → Move to Inbox |
| Apple Mail | Preferences → Rules → Add | Move from Junk |
| ProtonMail | Add to Contacts / Filters | Same as desktop |
| Zoho Mail | Settings → Anti-Spam | Same as desktop |
| AOL Mail | Add sender to Contacts | Same as desktop |
Gmail (Desktop & Mobile)
Desktop: Open Gmail → click the gear icon → See all settings → Filters and Blocked Addresses → Create a new filter. In the "From" field, enter the email address (or @domain.com to approve an entire domain). Click "Create filter" → check "Never send it to Spam" → Create filter.
Mobile: If the email's already in spam, open it and tap "Report not spam." Gmail learns from this. For a more permanent fix, you'll need to use the desktop version to create a filter - Gmail's mobile app doesn't support filter creation.
Pro tip: Also add the sender to your Google Contacts. Gmail treats contact senders more favorably in its filtering algorithms, effectively treating them as trusted.
Outlook.com & Outlook Desktop
Outlook.com (web): Settings → Mail → Junk email → Safe senders and domains → Add the email address or domain. Done. This is the fastest way to add a trusted sender in Outlook.
Outlook Desktop: Home tab → Junk → Junk E-mail Options → Safe Senders tab → Add the address or domain.
Mobile: Open the message → tap the three dots → "Move to Focused Inbox" → select "Always Move." This trains Outlook's filters for that sender going forward.
Given Outlook's 75.6% inbox placement rate, adding senders to your safe list matters more here than on any other provider. If you're expecting important emails from a specific sender and you're on Outlook, don't skip this step.
Yahoo Mail
Desktop: If the email's in spam, open it and click "Not Spam." For proactive setup: Settings → More Settings → Filters → Add new filters. Set the "From" field to the sender's address, set the action to "Move to Inbox."
Mobile: Open the Spam folder → select the email → tap Move → choose Inbox. Yahoo's mobile app doesn't have a dedicated safe sender list, so moving from spam is your best option.
Apple Mail (macOS & iOS)
macOS: Mail → Preferences (or Settings on newer macOS) → Rules → Add Rule. Set the condition to "From contains [sender address]" and the action to "Move Message to Inbox." Click OK.
iOS: There's no native allowlist feature in iOS Mail. Your best options: add the sender to Contacts (which helps with filtering), or if the email's in Junk, tap "Move to Inbox" and mark it as "Not Junk."
ProtonMail, Zoho, AOL & Others
ProtonMail: Add the sender to your Contacts, or create a filter (Settings → Filters → Add new filter) that routes their messages to your inbox. ProtonMail doesn't have a dedicated "safe senders" list - contacts and filters are your tools.
Zoho Mail: Settings → Anti-Spam → Email Address → Allowlist/Blocklist Emails → Add the sender's email address or domain to the allowlist. Zoho also supports organization-level allowlists through the Admin Console.
AOL Mail: Add the sender to your Contacts (Contacts → New Contact → enter the email → Save). AOL treats messages from contacts more favorably. If an email's already in spam, mark it as "Not Spam."
Thunderbird, EarthLink, or other legacy clients: The process is similar across the board - add the sender to your address book or create a message filter rule that routes their emails to your inbox. Takes under a minute.
Enterprise Allowlisting for IT Admins
Look, if a vendor asks you to approve their emails and their SPF fails, their DKIM is missing, and their DMARC is misconfigured - the answer is no. Tell them to fix their authentication. I've seen this play out dozens of times: a vendor (sometimes ironically a security vendor) outsources email to a third party with broken authentication, their welcome emails get flagged as high-confidence phishing by M365 ATP, and their solution is "please add these 11 email addresses to your safe senders list."
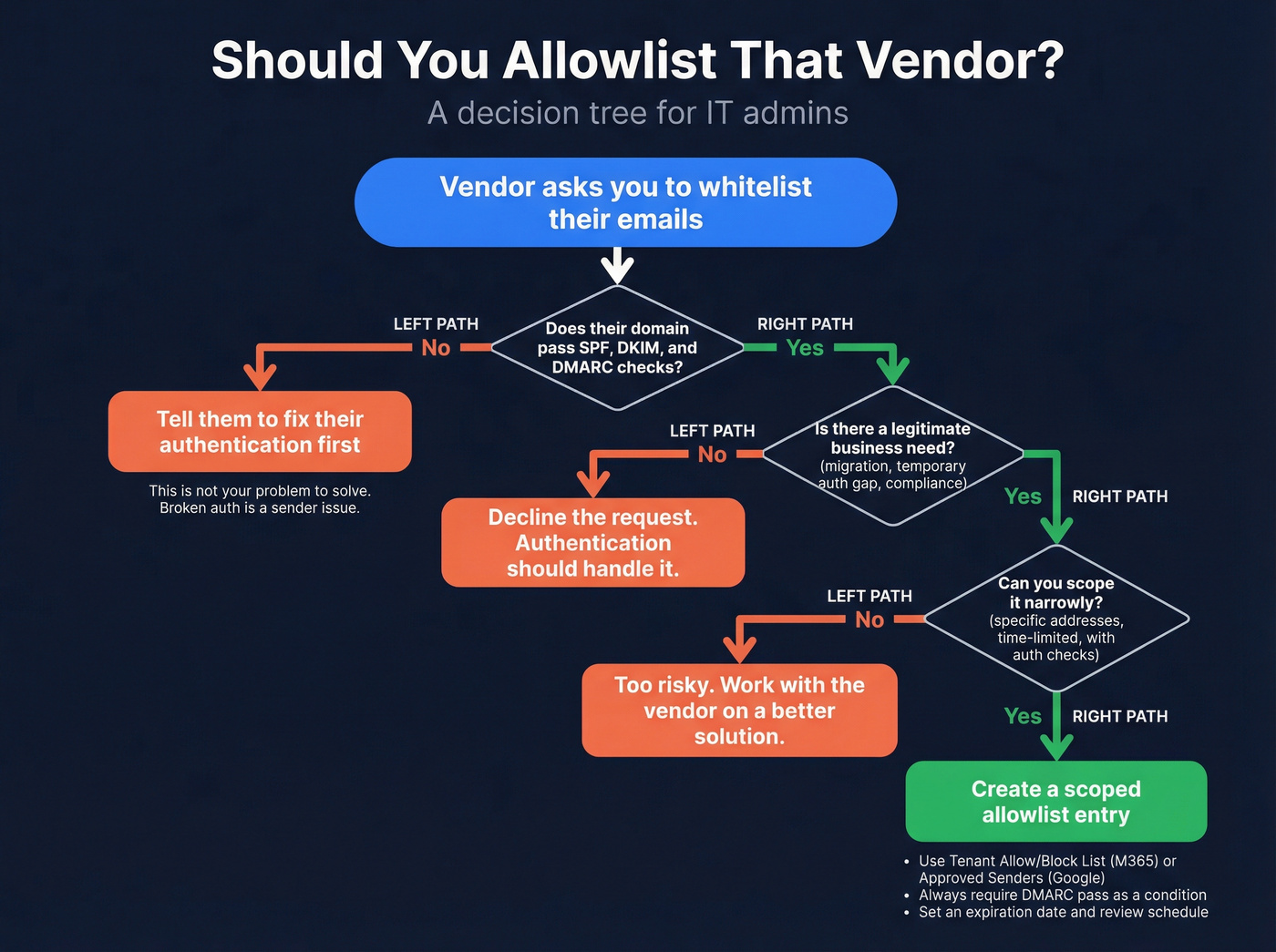
That's not a solution. That's a liability.
But sometimes you genuinely need to create an organizational allowlist - for a trusted partner during a migration, a critical SaaS tool with a temporary authentication gap, or a compliance requirement. Here's how to do it without blowing a hole in your security posture.
Microsoft 365 Admin (Tenant Allow/Block List & Mail Flow Rules)
Microsoft ranks its allowlist methods from most to least recommended:
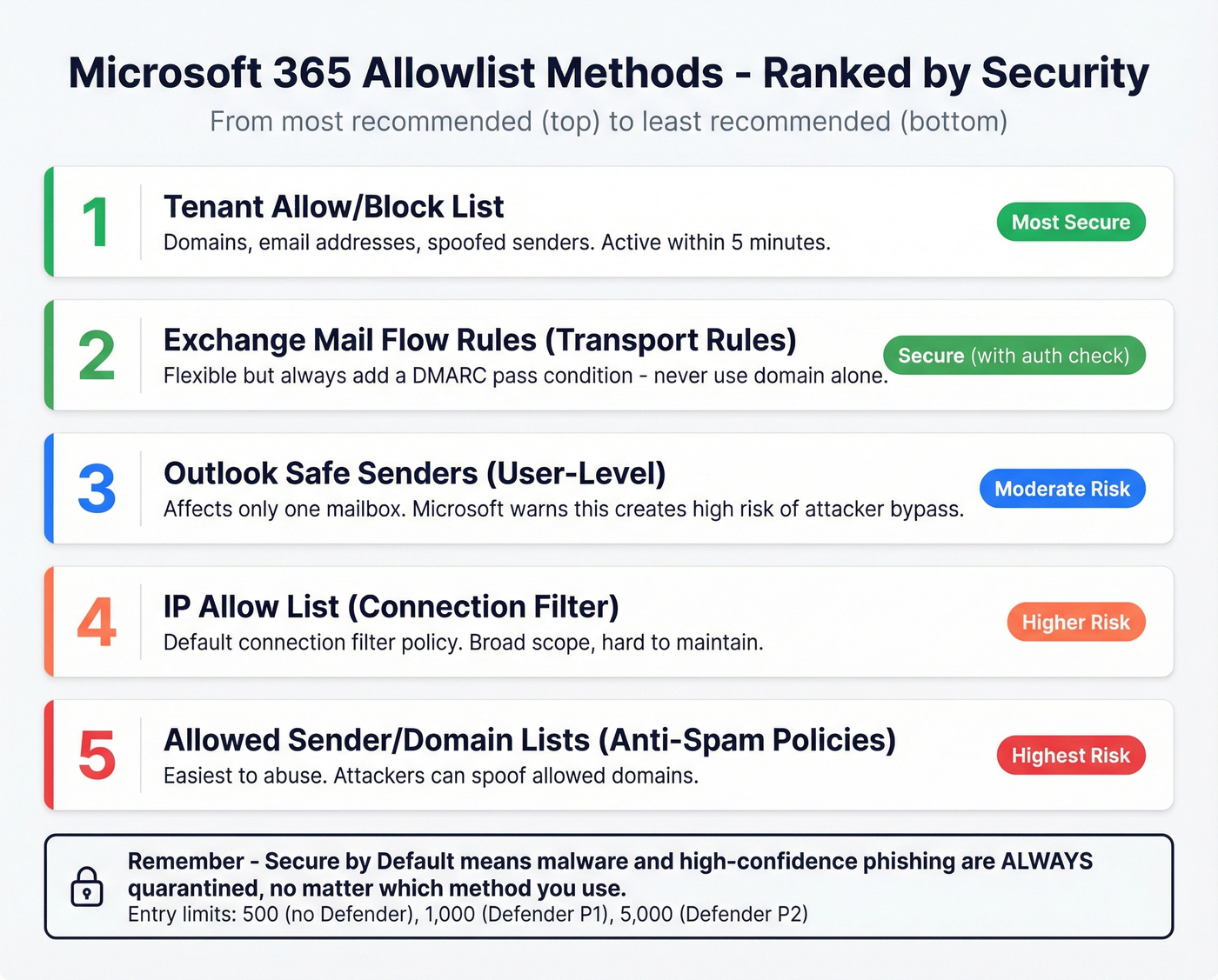
- Tenant Allow/Block List - domains, email addresses, spoofed senders
- Exchange mail flow rules (transport rules)
- Outlook Safe Senders (user-level, affects only that mailbox)
- IP Allow List in default connection filter policy
- Allowed sender/domain lists in anti-spam policies
Start with the Tenant Allow/Block List. It's the most secure option and entries become active within 5 minutes. Entry limits depend on your license: 500 allow entries without Defender, 1,000 with Defender Plan 1, 5,000 with Defender Plan 2.
Critical caveat: Microsoft's "Secure by Default" policy means messages identified as malware or high-confidence phishing are always quarantined, regardless of which allowlist method you use. You can't override this, and you shouldn't want to.
Mail flow rule warning: Never use sender domain alone as a condition. An attacker can spoof the domain and bypass all your filtering. Always add an authentication check - specifically, require that the Authentication-Results header contains dmarc=pass or dmarc=bestguesspass. This is the single most important step most admins skip.
Microsoft explicitly warns that user-level Safe Senders "creates a high risk of attackers successfully delivering email that would otherwise be filtered." If you're debating whether to remove user-level allowlisting ability entirely, the security argument is clear. The counterargument - it'll flood your help desk - is real but manageable with good communication.
Google Workspace Admin (Admin Console & Approved Senders)
Path: Admin Console → Apps → Google Workspace → Gmail → Spam, Phishing and Malware.
IP-based allowlisting: Hover over "Email whitelist" → Edit → enter sending IP addresses (comma-separated) → Save. In Google Workspace, this specifically refers to an IP-level bypass.
Domain/address-based allowlisting: In the Spam section → Configure → select "Bypass spam filters for messages received from addresses or domains within these approved senders lists" → click "Create or edit list" → add the sender domain or address.
The toggle that matters: "Authentication required." When this is ON, Google still checks SPF/DKIM for approved senders. When it's OFF, you're bypassing authentication entirely. Leave it ON unless you have a specific, temporary reason to disable it - and document that reason, because your security team will ask.
The Real Fix: SPF, DKIM, and DMARC Authentication
Why Authentication Replaced Traditional Whitelisting
A sysadmin on r/sysadmin framed it well: SPF/DKIM/DMARC configuration is whitelisting - at the infrastructure level. In 2026, emails from domains without proper authentication are automatically rejected or spam-foldered by every major provider. Implementing these protocols is effectively approving your own domain across the entire internet.
The analogy that clicks: authentication in 2026 is like HTTPS. It's not a security bonus. It's a baseline requirement. Without it, you don't get to play.
Traditional safe sender lists operate on one mailbox or one organization. Authentication operates globally. That's why it replaced the old model - it scales, it's verifiable, and it doesn't create security holes.
| Dimension | User-Level | Admin-Level | Authentication |
|---|---|---|---|
| Scope | One mailbox | Entire org | All servers globally |
| Who controls it | End user | IT admin | Sending domain owner |
| Scales | No | Partially | Yes |
| Security risk | High | Medium | Low |
| Survives compromise | No - attack vector | No - attack vector | Yes - spoofs still fail |
| Required in 2026 | Optional | Optional | Mandatory |
The 2024-2026 Authentication Mandates
The mandates came fast:
- February 2024: Google and Yahoo require SPF, DKIM, and DMARC for bulk senders (5,000+ messages/day).
- May 2025: Microsoft follows suit for Outlook consumer domains (hotmail.com, live.com, outlook.com). Non-compliant messages get rejected with error
550; 5.7.515. - September 2025: La Poste (France's national postal service) adds its own requirements.
The pattern is clear: every major email provider now mandates authentication. If your domain doesn't pass SPF, DKIM, and DMARC checks, your emails don't reach inboxes - no amount of user-level safe sender lists will save you.
And the adoption gap is staggering. Only 16% of domains have implemented DMARC, leaving the vast majority vulnerable to both spoofing and delivery failures. A typical DMARC implementation takes 6-8 weeks. If you haven't started, you're already behind.
Hot take: If your deal sizes are under $50k and you're spending time asking customers to add you to their safe senders instead of fixing your DMARC, you're solving the wrong problem. DMARC is free. It works everywhere. Allowlist requests are a tax on your customers' patience - and most of them will ignore you anyway.
SPF, DKIM, and DMARC Cheat Sheet
SPF:
- End your record with
~all(softfail), not-all(hardfail). Hard fail can cause receiving servers to block messages before evaluating DKIM and DMARC. - Stay under the 10 DNS lookup limit. Use SPF flattening tools if you're hitting it.
- Every third-party service that sends on your behalf (CRM, marketing platform, support tool) needs to be included.
DKIM:
- Use
rsa-sha256signing algorithm. - 2048-bit key length minimum.
- Rotate keys at least every 6 months. Most teams forget this.
DMARC:
- Start with
p=nonefor monitoring, but move top=quarantineand ultimatelyp=reject. Staying onp=noneindefinitely defeats the purpose. - Include the
ruatag for aggregate reports - this is how you catch authentication failures before they become delivery problems. - Set
pct=100(or omit it, which defaults to 100). Partial enforcement is a transitional state, not a destination.
Every CRM, email marketing platform, and support system that sends on your behalf creates a potential authentication gap. We've seen teams nail their primary domain's DMARC only to discover that their Zendesk instance, their HubSpot account, and three acquired company subdomains were all sending unauthenticated email. Audit everything.
Security Risks: When NOT to Whitelist an Email Sender
The Vendor Whitelisting Trap
Here's a pattern that plays out constantly in IT departments: a vendor's emails start hitting spam. Instead of checking their own authentication, they send your IT team a message asking you to approve 11 email addresses. You check their records - SPF fails, DKIM is missing, DMARC is misconfigured. Everything screams "I'm a spoof."
The correct response: "No. Fix your authentication."
The reason is simple. If you add a sender to your safe list when they fail authentication checks, and that sender's account gets compromised, the attacker inherits your trust. Phishing emails, malware attachments, BEC scams - all delivered straight to your users' inboxes, bypassing every filter you've configured.
Barracuda users have reported that user-level safe sender rules override all checks except virus detection. That means if a user adds a sender policy for a domain, emails that fail SPF are still delivered. The security implications are enormous.
90% of successful cyberattacks start with a phishing email. Hornetsecurity's 2026 report shows a 131% year-over-year increase in emails containing malware. The attack surface is growing, and blanket allowlisting expands it.
Compromised Accounts and the Emotet Lesson
The Emotet malware campaign demonstrated exactly why this approach is dangerous at scale. Emotet compromised legitimate email accounts and injected malicious messages into ongoing email threads. The recipients had already been communicating with the sender - many had added them to their safe senders. The malware spread through phishing links and Office documents, riding the trust those allowlists had created.
The numbers behind this: 37 billion data records were leaked in 2020 alone, and 32% were email addresses. That's roughly 12 billion compromised email addresses from a single year - the cumulative total is far worse. Any one of them could be a trusted sender in your organization.
The Zero Trust Alternative
The modern approach is zero trust email security: never assume a sender is safe, even internal ones. Require continual authentication. Monitor threats pre- and post-delivery. Pair email security with MFA - Microsoft reports it prevents 99% of credential-based attacks.
This doesn't mean you can never allowlist a sender. It means the practice should be:
- Temporary, not permanent
- Scoped to specific addresses, not entire domains
- Conditional on authentication passing (add
dmarc=passrequirements to mail flow rules) - Documented with an expiration date and a business justification
If you must allowlist a sender with authentication issues, consider appending a visible warning banner to those messages - a compromise that maintains delivery while keeping users alert.
If your organization doesn't have a formal allowlisting governance policy, you're not alone - most SMBs don't. But if you're handling sensitive data, customer PII, or financial transactions, this is a gap worth closing.
For Email Marketers: How to Reach the Inbox (Not Just Ask for It)
Why Your Emails Land in Spam
Picture this: you send a 10,000-person campaign. Your open rate comes back at 8%. You dig into the data and discover that 24% of your Outlook recipients never saw the email - it went straight to spam or got dropped entirely. Your Gmail numbers look better, but 6.8% of those went to spam too.
The instinct is to ask subscribers to add you to their safe senders. And that helps - for the subscribers who actually do it. But roughly 30-40% of email marketers still include these requests in their onboarding sequences, and the conversion rate is abysmal. Most subscribers don't know what it means, don't care enough, or forget immediately.
The three things that actually determine inbox placement:
- Authentication - SPF, DKIM, DMARC properly configured
- List hygiene - no invalid addresses, spam traps, or honeypots
- Engagement - open rates, click rates, spam complaint rates
Asking recipients to add you to their contacts is a distant fourth.
Gmail's spam complaint threshold is 0.3%. Cross that line, and your inbox placement drops fast. Microsoft's filters are even more aggressive - they use user feedback signals like "Sweep" and "Focused Inbox" to auto-redirect low-engagement senders.
The Safe Sender Request (How and When to Ask)
If you're going to ask subscribers to approve your address, HubSpot's recommendation is the right one: include the request in your welcome email, when engagement is highest. Don't bury it - make it a clear, simple ask with provider-specific instructions.
Here's a template you can copy and paste into your welcome email:
To make sure you get every issue of [newsletter name], add [your-email@domain.com] to your contacts. Here's how:
- Gmail: Search for our email → click the three dots → "Filter messages like these" → "Never send to Spam"
- Outlook: Settings → Junk email → Safe senders → Add [your-email@domain.com]
- Yahoo: Open our email → click the three dots → "Filter emails like this" → Move to Inbox
- Apple Mail: Add [your-email@domain.com] to your Contacts
But don't rely on this. It's a supplement, not a solution.
Clean Your List Before You Send
Here's the root cause most marketers miss: bad data destroys sender reputation, which causes filtering, which is why recipients need to approve you in the first place. It's a vicious cycle.
Invalid email addresses bounce. Spam traps flag your domain. Honeypots get you blocklisted. Every one of these events compounds over time, and progressively your sender reputation degrades until even legitimate subscribers stop seeing your emails.
The fix is verification before you send. Prospeo's email verification catches spam traps, honeypots, and invalid addresses at 98% accuracy - removing the bad data that damages your reputation in the first place. The free tier covers 75 verifications per month, enough to validate the process before scaling. For larger lists, it runs on credits at roughly $0.01 per email.
This isn't about replacing authentication or engagement strategy. It's about removing the data quality problem that undermines everything else. If you're sending to a list you haven't verified in the last 90 days, you're gambling with your domain reputation every time you hit send.

You just read 2,000 words on rescuing emails from spam. Here's how to avoid the problem entirely: send to verified addresses. Prospeo verifies 143M+ emails with catch-all handling, spam-trap removal, and honeypot filtering. Teams using Prospeo see bounce rates under 4%.
Bounce rates drop when your data is verified every 7 days.
FAQ
What does it mean to whitelist an email?
It means marking a sender as trusted so their messages bypass spam filters and land in your inbox. Every major provider supports it through safe sender lists, contact additions, or filter rules. It only affects your individual mailbox - not anyone else's.
Is whitelisting an email safe?
Adding a sender with proper SPF/DKIM/DMARC authentication is low-risk. Adding a sender that fails authentication is dangerous - if that account gets compromised, phishing emails bypass your filters entirely. Always verify a sender's authentication status before approving them.
How do I stop emails going to spam without whitelisting?
If you're the sender: implement SPF, DKIM, and DMARC authentication, keep spam complaint rates below 0.3%, and verify your list before sending. Tools like Prospeo remove invalid addresses, spam traps, and honeypots at 98% accuracy, protecting your domain reputation at the source.
What's the difference between whitelisting and allowlisting?
They're identical in function. "Allowlist" is the newer, inclusive term adopted by Google, Apple, and many security vendors. Most email interfaces still use "whitelist" in their UI. Both let you designate trusted senders whose messages skip junk filtering.
Does adding a sender to contacts count as whitelisting?
Yes, partially. Gmail, Outlook, Yahoo, and Apple Mail all give preferential filtering treatment to senders in your contacts. It's not as strong as creating a dedicated filter rule, but it's the fastest single step you can take - and it works on both desktop and mobile.