Blacklist Alert: How to Triage, Delist, and Prevent Email Blocks in 2026
A blacklist alert is either a harmless monitor ping - or the start of a very expensive week.
Treat it like an incident, but don't treat it like a disaster. Check bounce logs first, confirm whether a high-impact DNSBL/RBL is actually cited, then act. Checker screenshots aren't evidence.
What a "blacklist alert" actually means (and when it matters)
A blacklist alert means a monitor found your sending IP, domain, subdomain, or IPv6 on a DNSBL/RBL (a blocklist database of senders associated with spam, compromised hosts, open relays, or abusive patterns).
Here's the operational truth: blocklists don't "block email" by themselves. Mailbox providers and corporate gateways use some DNSBLs as signals inside their own filtering and reputation systems, and they ignore plenty of lists entirely.
And the ecosystem's huge. Braze has pointed out there are 100+ blocklists that matter to some degree, plus a long tail of tiny lists that barely influence delivery anywhere. That's why you get alerts for lists you've never heard of, run by someone you can't contact, that don't move inbox placement at all.
A listing matters when:
- Your bounces explicitly cite a list (Spamhaus, Barracuda, SpamCop, etc.)
- You see a sudden spike in 5xx rejections at major mailbox providers
- You're on a high-impact list (Spamhaus is the one to take personally)
It's noise when:
- The alert's from an obscure list and your delivery metrics are stable
- You can't find a single bounce that references the listing
What you need (quick version)
If I had to pick 3 things to do first...
- Find bounce evidence (not a screenshot of a checker).
- Check Spamhaus specifically (it's the fastest way to separate "real incident" from "monitor drama").
- Fix the root cause before delisting (delisting first is how you get relisted by lunch).
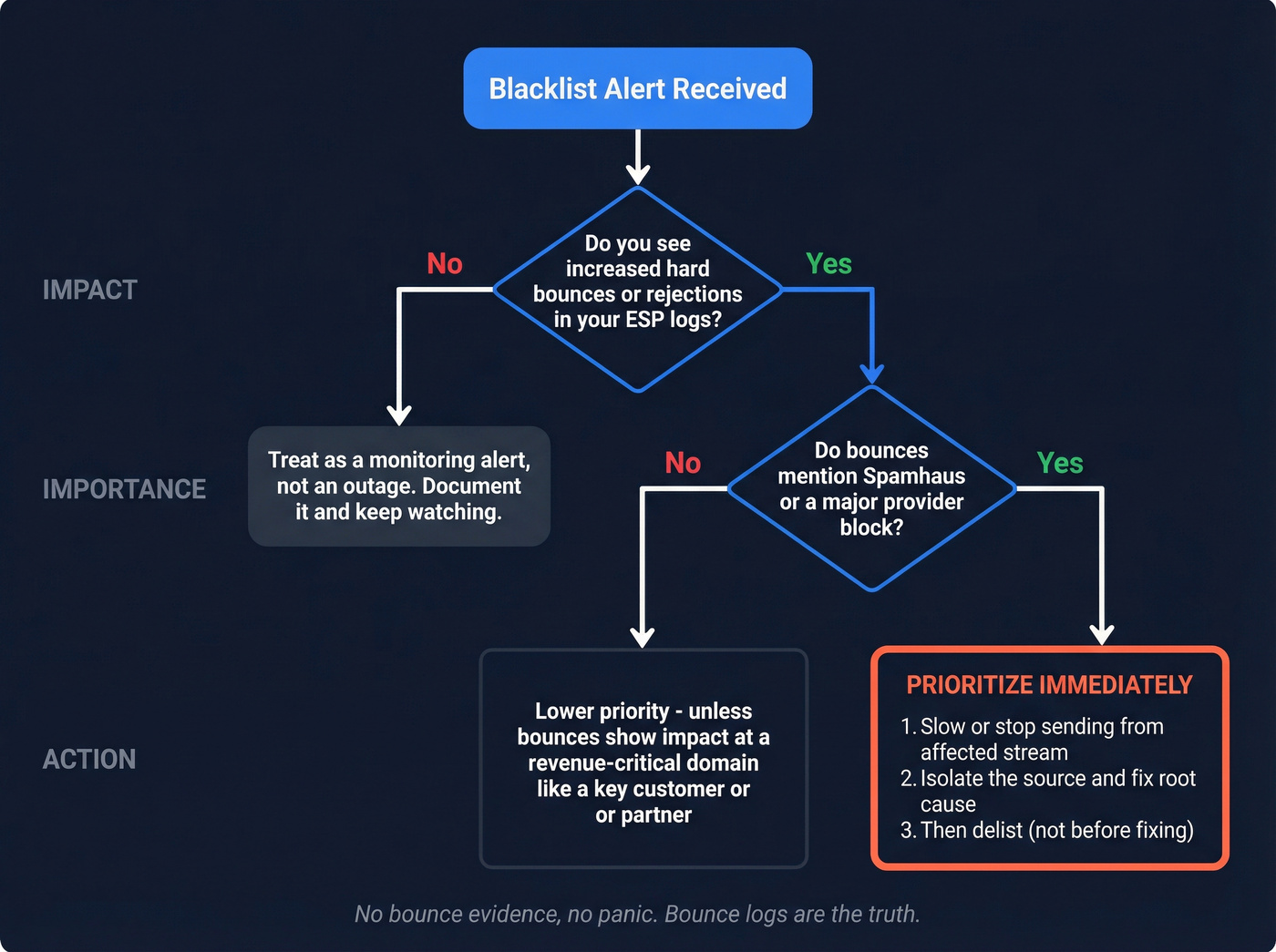
60-second decision tree (Impact -> Importance -> Action)
Impact
- Do you see increased hard bounces / rejections in your ESP logs?
- No -> treat as a monitoring alert, not an outage.
- Yes -> continue.
Importance
- Do bounces mention Spamhaus or a major provider block?
- Yes -> prioritize immediately.
- No -> lower priority unless bounces show impact at a revenue-critical domain (a key customer, a partner, or your biggest segment).
Action
- If it's a real block: slow/stop sending, isolate the source, fix auth/security/list hygiene, then delist.
- If it's noise: document it, keep monitoring, don't thrash your sending setup.
Confirm impact first after a blacklist alert (stop treating alerts like outages)
Use this rule: no bounce evidence, no panic.
An alert's a signal. Your bounce logs are the truth. Pull rejection reasons from your ESP (or MTA) and look for patterns like:
550 5.7.1 Service unavailable; Client host [x.x.x.x] blocked using ...554 5.7.1 Message rejected due to ...421 4.7.0 Temporary rate limit / reputation issue(not a DNSBL, but it's still impact)
If you run multiple streams (transactional + marketing, multiple subdomains, multiple IP pools), segment bounces by:
- sending domain/subdomain
- IP pool (dedicated vs shared)
- campaign or automation
- recipient domain (gmail.com vs outlook.com vs corporate domains)
This is where teams lose hours: they see "listed" and assume "blocked everywhere." In reality, you can be listed on a low-signal DNSBL and still deliver fine to Gmail and Microsoft, while one corporate gateway rejects you hard because it trusts that specific list.
I've seen this play out in a Monday-morning incident: a sales team paused every stream (including password resets) because a monitor flagged a tiny DNSBL. The only real problem was one customer running Barracuda, and the fix was isolating one IP pool and cleaning one automation. Two hours of chaos for a 10-minute log review.
Use this / skip this
Use the alert as a trigger if:
- bounces cite a specific DNSBL/RBL
- a key customer domain's rejecting you
- inbox placement drops at the same time
Skip the fire drill if:
- the alert's from an obscure list
- bounce rate and complaint rate are normal
- only one low-signal list's involved
Real talk: treat these pings like smoke alarms, not house fires.

Most blacklist incidents trace back to one root cause: bad email data. Stale addresses, spam traps, and honeypots wreck your sender reputation. Prospeo's 5-step verification with spam-trap removal and honeypot filtering eliminates the dirty data that gets you listed in the first place.
Stop delisting and start sending to emails that actually exist.
Noise vs signal triage (which alerts you can ignore)
Most blacklist tooling is designed to be "complete," not useful. That's how you end up with 14 red flags and zero actual delivery impact.
A practical heuristic that matches what we've tested in real incident reviews: niche lists flag brand-new domains/IPs constantly - sometimes just for existing, sharing an IP neighborhood, or tripping a simplistic rule. If bounces don't reference it, it's background noise.
The signal that matters
Spamhaus is the highest-impact listing for most teams. Braze has reported Spamhaus listings can cut deliveries by 60%+ in real-world scenarios. If you're listed there and you're sending meaningful volume, treat it as a real incident.
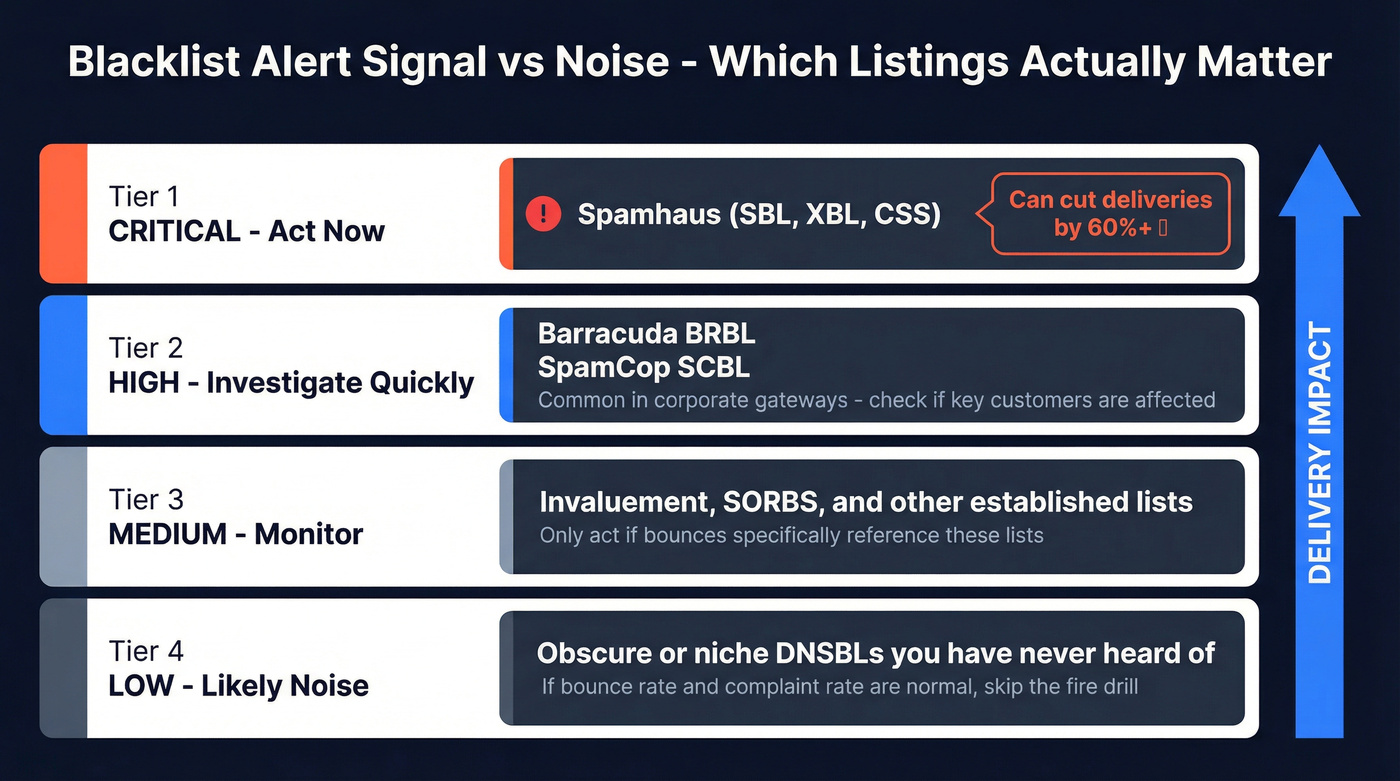
Also high-signal: bounces that mention Barracuda, SpamCop, or a specific enterprise gateway used by your customers.
Pros / cons of chasing every listing
Pros
- You catch real issues early (compromise, open relay, bad acquisition source)
- You build a clean incident trail for leadership
Cons
- You burn hours on lists nobody uses
- You make risky changes (DNS/auth/IP moves) without evidence
- You delist without fixing root cause and relist anyway
Here's the thing: the classic failure mode is someone dropping a checker screenshot in Slack, everyone panicking, and the "fix" turning into submitting random delist forms instead of reading bounce logs.
If you want a clean triage model, impact confirmed by bounces beats checker screenshots every time.
The first 30 minutes checklist (incident commander playbook)
Time-box this. The goal's to stop the bleeding, get clarity, and avoid making it worse.
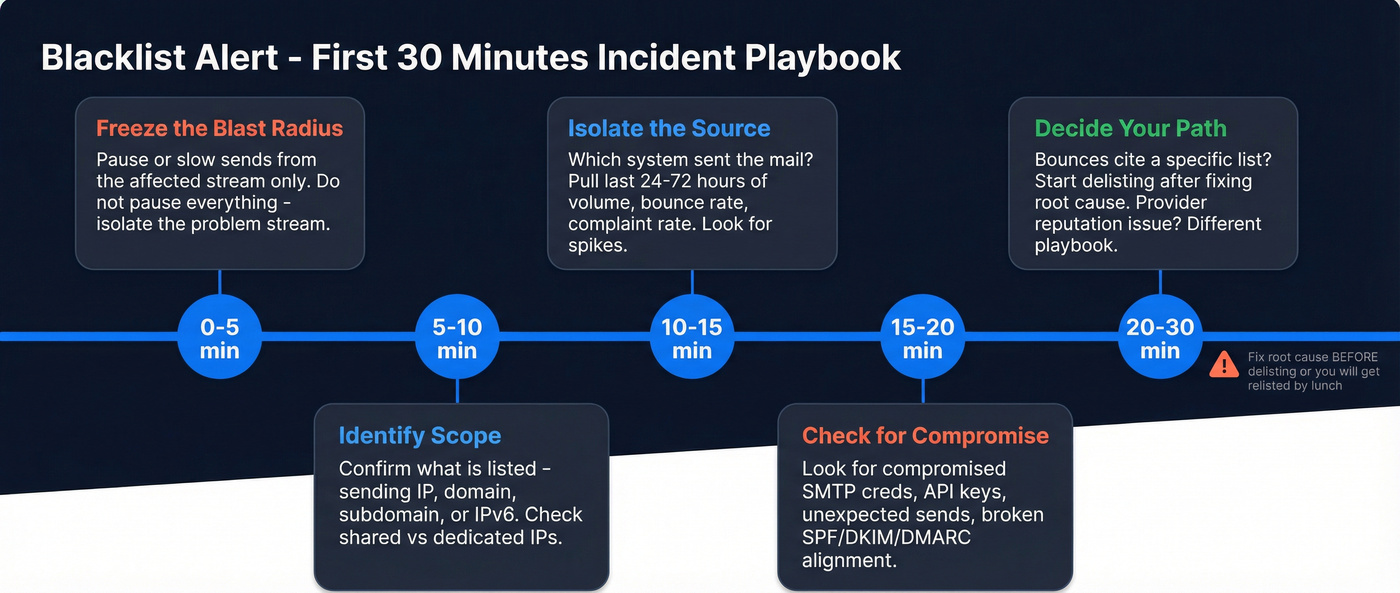
Minute 0-5: Freeze the blast radius
- Stop or slow sends from the affected stream (pause campaigns, reduce concurrency, lower daily caps).
- If you've got multiple subdomains/IP pools, don't pause everything - pause the one showing bounces.
One bad automation shouldn't take down your whole program.
Minute 5-10: Identify scope (IP vs domain vs IPv6)
- Confirm what's listed: sending IP, domain, subdomain, and IPv6.
- Check whether you're on shared IPs (ESP pool) or dedicated. Shared pool issues aren't "your fault," but they still hit your revenue.
Minute 10-15: Isolate the source
- Which system sent the mail?
- marketing platform
- sales sequencer
- transactional sender
- a server/app you forgot about
- Pull the last 24-72 hours of:
- send volume
- hard bounce rate
- complaint rate
- top recipient domains
- Look for spikes (new list upload, new automation, new integration).
Minute 15-20: Check compromise and obvious misconfig
Blacklist incidents are symptoms. The disease is usually one of these:
- compromised credentials (SMTP creds, API keys, admin logins)
- unexpected sends (password reset floods, weird timestamps, new IPs)
- broken SPF, DKIM, DMARC alignment for the domain/subdomain you actually send from
Minute 20-30: Decide your path
- If bounces cite a specific list: start the delisting playbook after you've stopped the cause.
- If bounces are provider-reputation based (Gmail/Microsoft): jump to the provider section below.
I've watched teams "clear" a listing while an infected host kept sending. They got relisted the same afternoon. It's maddening, and it's avoidable.
Delisting playbooks (Spamhaus, Barracuda, SpamCop, slow lists)
Delisting order matters most with Spamhaus, because the checker enforces a required removal sequence.

My default order when you've got multiple hits:
- Spamhaus (highest impact, clearest process)
- Barracuda (common in corporate gateways)
- SpamCop (often resolves quickly once behavior stops)
- Everything else (only if bounces prove impact)
Spamhaus (SBL, XBL, CSS, PBL) - prioritize this
Start here: https://check.spamhaus.org. It's the only place you should use for Spamhaus context and removals.
Spamhaus' checker enforces an order:
- SBL first -> then XBL/CSS -> then PBL
That ordering's a clue to the root cause.
Use this if: bounces mention Spamhaus, or you see broad delivery drops across multiple recipient domains. Skip this if: you only see a PBL status and you're not sending direct-to-MX.
Steps that work
- Look up your IP and domain in the Spamhaus check center.
- If you're on SBL: involve your ISP/hosting provider's abuse team and remove the spam source (compromise, list acquisition issue, open relay).
- If you're on XBL/CSS: treat it like a security incident. Clean the infected host or credential leak and stop the abusive traffic.
- Recheck after remediation. XBL-type issues often clear once the bad behavior stops and the system sees it.
Spamhaus XBL runs at huge scale - around 2M listings on average with 650k detections/day - so the winning move isn't "arguing." It's stopping the behavior.
For SBL background, Spamhaus' own overview is the cleanest reference: https://www.spamhaus.org/blocklists/spamhaus-blocklist/
Spamhaus PBL "listing" is often normal (common false alarm)
Myth: "We're on Spamhaus PBL, we're blacklisted."
Reality: PBL often means your IP space shouldn't send direct-to-MX. That's common for residential/dynamic ranges and plenty of general hosting ranges.
Quick fix for most teams: don't send direct-to-MX from that IP. Send through a proper relay and authenticate correctly.
- Enable SMTP AUTH
- Use ports 587 or 465 (not 25)
- If you request a single-IP PBL exclusion, DNS propagation's about 15 minutes
- Exclusions expire after 1 year
If you're using a mainstream ESP or sequencer with authenticated sending, PBL's rarely the real problem. Treat it as a clue, not a crisis.
Barracuda BRBL - delist steps + what to do if the form goes nowhere
Barracuda's process is simple: submit the removal request with complete info and a real remediation explanation. Valid requests are often processed within ~12 hours.
Steps
- Confirm the exact IP that's listed (Barracuda is IP-focused).
- Submit the Barracuda Central removal request with clear remediation details (compromise cleaned, risky list source removed, volume reduced, auth fixed).
- Wait the processing window, then retest.
If you get stuck in limbo, escalate through support channels. Once cleared, allow 2-24 hours for propagation.
Also: Barracuda notes duplicate requests can be ignored - submit once, submit cleanly.
SpamCop SCBL - mostly automatic (don't waste time begging)
SpamCop's blunt: you can't manually delist. If there are no new reports, you're auto-delisted after ~24 hours, and it can take up to 4 hours to propagate.
Your job is to stop whatever triggered the reports. Then wait.
When delisting is slow (Invaluement + similar)
Some lists move at the speed of geology. Delisting can take weeks even after you've fixed the issue.
What people do in the real world when revenue can't wait:
- move the affected stream to a clean sending IP/pool, and/or
- route temporarily through a reputable ESP while your infrastructure cools off
It's not elegant. It's effective.
When it's not a blacklist problem (Gmail + Microsoft reality)
A lot of incidents are provider reputation incidents. You're not blocked by a DNSBL - you're throttled, junked, or temp-failed by Gmail or Microsoft based on engagement, complaints, and sending patterns.
Hot take: if your outbound motion depends on blasting cold, unverified lists, you don't have a deliverability problem. You've got a go-to-market problem.
Microsoft (Outlook/Hotmail/Office 365 recipients): what to do next
Microsoft's operational path is:
- SNDS to monitor IP reputation and traffic
- JMRP to receive complaint feedback loops
- sender.office.com to request automated mitigation/review
Two gotchas worth knowing:
- SNDS/JMRP had an authentication change in November 2026 (approvals/denials require auth now).
- Automated report links expire after 30 days, so you need a real owner for this, not a "we'll check it later" task.
5-step Microsoft triage sequence
- Confirm the symptom in logs: are you seeing 4xx temp fails (throttling) or 5xx hard rejects?
- Set up/verify SNDS + JMRP for the sending IPs/domains involved (or confirm your ESP already handles this).
- Reduce risk immediately: pause cold segments, lower concurrency, and cut daily volume until rejections stabilize.
- Submit a mitigation request in sender.office.com with a specific remediation summary (what changed, what you fixed, what you're doing to prevent recurrence).
- Wait + retest: monitor rejection rates by recipient domain for 24-72 hours and only ramp volume when the curve's clearly improving.
What success looks like: temp fails drop first, then hard rejects, then junk placement improves over the next few days as engagement recovers.
Gmail: a 10-minute triage checklist that actually moves the needle
Google Postmaster Tools changed: the old Domain Reputation and IP Reputation dashboards were retired, so you don't get the same simple "green/yellow/red" view anymore. That makes it even more important to use first-party signals (bounces, complaints, engagement) and fix what Gmail punishes.
Targets that matter:
- Keep user-reported spam rate <0.3%
- Aim for <0.1% if you want breathing room
Gmail triage checklist (10 minutes)
- Confirm SPF/DKIM alignment for the exact domain/subdomain in the From header (misalignment is a self-own).
- Check complaint trend in your ESP: if complaints spiked, stop sending to the segment that caused it.
- Pause cold segments immediately (old lists, scraped lists, "we'll warm them up" lists).
- Reduce daily volume and concurrency for 48-72 hours. Gmail responds well to "we stopped doing the bad thing."
- Send only to engaged recipients for 7-14 days (recent opens/clicks/replies). That's the fastest way to rebuild reputation.
- Fix unsubscribe friction (one-click where possible; don't hide it). When people can't leave, they hit spam.
- Stop changing five variables at once. Pick two: audience + volume. Stabilize. Then iterate.
If Gmail's temp-failing you, the fix is almost never "find a delist form." It's send less, send cleaner, and send to people who actually want it.
Monitoring & checker tools (supporting cast, not the hero)
Tools help you check -> confirm impact -> monitor -> reduce noise. That's it. Don't buy a "deliverability suite" to avoid reading bounce logs.
If you're evaluating a paid option, think in terms of blacklist monitoring tools (for visibility and alert routing) rather than magical "fix deliverability" buttons.
Feature requirements worth demanding:
- Monitor IP + domain + IPv6
- Alert routing (email + Slack/webhook) and noise controls
- History/reporting (correlate to sends)
- Bulk/CIDR support if you manage multiple IPs
- "What changed?" context, not just red/green
Cadence matters: some monitors check daily, so a fixed listing can still show "active" until the next scan.
Comparison table - checkers vs monitors vs deliverability suites
| Tool | Best for | IP/Domain/IPv6 | Alerting | Scan cadence | Price anchor |
|---|---|---|---|---|---|
| MxToolbox | diagnostics + monitoring | Yes/Yes/Yes | On-demand + alerts | On-demand + scheduled | Delivery Center starts around ~$129/mo |
| DNSChecker | quick lookup | Yes/Yes/No | No | On-demand | Free |
| BlacklistAlert.org | fast spot-check | Yes/Yes/No | No | On-demand | Free |
| ZeroBounce | broad blacklist monitoring | Yes/Yes/Yes | Every 24h | Free tier available + paid plans (often ~$15-$99/mo depending on usage) | |
| BlacklistMaster | alerts + integrations | Yes/Yes/Yes | Slack/webhook | 20m-24h | ~$10-$50/mo |
| Uptime.com | simple daily checks | No/Yes/No | Email/SMS | Daily | ~$10-$30/mo |
| Validity Everest | enterprise deliverability suite | Yes/Yes/Yes | Advanced | Varies by plan | Not public (quote-based) |
Note: IPv6 support can vary by module and plan. Check the exact workflow you need before you commit.
Tool picks (short, practical)
MxToolbox - best "one tab" for incident response Use it when you want lookup + diagnostics + monitoring in one place. It also supports email-based checks, which is handy when you can't access the UI from a locked-down environment.
BlacklistMaster - best for Slack/webhook workflows (gotcha included) Great when you want alerts routed into ops channels and you care about scan frequency (20 minutes is a real advantage during an incident). Gotcha: faster scans and integrations push you toward the higher end of the ~$10-$50/month range.
ZeroBounce - best low-effort monitoring breadth Best when you want "set it and forget it" blacklist monitoring across lots of providers, including IPv6. Skip it if you only need a one-off lookup.
DNSChecker + BlacklistAlert.org - best for quick second opinions Use these for fast spot-checks. Don't use them as your source of truth for impact.
Uptime.com - best "daily pulse," not full coverage It checks against a set of well-known lists, which is fine for a daily alarm. It's too slow for active incidents.
Validity Everest - best when deliverability's a core competency If you send serious volume and need governance, seed testing, and deep analytics, Everest is a category leader. If you're an SMB trying to survive a single incident, it's overkill.
Further reading: WebSitePulse has a clear explainer on monitoring concepts: https://www.websitepulse.com/blog/what-is-email-blacklist-monitoring
How to prevent the next blacklist alert (policy, not vibes)
Most incidents are self-inflicted: bad data, sloppy authentication, and "send more" pressure. Fix the system and the alerts quiet down.
The prevention policy I'd actually enforce
Authentication & identity
- SPF/DKIM/DMARC must be present and aligned to the domain you send from.
- Separate streams: keep transactional and marketing/outbound on different subdomains and (ideally) different IP pools.
List hygiene & targeting
- Remove hard bounces immediately.
- Prune inactive recipients on a schedule (don't keep mailing ghosts).
- Don't "warm up" a domain with cold lists. Warm-up is for infrastructure, not for bad targeting.
Operational controls
- Ramp volume gradually on new domains/subdomains/IPs.
- Put rate limits on automations so one bug can't send 200k emails overnight.
- Make unsubscribe easy. If leaving's hard, spam complaints go up.
Common root causes -> the control that prevents them
Root cause: compromised SMTP/API credentials Control: rotate keys, enforce MFA/admin audit logs, and alert on unusual send spikes.
Root cause: new list upload tanks bounce + complaint rates Control: require verification before first send; cap first-day volume; send to engaged segments first.
Root cause: shared IP pool neighbor gets listed Control: move critical streams to a dedicated pool or a higher-trust pool; keep transactional isolated so it doesn't get dragged down.
Avoid this (it creates repeat incidents)
- "Spray and pray" cold sends to unverified addresses.
- Re-mailing old lists that haven't engaged in months.
- Paying to delist as your primary strategy.
Callout: UCEPROTECT is the pay-to-delist trap you should ignore (until bounces prove otherwise)
UCEPROTECT is notorious for noisy listings and pay-to-delist pressure. The big reason: Level 3 can list an entire ASN, which creates collateral damage and lots of false urgency.
Here's the rule: if your bounces don't cite it, don't care. Major mailbox providers don't base their core filtering decisions on pay-to-delist schemes, so you're better off spending that time on list quality, auth, and sane sending patterns.
Prospeo (Tier 1) - verified data to reduce bounces & reputation hits
Prospeo ("The B2B data platform built for accuracy") is the prevention lever we recommend when these incidents are really a symptom of bounce-heavy outbound. It's not a blacklist checker. It's how you stop feeding your sender reputation with hard bounces and spam-trap landmines in the first place.
Prospeo gives you 98% email accuracy with real-time verification and a 7-day refresh cycle (the industry average is 6 weeks). It includes 300M+ professional profiles, 143M+ verified emails, and 125M+ verified mobile numbers, and it's used by 15,000+ companies.
If your "blacklist alert" pattern keeps coming back, look hard at your inputs: where the addresses came from, how old they are, and whether you're verifying before you hit send. Fix that, and a lot of deliverability drama disappears.

You just spent hours triaging a blacklist alert. Now prevent the next one. Prospeo refreshes every record on a 7-day cycle - so you're never sending to addresses that decayed into spam traps weeks ago. Teams using Prospeo see bounce rates under 4%.
Replace your decayed lists with data that's never more than 7 days old.
A blacklist alert feels urgent because it's loud. The fix is usually quiet: confirm impact, fix the cause, delist in the right order, then tighten list quality and authentication so you don't end up here again.
FAQ
What's the difference between an IP blacklist alert and a domain blacklist alert?
An IP listing means a specific sending IP (or range) is flagged, which can affect any domain sending from it. A domain listing targets your domain/subdomain reputation and can follow you even if you change IPs. As a rule of thumb, IP issues are common on shared infrastructure, while domain issues reflect sustained complaint/bounce problems.
Should I stop sending email immediately after a blacklist alert?
Stop or slow sending only when logs show active rejections (4xx/5xx) or you're on a high-impact list like Spamhaus. Otherwise keep stable streams running and monitor. In practice, pausing one affected subdomain/IP pool for 24-72 hours is safer than "pause everything," especially if transactional mail's healthy.
How long does it take to get delisted from SpamCop, Barracuda, or Spamhaus?
SpamCop typically auto-delists after ~24 hours without new reports (allow up to 4 hours to propagate), while Barracuda often processes valid requests in ~12 hours (then 2-24 hours for propagation). Spamhaus timing varies by list type, and the check center enforces the order SBL -> XBL/CSS -> PBL, so remediation speed matters more than arguing.
What's a good free way to reduce blacklist alerts caused by bad contact data?
Use a verifier before you send and cap first-day volume to a small test batch (say, 200-500 emails) so bounces don't spike your reputation. Prospeo's free tier includes 75 email credits plus 100 Chrome extension credits per month with real-time verification, which is enough to validate a pilot list before scaling.
Do I need to delist if I'm listed?
Delist only after you've fixed the root cause, and only when bounces cite the list or you see measurable delivery impact at important recipient domains. If the listing isn't referenced in rejections and your metrics are stable, treat it as monitoring noise and focus on authentication, list hygiene, and controlled sending.