Account Identification: What It Means in B2B, Banking, and Accounting
"Account identification" means completely different things depending on who's asking. A VP of Marketing wants to know which companies are visiting their website. A compliance officer needs to verify a customer's identity before opening a bank account. An accounting student is trying to classify transactions into the right ledger categories.
All three are Googling the same term. None of them want the same answer.
What You Need (Quick Version)
B2B sales or marketing? You need website visitor identification paired with contact data. Start with a budget tool like RB2B or Leadfeeder to see which companies hit your site, then enrich those accounts with verified emails and direct dials for the actual decision-makers. Jump to the B2B section below.
Banking or compliance? You need KYC and Customer Identification Program (CIP) guidance - including the June 2025 TIN exemption that's the first major CIP update in over two decades. Jump to the banking section.
Accounting? You need the classification framework - Traditional (British) vs. Modern (American) account types. Jump to the accounting section.
The digital identity solutions market hit $47.36 billion in 2025 and is projected to reach $231 billion by 2035, with growth driven by all three use cases simultaneously. The identity verification segment alone sits at $14.1 billion in 2026. Most guides cover one of these meanings and ignore the rest. This one covers all three, with tools, pricing, regulatory updates, and practical frameworks for each.
B2B Account Identification - Turning Anonymous Traffic into Pipeline
98% of B2B website visitors leave without filling out a form, requesting a demo, or doing anything that identifies them. That's not a marketing failure. It's just how B2B buying works. Prospects research anonymously across dozens of vendors before ever raising their hand.
B2B account identification is the practice of figuring out which companies (and sometimes which individuals) are visiting your site, even when they don't convert. Companies implementing visitor identification see a 10-30% increase in qualified pipeline and 2-3x improvement in outbound response rates compared to purely cold outreach. The logic is simple: someone researching your category is warmer than a random name on a list.
But the gap between what vendors promise and what you'll actually get is enormous.
How B2B Visitor Identification Works
There are two fundamental approaches, and the distinction matters more than most vendors want you to know.
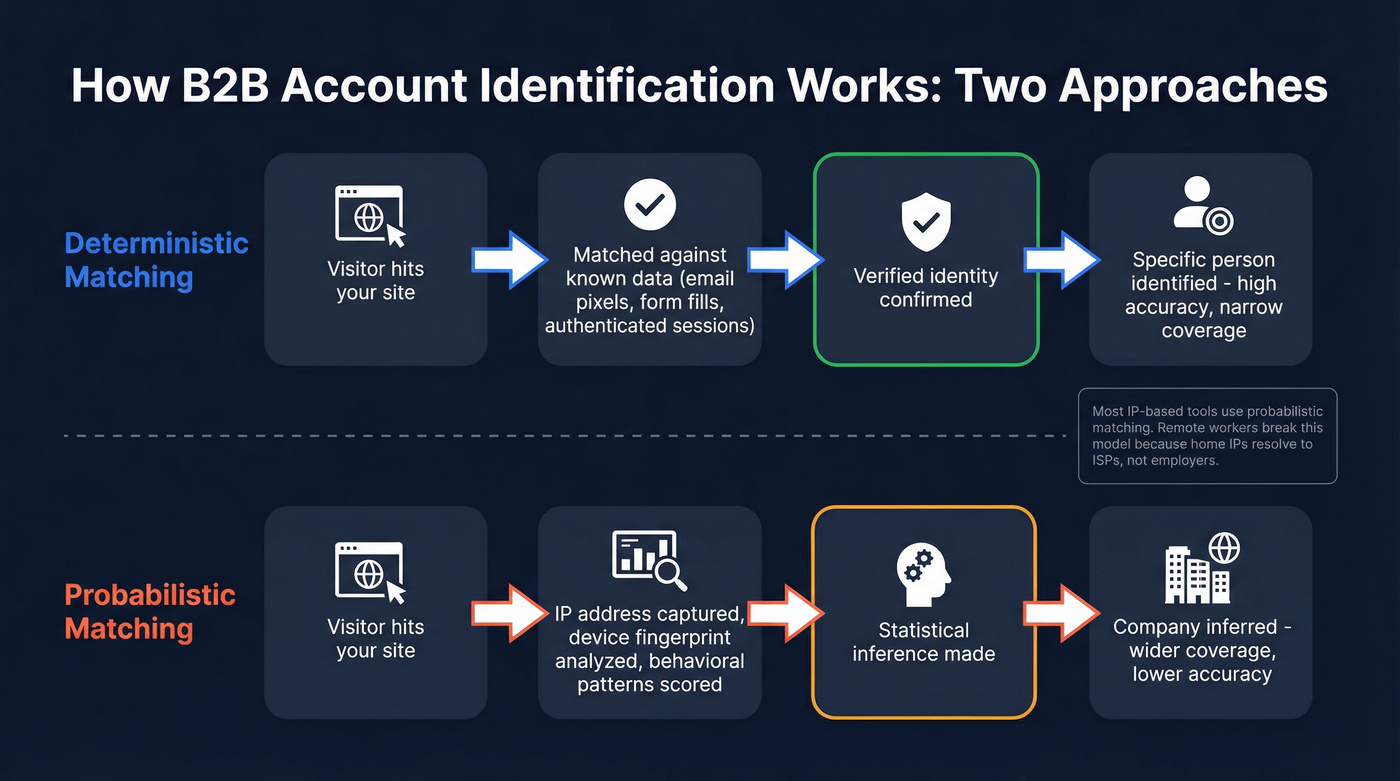
Deterministic matching uses verified first-party data signals - things like email pixels, form fills, or authenticated sessions - to identify a specific person. When it works, it's accurate. But it only works when the visitor has previously interacted with your ecosystem in some identifiable way.
Probabilistic matching uses statistical models built on IP addresses, device fingerprints, and behavioral patterns to infer who's visiting. It casts a wider net but trades accuracy for coverage. Most IP-based visitor identification tools fall into this category.
The IP-based approach works like this: your website captures the visitor's IP address, the tool maps that IP to a company using a reverse-IP database, and you get a company name (and sometimes firmographic data like industry, size, and location). Some tools layer on person-level identification by cross-referencing behavioral signals with contact databases.
The catch? IP-to-company mapping was designed for a world where employees worked in offices. That world doesn't exist anymore.
Realistic Match Rates (Not What Vendors Tell You)
Anyone promising 80%+ contact-level identification is counting company matches, not individual people. Accuracy varies wildly based on your traffic composition, and the real numbers are far more modest than vendor marketing suggests.
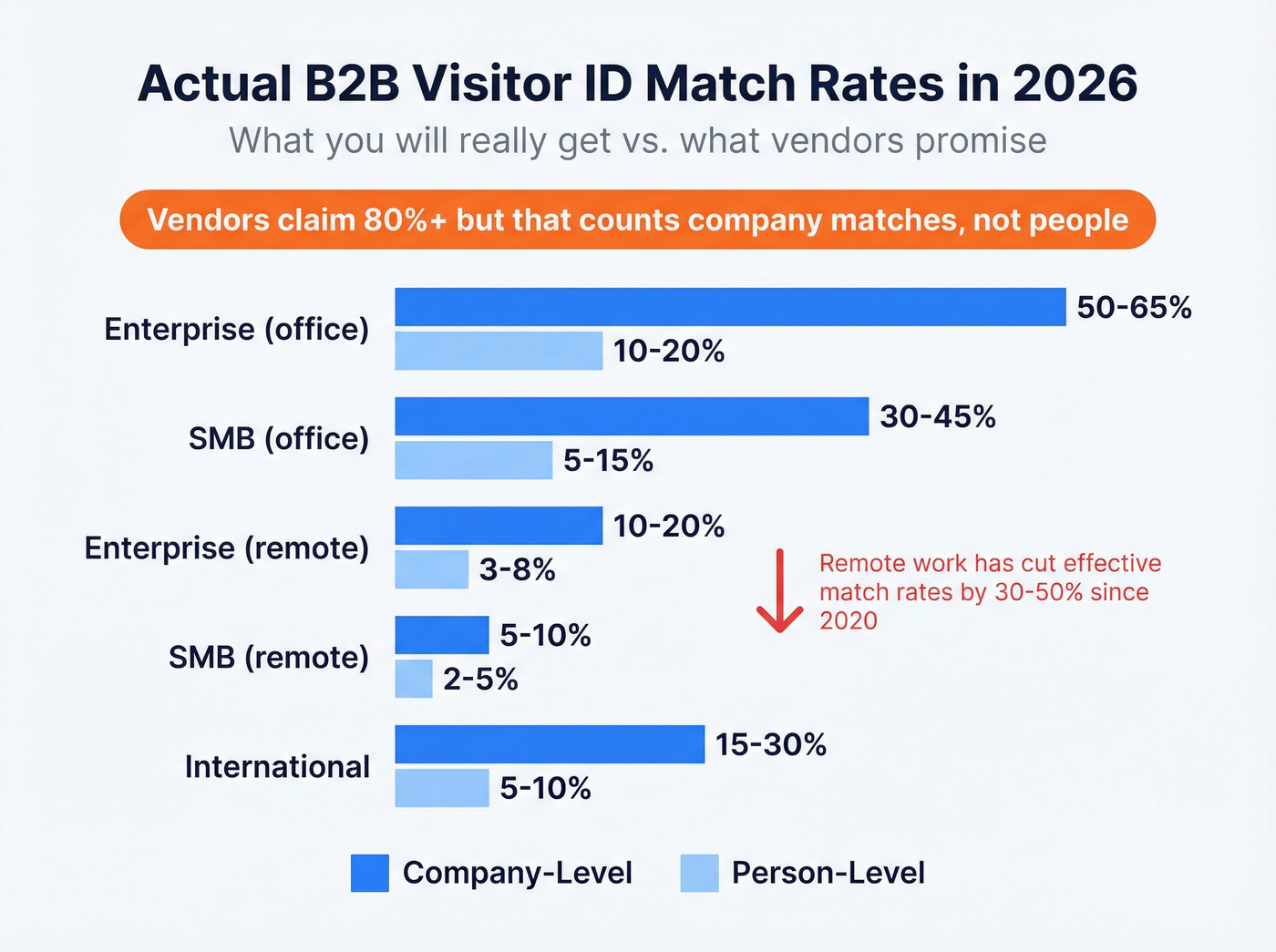
Here's what match rates actually look like in 2026:
| Traffic Type | Company-Level | Person-Level |
|---|---|---|
| Enterprise (office) | 50-65% | 10-20% |
| SMB (office) | 30-45% | 5-15% |
| Enterprise (remote) | 10-20% | 3-8% |
| SMB (remote) | 5-10% | 2-5% |
| International | 15-30% | 5-10% |
The remote work problem is the elephant in the room. Over 60% of knowledge workers are remote or hybrid in 2026. When someone works from home, their IP address resolves to Comcast or Verizon - not their employer. That single factor has cut effective match rates by 30-50% compared to pre-2020 levels.
We've seen teams buy a visitor identification tool expecting to identify half their traffic, only to discover their actual match rate is 12% because their audience skews toward remote-first startups. The #1 complaint on Reddit about these tools? Low match rates versus marketing claims. One user in r/b2bmarketing noted that most alternatives either have low identification rates or are too expensive because they bundle unnecessary features to justify $5-10K pricing.
If your site traffic is primarily SMB and remote, expect company-level identification in the 15-25% range. Plan accordingly.
B2B Visitor Identification Tools and Pricing
The market splits into three tiers: budget tools for testing the concept, mid-market tools with richer integrations, and enterprise ABM platforms where visitor ID is one feature among many.
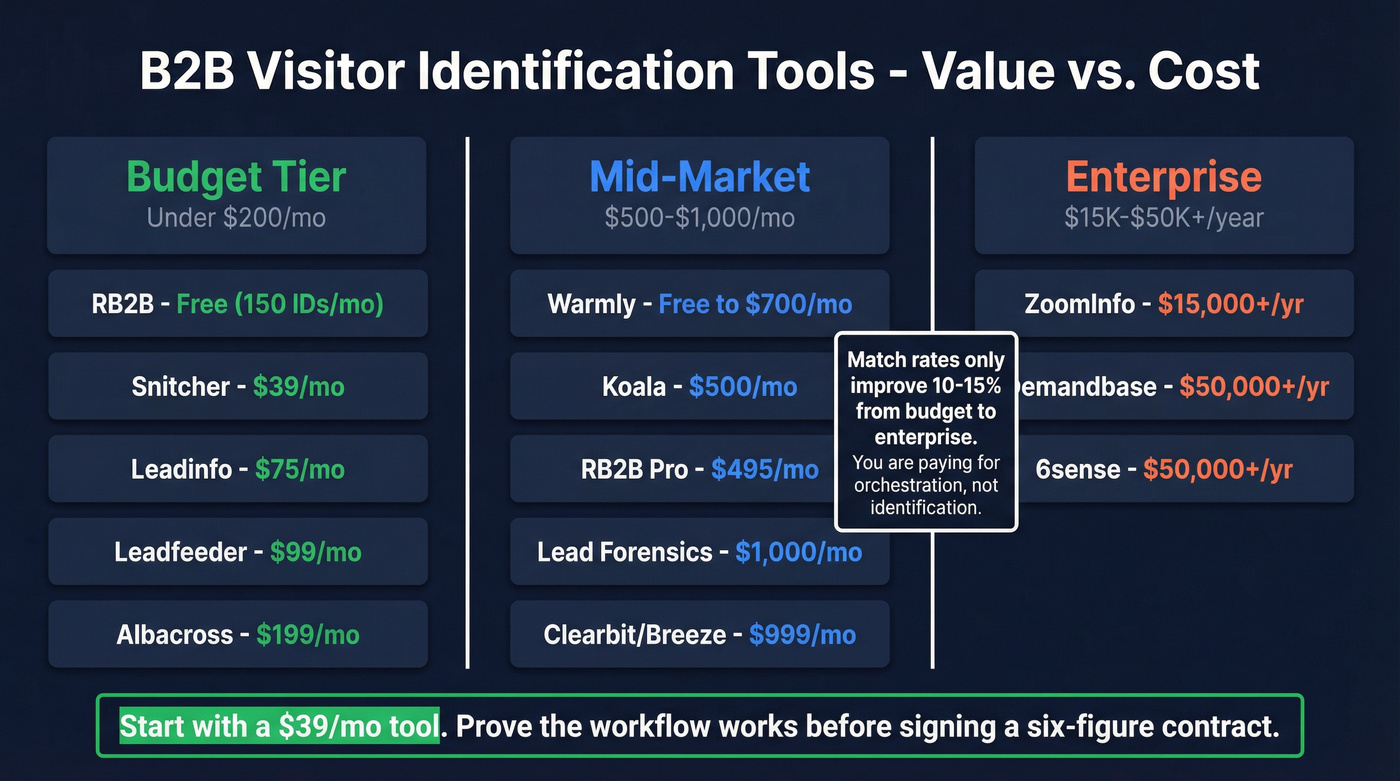
Budget Tier (Under $200/month)
| Tool | Match Rate (Co / Person) | Starting Price | Best For |
|---|---|---|---|
| RB2B | 20-30% / 5-15% | Free (150 IDs/mo) | Budget testing |
| Snitcher | 20-30% / N/A | ~$39/mo | Lean teams |
| Leadinfo | 35-40% / N/A | ~$75/mo | EU traffic |
| Leadfeeder | 10-15% / N/A | ~$99/mo (free tier) | GA integration |
| Albacross | 25-35% / N/A | ~$199/mo | Scandinavian focus |
Mid-Market & Enterprise
| Tool | Match Rate (Co / Person) | Starting Price | Best For |
|---|---|---|---|
| Warmly | 15-25% / 10-20% | Free / $700/mo | Mid-market |
| Koala | 20-25% / 5-15% | $500/mo | SaaS companies |
| RB2B Pro | 30-40% / 10-20% | $495/mo | US person-level |
| Lead Forensics | 20-25% / N/A | ~$1,000/mo | Enterprise UK |
| Clearbit/Breeze | 15-20% / 5-10% | ~$999/mo | HubSpot users |
| ZoomInfo | 25-35% / 10-20% | $15,000+/yr | Full-stack GTM |
| Demandbase | 25-40% / 10-15% | $50,000+/yr | Enterprise ABM |
| 6sense | 25-40% / 10-15% | $50,000+/yr | Enterprise ABM |
A few things jump out. The gap between budget and enterprise pricing is massive - $39/month to $50,000+/year - but the gap in match rates isn't proportional. You're paying for integrations, intent data, and orchestration features, not dramatically better identification.
European tools like Leadinfo and Albacross consistently outperform US-built tools on EU traffic, scoring 35-40% match rates in Europe versus 15-20% for American alternatives. If your traffic is primarily European, start there.
Here's the thing: most B2B teams don't need a $50K ABM platform for this. A $39/month Snitcher account paired with a good contact data tool will get you 80% of the value at 1% of the cost. The enterprise platforms earn their keep through orchestration, not identification. Don't sign a six-figure Demandbase contract until you've proven the workflow works at the budget tier.
If you're building this into your broader B2B sales stack, start lean and add orchestration only after the workflow is proven.
GDPR, Privacy, and Cookieless Tracking
The legal picture is more nuanced than "IP tracking = GDPR violation."
Company-level visitor identification - where you identify the organization, not the individual - generally falls under GDPR's Article 6(1)(f) legitimate interest provision. Company data like name, registration number, sector, and employee count aren't traceable to an individual and don't qualify as personal data.
The complication is IP addresses themselves. The CJEU's Breyer ruling (C-582/14) established that dynamic IP addresses can constitute personal data if the website operator has legal means to obtain identifying details from the ISP. Static IPs unambiguously qualify as personal data under GDPR.
Cookieless tracking technology sidesteps much of this by using only network metadata and ASN mapping - no fingerprinting, no tracking cookies, no personal profiles. This approach bypasses the ePrivacy Directive entirely, meaning no cookie consent banners are required. European-hosted tools also tend to outperform on EU traffic identification rates, which is another reason to consider them if your audience is primarily in the EU.
Practical compliance requirements: disclose visitor identification in your privacy policy, provide an opt-out option, and limit data processing to stated purposes. For the outbound side, see GDPR for Sales and Marketing.
Intent Data - Identifying Accounts Before They Visit
Visitor identification has a blind spot: it only catches accounts that have already found your website.
Intent data catches accounts while they're still researching the broader category. There are three types. First-party intent comes from your own properties - website behavior, email engagement, demo requests. It's the clearest buying signal but the narrowest. Third-party intent is aggregated from across the web, tracking which companies are researching topics relevant to your product. Second-party intent comes from partners - review sites, co-hosted events, industry communities.
Four in ten B2B marketing teams say their most effective recent shift was moving from broad platforms to niche, ABM-style communities. That tracks: intent data is the mechanism that makes ABM targeting precise rather than aspirational.
Most ABM platforms like Demandbase and 6sense now include intent data as a table-stakes feature, but dedicated intent providers offer broader topic coverage and deeper signal fidelity. For teams that want intent signals without committing to a six-figure ABM platform, tools like Prospeo layer intent data covering 15,000 topics directly into a B2B database - so you can filter by which accounts are actively researching topics related to your solution before they ever hit your website. If you're new to this category, start with intent signals and then move to accounts in market intent data.
How to Track Buyers Across Companies
Here's where 90% of visitor identification investments die.
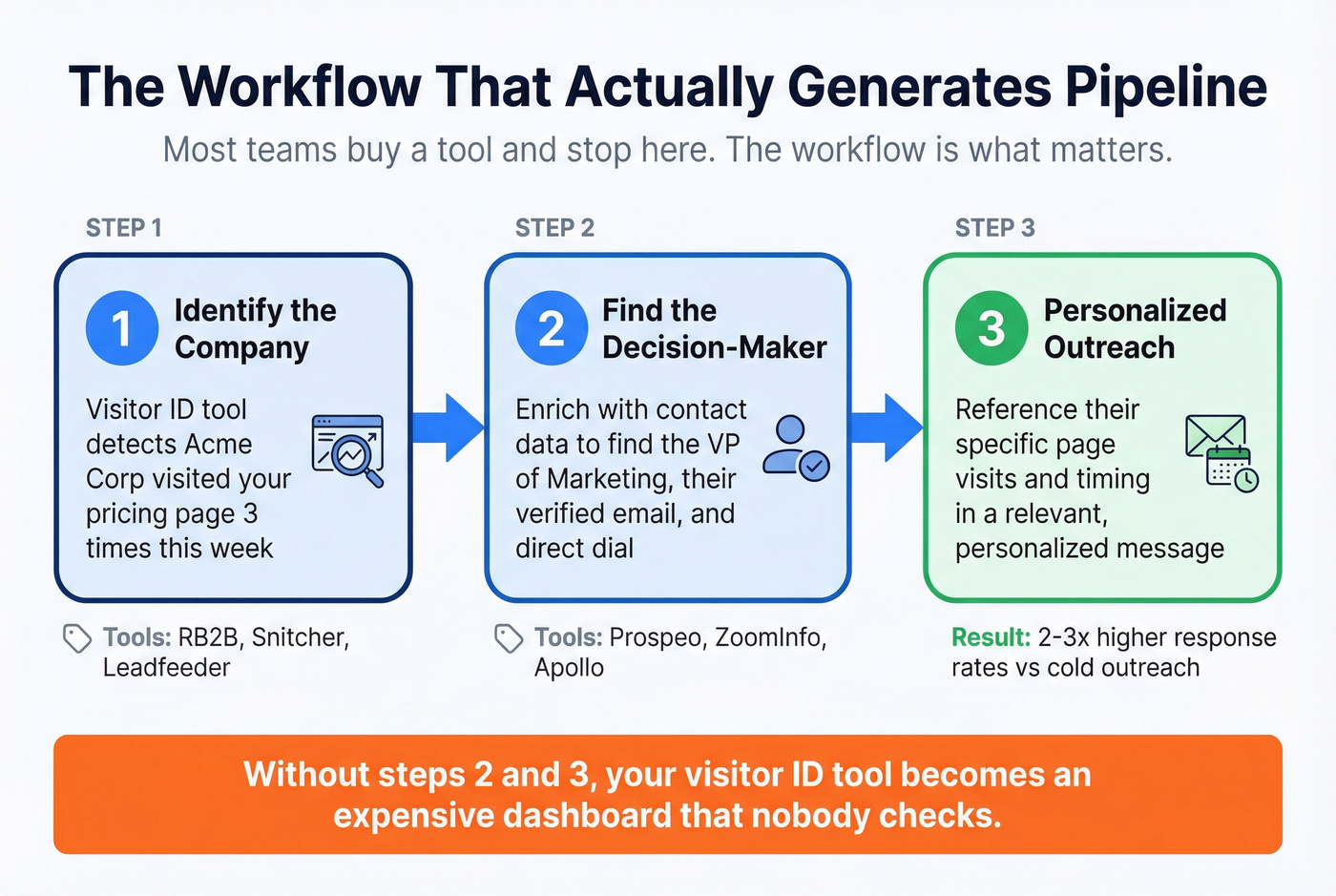
A team buys a tool, identifies companies visiting their site, and then... the data sits in a dashboard. Nobody has time to manually research each company, find the right decision-maker, track down a verified email, and write a personalized outreach sequence.
In our experience, this pattern plays out constantly: a revenue leader gets excited about identifying anonymous visitors, buys a tool, and three months later the dashboard is collecting dust because nobody built the bridge between "company name" and "booked meeting." The tool isn't the problem. The workflow is.
The ability to track buyers across companies - connecting anonymous website visits to real decision-makers at those organizations - is what separates teams that generate pipeline from teams that generate dashboards. The workflow that actually works has three steps:
Step 1: Identify the company. Your visitor ID tool tells you Acme Corp visited your pricing page three times this week. Good signal.
Step 2: Find the decision-makers. This is the gap. Knowing "Acme Corp" visited means nothing if you can't reach the VP of Engineering who's actually evaluating solutions. You need verified contact data - emails and direct dials - for the right people at that company. (More on this in key decision makers.)
Step 3: Outreach within 48 hours. Intent decays fast. A company researching your category today might sign with a competitor next week. Speed matters more than perfection. Use a repeatable B2B cold email sequence and measure response by cohort.
Prospeo is built for step two. Search by company name, filter by job title, department, and seniority, and pull verified emails and direct dials in seconds. The database covers 300M+ professional profiles with 98% email accuracy and 125M+ verified mobile numbers. Every record refreshes on a 7-day cycle - not the 4-6 week industry average - so you're not reaching out to someone who changed jobs last month. At roughly $0.01 per email, it's a fraction of what ZoomInfo charges for the same data.
The math is simple: if your visitor ID tool identifies 50 companies per week and you can convert even 5% of those into meetings, that's ~10 new qualified conversations per month from traffic you were already getting. But only if you can bridge the gap between "company name" and "booked meeting."

Visitor identification tools tell you which companies hit your site. Prospeo tells you who to call. Enrich identified accounts with 98% accurate emails and verified mobile numbers from 300M+ profiles - at $0.01 per email.
Turn anonymous website visitors into booked meetings, not just company names.

Most visitor ID tools stop at the company name. Your pipeline doesn't grow until you reach the actual buyer. Prospeo's 125M+ verified mobiles hit a 30% pickup rate - that's 3x what ZoomInfo delivers - with data refreshed every 7 days, not 6 weeks.
Stop paying $50K for ABM platforms when $0.01 per lead gets you further.
Banking and Financial Account Identification
Account identification in banking is a completely different discipline - regulatory, compliance-driven, and increasingly shaped by AI-powered fraud.
Account Numbers, Routing Numbers, and Financial Identifiers
At the most basic level, a financial account identifier is the unique string of numbers that distinguishes your account from every other account at a financial institution. Most US bank account numbers run 8-12 digits, though the range spans 5-17 depending on the institution. These identifiers originated in the late 1960s when computers first entered banking operations.
Routing numbers are the other half of the equation. Every US financial institution has a 9-digit routing transit number (RTN), with the first two digits indicating the Federal Reserve District (01 for Boston through 12 for San Francisco). There's a distinction most people miss: ABA routing numbers are used for paper checks, while ACH routing numbers handle electronic transfers. They're often the same number, but not always.
KYC and Customer Identification Programs (CIP)
The Customer Identification Program (CIP) rule was introduced in 2003 under the USA PATRIOT Act, requiring banks to develop procedures for verifying the identity of anyone opening an account. The rule mandates four elements: collecting identifying information (name, date of birth, address, identification number), verifying that information, maintaining records, and checking against government lists of known or suspected terrorists.
The standard isn't absolute certainty - it's "reasonable belief" that the bank knows the customer's true identity. That distinction matters because it gives institutions flexibility in how they verify, while still holding them accountable for due diligence.
CIP requirements also apply to non-U.S. citizens and business entities. Banks must collect a passport number or government-issued ID for foreign nationals, and organizational documents (articles of incorporation, partnership agreements) for companies, partnerships, and trusts.
For over two decades, the CIP rule remained essentially unchanged. Then in June 2025, regulators approved the first major modernization: an amendment allowing banks to collect Taxpayer Identification Numbers (TINs) from reliable third-party sources rather than directly from customers. This mirrors an existing carve-out for credit card issuers and reflects a practical reality - consumer data breaches have made people increasingly reluctant to share SSNs during digital onboarding.
The exemption comes with conditions: the TIN must still be obtained before account opening, banks need risk-based written procedures, and the process must remain consistent with other CIP requirements.
Digital Identity Verification Methods
Modern identity verification goes far beyond checking a driver's license. Five core components make up today's IDV stack:
- Biometric verification - facial recognition, fingerprint scanning, liveness detection. OCR and pattern recognition extract data from ID documents, then biometrics confirm the person presenting the document is the person on it.
- Document forensics - AI algorithms check for tampering, inconsistencies, and forgery markers in submitted documents.
- Identity data verification - matching submitted information against government records, credit bureaus, and mobile operator databases.
- Electronic identities (eID) - digital IDs issued via apps or government platforms, increasingly common in the EU under eIDAS regulation.
- Phone and email verification - OTPs and secure links confirming control of a communication channel.
"Reusable identity" architectures are emerging - a single verified credential that ports across multiple platforms, reducing redundant verification. For financial institutions, reducing onboarding time from minutes to seconds can lower customer acquisition cost by up to 25%.
One real-world pain point that doesn't get enough attention: smaller banks and credit unions often aren't in major verification databases, creating gaps in automated workflows. One nonprofit processing 12,000 grants annually found that its verification tool couldn't cover many of their recipients' institutions, forcing manual fallbacks that defeated the purpose of automation. If your institution or your customers' institutions are smaller, budget for these edge cases.
Fraud Trends Reshaping Account Identification in 2026
The fraud picture has shifted dramatically.
Sophisticated fraud nearly tripled - jumping from 10% of all fraud attempts in 2024 to 28% in 2025, a 180% increase. The overall identity fraud rate stayed relatively stable (hovering around 2-2.6%), but the attacks that do happen are far harder to catch.
Deepfakes now rank among the top five fraud types. The UK government predicted 8 million deepfakes would be shared in 2025, up from 500,000 in 2023. The Arup incident - where an employee transferred $25 million after receiving deepfake video instructions from fake "senior management" - demonstrated that these aren't theoretical threats. They're happening right now.
Synthetic identities are another escalating problem. In 2025, synthetic identities appeared in 21% of first-party fraud cases detected. These are fabricated identities that combine real and fake information - a real SSN paired with a fake name and address - making them extraordinarily difficult to catch with traditional verification.
AI-generated fake documents are the newest vector. Two percent of all fake documents detected in 2025 were AI-generated using tools like ChatGPT, Grok, and Gemini. That number was zero just six months earlier. Underground markets on Telegram now sell "expat identity packages" - complete with SSNs, tax forms, and credit reports from former legal immigrants whose numbers remain active in US systems.
Check fraud remains stubbornly persistent: an estimated $21 billion in check fraud occurred in the Americas in 2023, with 62% of financial institutions reporting increased losses.
The response? Over 85% of financial firms are actively applying AI in fraud detection. Static visual-based detection methods for deepfakes are becoming less valuable as generative AI quality improves. Manual review and visual inspection alone are no longer sufficient.
2026 Regulatory Landscape
The regulatory environment is shifting toward risk-based flexibility rather than rigid prescriptive rules. Here's what matters right now.
CIP TIN Exemption (June 2025): Banks can now collect TINs from third-party sources. This is the first substantive CIP modernization since 2003 and signals a broader willingness to adapt regulations to digital-first banking.
FinCEN SAR Guidance (September-October 2025): Two important clarifications. First, voluntary cross-border information sharing between institutions is now explicitly permitted for suspicious activity reporting. Second, transactions near the $10,000 Currency Transaction Report threshold don't automatically require a Suspicious Activity Report - a common misconception that created unnecessary compliance burden. FinCEN also confirmed institutions aren't required to document no-file decisions.
Residential Real Estate AML Rule (December 2025): A nationwide standard replacing the patchwork of Geographic Targeting Orders, requiring AML reporting for residential real estate transactions.
Investment Adviser AML Rule: Originally set for January 2026, this has been postponed to January 2028. Investment advisers get a reprieve, but the rule is coming.
OCC Tailoring Initiative: The Office of the Comptroller of the Currency is actively working to tailor AML requirements to institution size, complexity, and risk profile. Smaller community banks won't face the same compliance burden as global systemically important institutions.
FinCEN Innovation Encouragement: FinCEN is explicitly encouraging responsible innovation, including AI and advanced analytics for AML compliance. AI tools can reduce false positives, accelerate investigations, and detect complex typologies - but human oversight remains required.
The overall direction is clear: regulators want effective, risk-based programs rather than checkbox compliance. That's good news for institutions willing to invest in modern technology, and a warning for those still running manual processes.
Account Identification in Accounting
In accounting, account identification means classifying transactions into the correct account categories. There are two systems, and which one you use depends largely on where you were trained.
The Traditional (British) approach uses three account types: Personal accounts (transactions with individuals, firms, or companies), Real accounts (permanent accounts that carry forward - assets like machinery, land, and cash), and Nominal accounts (temporary accounts closed at period-end - revenue, expenses, wages).
Personal accounts subdivide further: Natural persons (debtors, creditors, proprietors), Artificial persons (partnerships, companies, banks, government bodies), and Representative persons (outstanding, pre-paid, accrued, and unearned accounts). Real accounts split into Tangible (building, furniture, cash) and Intangible (goodwill, patents, copyrights, trademarks).
The Modern (American) approach uses five categories: Asset, Liability, Revenue, Expense, and Capital/Owner's Equity. It's now standard in most developed countries and maps directly to financial statements.
Here's how the two systems align:
| Example Account | Traditional | Modern | Statement |
|---|---|---|---|
| Plant & machinery | Real (Tangible) | Asset | Balance Sheet |
| Sales revenue | Nominal | Revenue | Income Statement |
| Owner's capital | Personal | Capital/Equity | Balance Sheet |
| Bank loan | Personal | Liability | Balance Sheet |
| Wages paid | Nominal | Expense | Income Statement |
| Goodwill | Real (Intangible) | Asset | Balance Sheet |
The practical difference: the Modern approach records expenses as they happen (reducing manipulation opportunities), while the Traditional approach recorded them when the product was sold. Modern accounting software has made the American system dominant - it maps cleanly to automated chart-of-accounts structures and financial reporting standards.
If you're setting up a new accounting system in 2026, use the Modern five-category approach. Skip the Traditional system unless your curriculum requires it.
Best Practices for Account Identification (Any Context)
Regardless of whether you're identifying website visitors, verifying bank customers, or classifying accounting transactions, certain principles apply universally.
For banking and KYC teams, the five most common verification mistakes are:
- Accepting expired or poor-quality identity documents
- Relying on a single data source instead of cross-referencing at least two independent sources
- Inconsistent application of verification procedures across staff members
- Inadequate record-keeping and documentation (records must be retained for 5+ years)
- Treating verification as a one-time checkbox rather than ongoing monitoring
These aren't theoretical risks. UK firms face penalties up to 10 million GBP for serious AML failures. Account takeover incidents have risen 24% year-over-year, and cybercriminals can purchase advanced identity theft tools for as little as $10/week.
The six-step verification process that works: collect initial information, validate documentation, conduct risk analysis, make a decision, implement ongoing monitoring, and maintain audit trails.
For B2B revenue teams, the framework is simpler but equally important: automate identification (don't rely on manual dashboard monitoring), enrich identified accounts with verified contact data, and operationalize outreach within 48 hours. Intent decays fast. If you're pressure-testing the workflow, use an ABM without expensive tools approach first.
Across all three contexts, the pattern is identical: identification without action is a cost center. The value comes from what happens next - blocking the fraudulent transaction, reaching the decision-maker within 48 hours, or classifying the transaction correctly so your P&L isn't fiction.
FAQ
What's the difference between account identification and identity verification?
Account identification determines which entity is involved in a transaction or interaction - it answers "who is this?" Identity verification confirms that entity is who they claim to be. Identification comes first; verification confirms it. In B2B, identification means figuring out which company visited your site. In banking, it means collecting customer information before opening an account.
How accurate are B2B website visitor identification tools?
Realistic company-level match rates run 20-40%, and person-level identification falls between 5-20%. Vendors claiming 70-80%+ are typically counting company matches or using inflated test conditions with office-heavy traffic. Remote work has cut effective rates significantly - if your audience skews remote-first, expect the lower end of these ranges.
Is IP-based visitor identification GDPR compliant?
Company-level identification using cookieless technology generally falls under legitimate interest (Article 6(1)(f)), but IP addresses can qualify as personal data under the CJEU Breyer ruling. Cookieless approaches using only network metadata and ASN mapping - without fingerprinting or tracking cookies - have the strongest compliance position. Disclose the practice in your privacy policy and provide an opt-out.
What changed in CIP rules for banks?
A June 2025 amendment now allows banks to collect TINs from reliable third-party sources rather than directly from customers - the first major CIP modernization since the original 2003 rule under the USA PATRIOT Act. Banks must still obtain the TIN before account opening and maintain risk-based written procedures. The change reduces onboarding friction for digital-first banking.
How do I turn identified accounts into sales meetings?
Use a contact data platform to find verified emails and direct dials for decision-makers at identified companies. Search by company name, filter by role and seniority, pull verified contacts, and launch outreach within 48 hours while intent is fresh. Prospeo's database covers 300M+ profiles at roughly $0.01 per email with 98% accuracy - the cost of bridging that gap is negligible compared to the pipeline value.