What Is Domain Reputation in 2026? (And Why You Can't Find a Single Score)
If you're asking what is domain reputation, you're usually feeling it: emails that used to land are suddenly in spam, getting throttled, or bouncing - while every dashboard insists things are "fine."
And in 2026, the annoying part is you can't just pull up one neat "domain reputation score" and call it a day.
Domain reputation is a system: signals in, outcomes out. If you manage the signals (complaints, bounces, authentication, consistency), inbox placement follows.
What you need (quick version)
Use this as your "don't overthink it" checklist:
- Stop hunting for one score - reputation is receiver-specific (Gmail != Yahoo != Microsoft).
- Keep spam complaints <0.1%; treat >=0.3% as an emergency line.
- Authenticate properly: SPF + DKIM + DMARC, and make sure domains align.
- Add List-Unsubscribe (one-click where supported) and honor opt-outs fast.
- Clean your list before you send - high bounces and traps torch trust quickly.
- Avoid sudden volume spikes; keep patterns stable week to week.
- Separate mail streams (newsletter vs product vs outbound) so one can't poison the other.
- Measure deliverability (inbox placement), not just delivery (server acceptance).
- Watch your links and tracking domains - phishy link patterns get punished.
Domain reputation has three meanings (here's the one you probably mean)
"Domain reputation" sounds like one thing. It isn't. It's three different concepts that got mashed together by marketing and sloppy terminology.
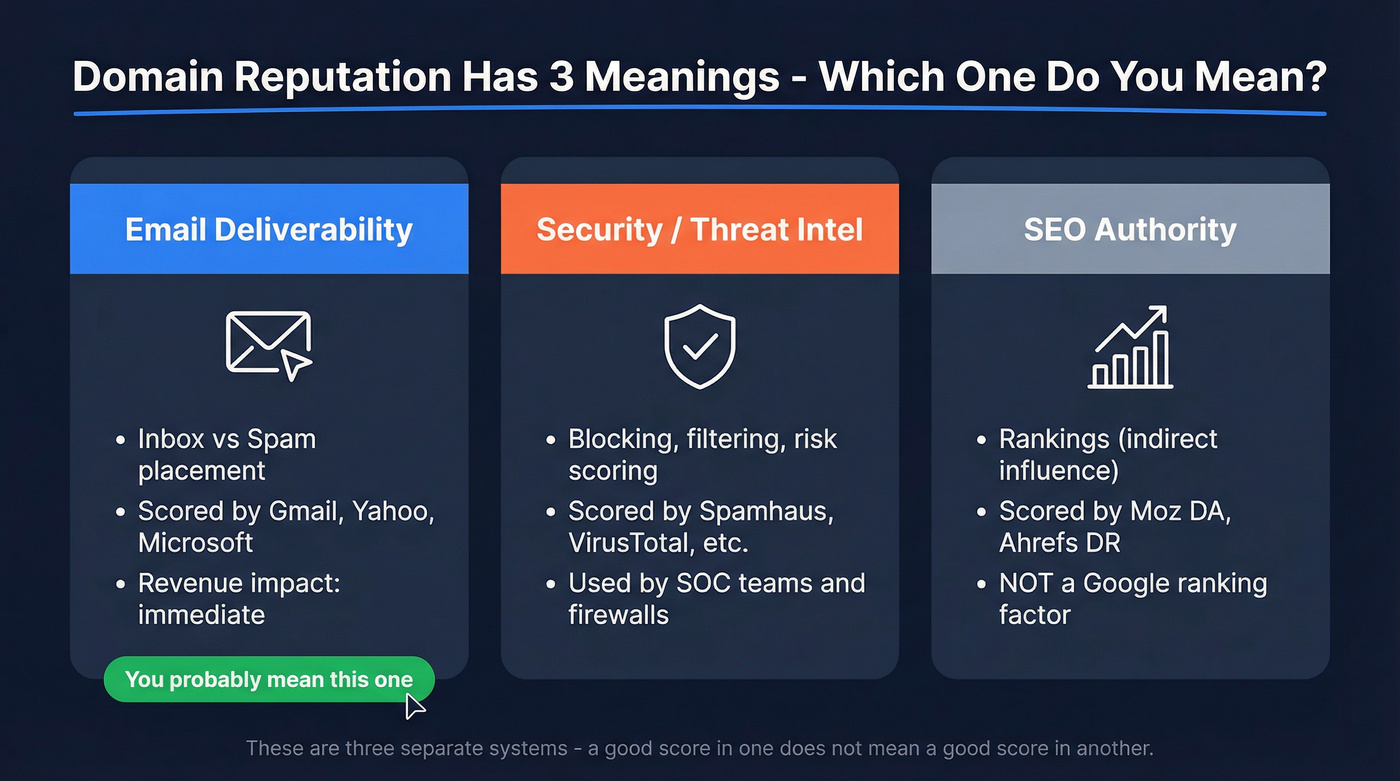
The fastest way to untangle it is to pick the ecosystem:
- Email deliverability reputation (inbox vs spam)
- Security / threat-intel reputation (blocking, filtering, risk scoring)
- SEO "authority" reputation (third-party metrics people confuse with Google)
Spamhaus has a framing that's actually useful because it's operational, not fluffy: domain reputation is a domain's fingerprint - the who, what, where, and when behind it. That's a security lens. It helps answer questions like "Should we trust this domain?" and "Is this domain part of an abuse cluster?" It doesn't directly answer "Will my cold email land in Gmail's inbox?"
Where security domain reputation is used (real-world use cases)
Security teams use domain reputation everywhere, often without calling it that:
- SOC triage: prioritize alerts when a domain shows up in logs, emails, or endpoint telemetry
- Phishing URL filtering: block or warn on links based on domain risk signals
- DNS firewall policy: allow/deny categories and newly seen domains
- Fraud prevention: detect lookalike domains, burner domains, and suspicious redirects
- Vendor risk checks: vet partner domains used for portals, invoicing, or SSO flows
- Brand protection: monitor for impersonation domains and malicious landing pages
What makes up the "fingerprint" (security lens)
Security reputation systems look at patterns like:
- Ownership and registration signals: registrar, registration timing, changes, privacy patterns
- Infrastructure associations: hosting, ASN, name servers, shared IP neighborhoods
- Observed behavior: spam/phishing/malware hosting, redirect chains, command-and-control patterns
- Historical context: whether the domain has a long clean history or a short suspicious one
How domain reputation gets gamed (security lens)
Attackers don't just "create a domain and blast." They play the long game:
- Warming: send low-volume benign traffic to build a clean-looking history
- Aging: sit on domains for weeks/months so they don't look "brand new"
- Expired-domain takeovers: buy an old, trusted domain and repurpose it for abuse (this is how "sudden" trust flips happen)
That's why security reputation is about clusters and history, not just today's content.
The SEO meaning (and why it causes endless confusion)
In SEO, "domain reputation" often gets used as a casual synonym for "domain authority." That's where the terminology gets messy.
A quick myth-bust that saves arguments: Moz Domain Authority (DA) is a third-party 1-100 metric and not a Google ranking factor. It can be a helpful comparative signal inside Moz's ecosystem, but it's not "your reputation with Google."
Here's the taxonomy that keeps everyone sane:
| Meaning | What it affects | Who scores it | What people confuse it with |
|---|---|---|---|
| Email deliverability | Inbox vs spam | Mailbox providers | "One global score" |
| Security/threat intel | Blocking/vetting | Threat intel networks | Deliverability |
| SEO "authority" | Rankings (indirect) | Third-party tools | Google ranking factor |
If you're here because emails started bouncing, getting blocked, or landing in spam, you mean the email version. That's the one that costs revenue fast.
What is domain reputation for email deliverability? (Where it shows up in a message)
Email sending reputation is the trust mailbox providers assign to your sending identity based on recipient reactions and whether your setup looks legitimate. That trust decides inbox, spam, throttling, or rejection.
Two things most teams miss.
1) It's one reputation per receiver
Your domain doesn't have "a reputation." It has many reputations - one per mailbox provider, and often one per internal model inside that provider. Gmail can hate you while Yahoo is fine. Microsoft can throttle you while Gmail still delivers.
2) Your domain appears in multiple "surfaces," not just the From line
Mailbox providers evaluate several domain surfaces in a single message. If they don't line up, you look evasive.
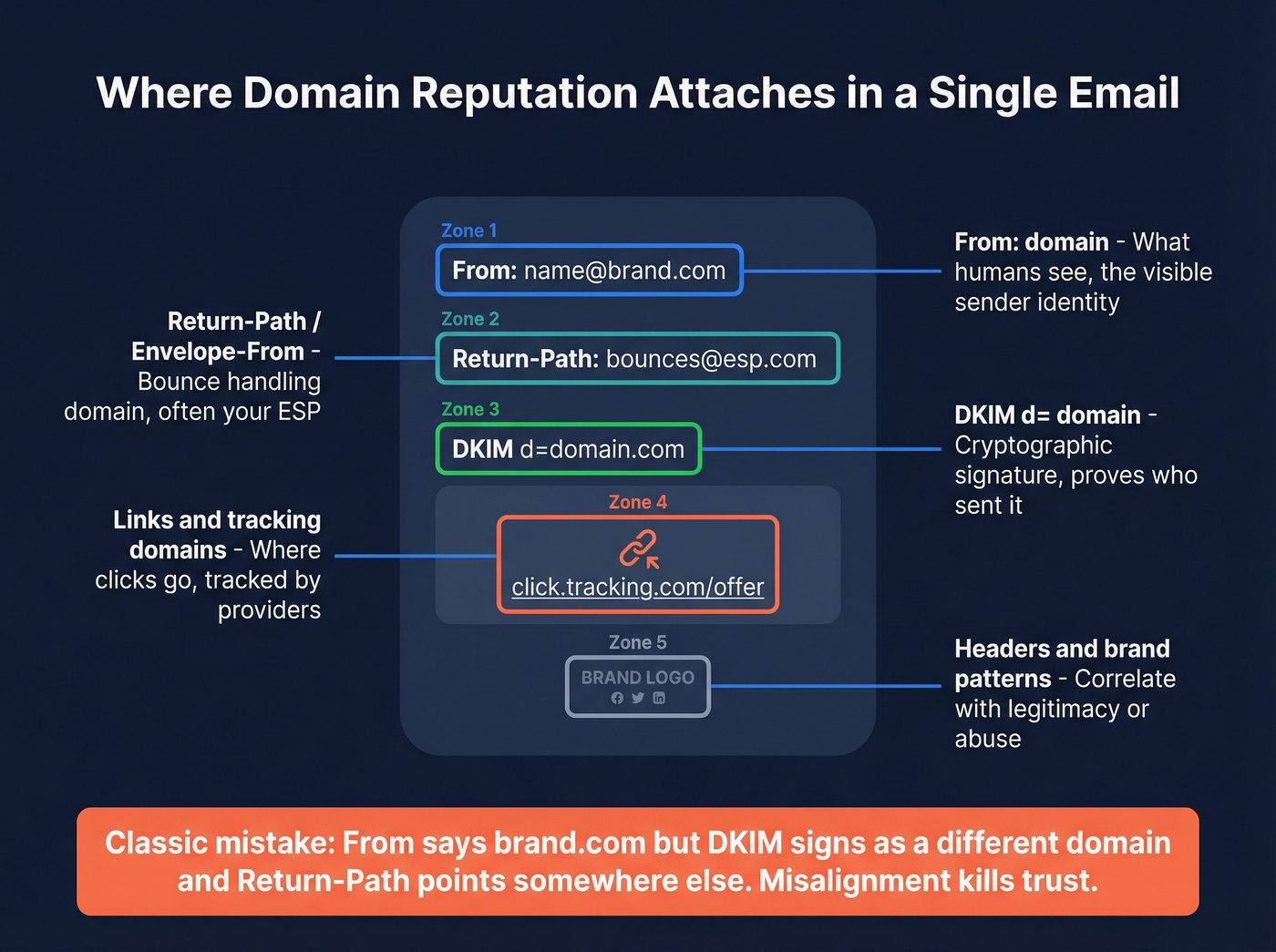
Where reputation can attach:
- From: the visible sender domain (what humans see)
- Return-Path / Envelope-From: the bounce/handling domain (often ESP infrastructure)
- DKIM d=: the domain that cryptographically signs the message
- Links/content domains: where your email sends people (tracking domains, landing pages)
- Headers + brand assets: patterns that correlate with abuse or legitimacy
A classic deliverability faceplant: you "look" like brand.com in the From address, but DKIM signs as a different domain and the Return-Path points somewhere else. That mismatch often happens after switching ESPs, adding a tracking domain, or changing sending services.
Here's the thing: if your average deal size is modest and you're doing outbound, your biggest deliverability problem is almost never "content." It's list quality and alignment. Fix those first and you'll feel like you found a cheat code.

You just read that high bounces torch domain trust fast. That's exactly what happens when you prospect with unverified data. Prospeo's 5-step email verification - with catch-all handling, spam-trap removal, and honeypot filtering - delivers 98% accuracy. Teams switching from other providers cut bounce rates from 35%+ to under 4%.
Stop gambling your domain reputation on bad contact data.
Domain reputation vs IP reputation (and why SNDS won't answer your domain question)
Domain reputation and IP reputation influence each other, but they're not interchangeable.
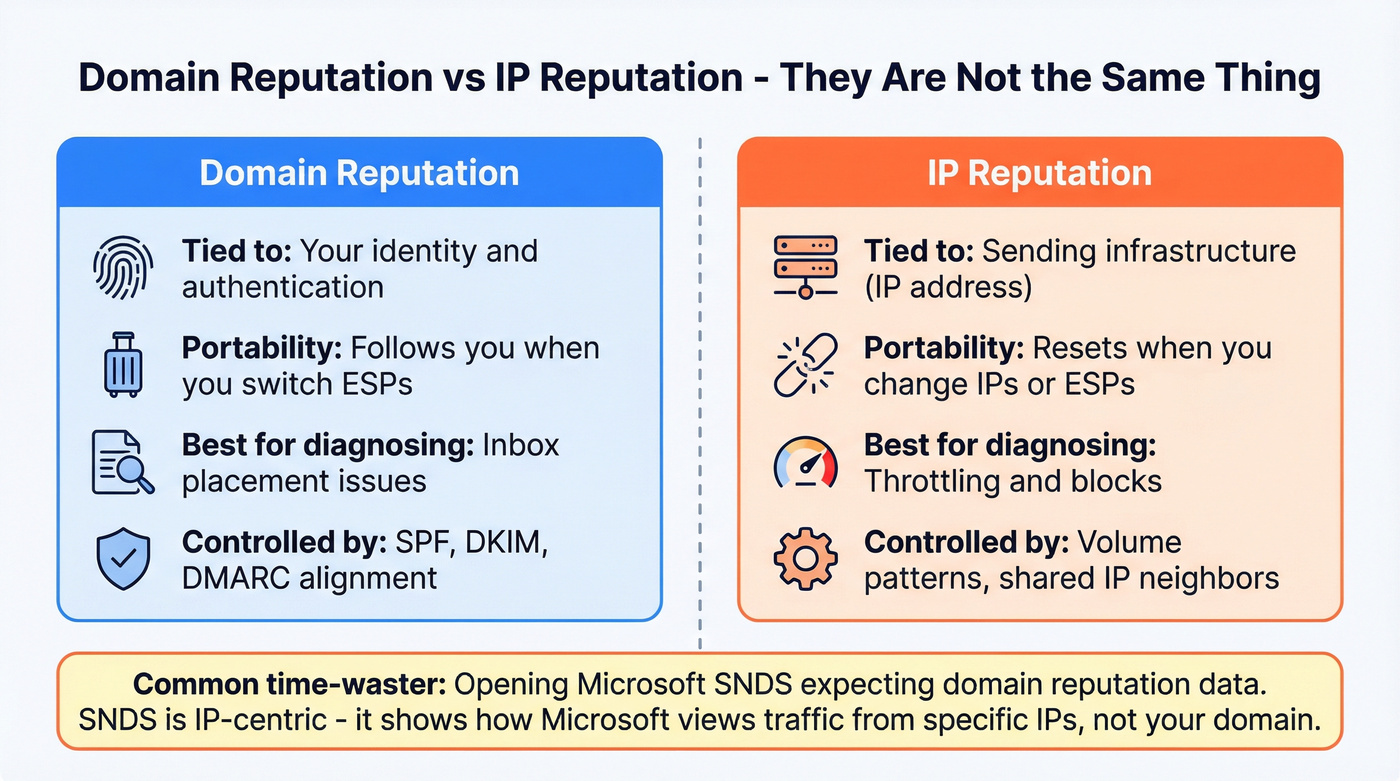
- IP reputation is tied to the sending infrastructure (the IP address your mail comes from).
- Domain sending reputation is tied to your identity (the domain you control and authenticate).
Practical takeaway: domains are portable; IPs are infrastructure-tied.
If you switch ESPs, rotate IPs, or move from shared to dedicated infrastructure, your IP reputation can change quickly. Your domain reputation follows you more - assuming you keep authentication aligned and behavior consistent.
This is also where people waste time: they open Microsoft SNDS expecting "domain reputation," then wonder why it's not helping.
SNDS is IP-centric. It's useful for understanding how Microsoft views traffic from specific IPs (volume patterns, complaint signals, potential throttling). It won't give you a clean domain-level answer because that's not what it's built for.
| Question | Domain reputation | IP reputation |
|---|---|---|
| What is it? | Trust in your domain | Trust in your IP |
| Tied to | Identity/auth | Infrastructure |
| Changes when you switch ESPs | Less (if aligned) | More |
| Best for diagnosing | Inbox placement | Throttling/blocks |
What signals actually move domain reputation (the inputs mailbox providers care about)
Mailbox providers respond to signals that correlate with abuse. If you want better reputation, manage the signals - don't chase vibes.
Mailgun has a distinction too many teams still miss, and it shows in how they report results. In one Mailgun survey, only 12% of respondents said they understood their delivery rate, which tracks with how often teams confuse "accepted by server" with "in the inbox."
Delivery vs deliverability (stop measuring the wrong thing)
- Delivery = the receiving server accepted the message.
- Deliverability = where it lands (inbox vs spam vs tabs), or whether it gets filtered later.
You can have 99% delivery and awful deliverability. That's how teams get fooled by "green checks" while real opens collapse.
The signals that move reputation fastest
These are the big movers:
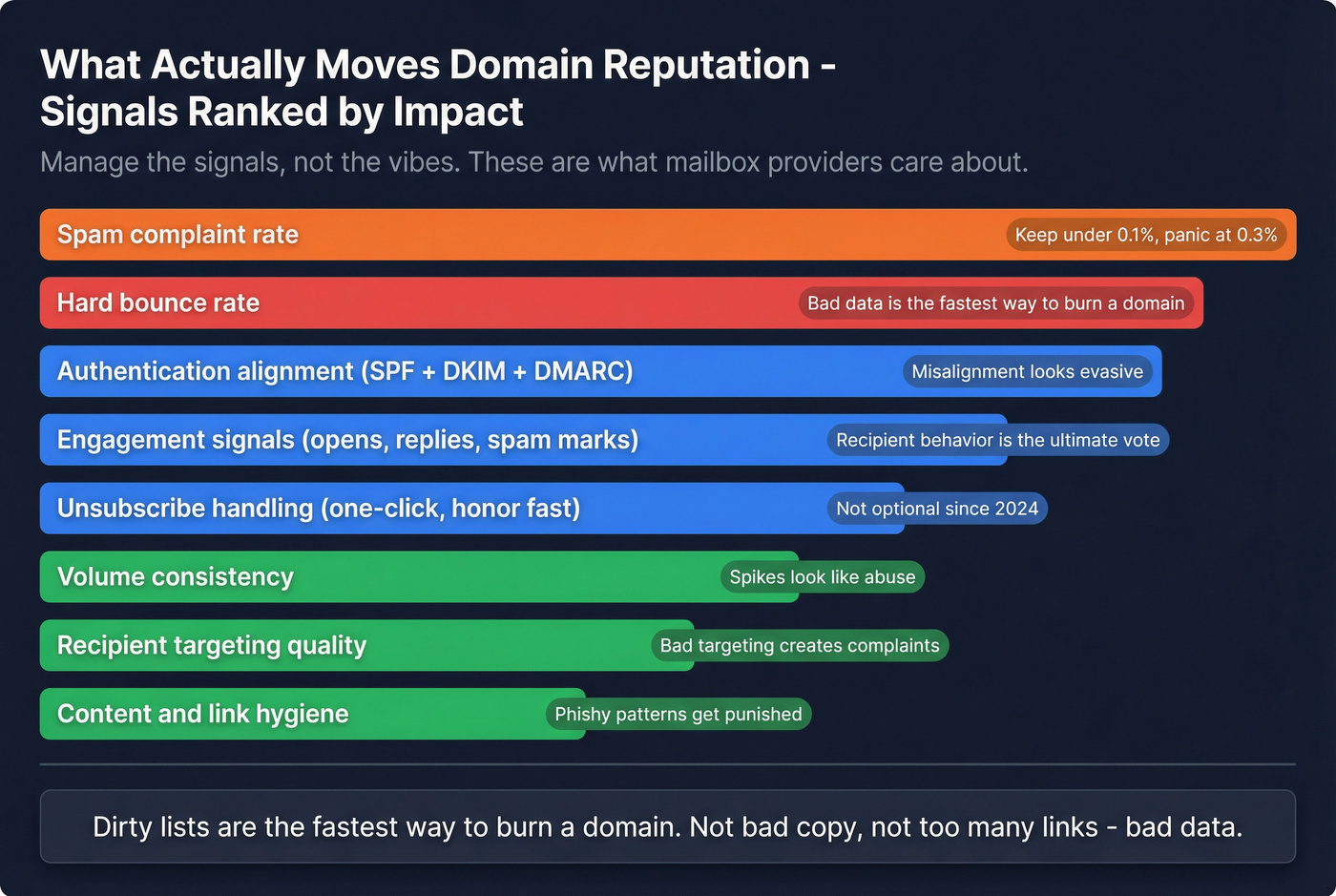
- Spam complaint rate (the thermostat)
- Bounce rate (hard bounces are poison)
- Authentication pass + alignment (SPF, DKIM, DMARC)
- Unsubscribe behavior (one-click support, honoring opt-outs quickly)
- Engagement (reads, replies, deletes, "mark as spam")
- Volume + consistency (spikes look like abuse)
- Content + link hygiene (phishy patterns, sketchy domains, URL shorteners)
- Recipient targeting quality (bad targeting creates complaints)
In our experience, dirty lists are the fastest way to burn a domain. Not "bad copy," not "too many links" - bad data.
Do / avoid (the stuff that actually changes outcomes)
Do:
- Operate to <0.1% spam complaints.
- Keep hard bounces near zero.
- Align From, DKIM d=, and your DMARC policy.
- Segment mail streams so one program can't contaminate the rest.
Avoid:
- Blasting a new segment with weak targeting and unclear opt-out.
- Switching sending domains/tracking domains every other week.
- Treating "unsubscribe" like a legal checkbox instead of a reputation control.
2026 enforcement reality: Yahoo + Microsoft + Gmail
If deliverability feels harder than it used to, you're right. The 2024-2025 enforcement wave turned "best practices" into "requirements," especially for bulk senders.
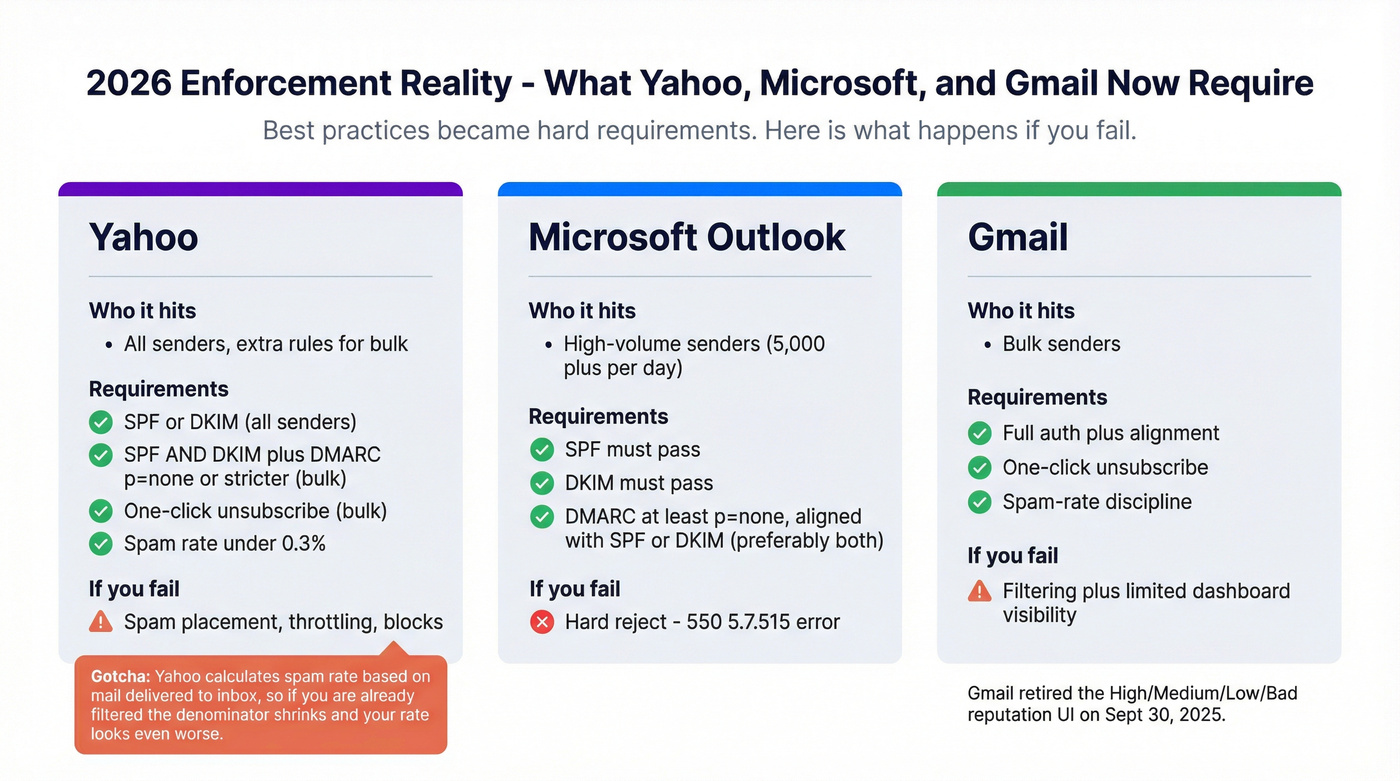
One reason Gmail feels more opaque in 2026: Gmail Postmaster Tools retired the old High/Medium/Low/Bad reputation UI on Sept 30, 2025, so you lost the simplest "at a glance" reputation bar.
| Provider | Who it hits | Key requirements | What happens if you fail |
|---|---|---|---|
| Yahoo | All senders (with extra rules for bulk senders) | All: SPF or DKIM; Bulk: SPF and DKIM + DMARC p=none or stricter (must pass; relaxed alignment OK) + one-click unsubscribe; spam <0.3% | Spam placement, throttling, blocks |
| Microsoft (Outlook.com) | High-volume senders (>5,000/day) | SPF must pass + DKIM must pass; DMARC at least p=none and align with SPF or DKIM (preferably both) | 550 5.7.515 hard reject |
| Gmail | Bulk senders | Compliance focus (auth + alignment + one-click unsubscribe + spam-rate discipline); reputation bars removed from Postmaster Tools | Filtering + limited dashboard visibility |
Yahoo gotcha (worth highlighting): Yahoo's spam-rate math is unforgiving. They calculate spam rate based on mail delivered to the inbox, so if you're already being filtered, the denominator shrinks and your spam rate can look worse.
Useful links:
- Yahoo sender best practices: https://senders.yahooinc.com/best-practices/
- Microsoft high-volume sender requirements: https://techcommunity.microsoft.com/blog/microsoftdefenderforoffice365blog/strengthening-email-ecosystem-outlook%E2%80%99s-new-requirements-for-high%E2%80%90volume-senders/4399730
When you see Microsoft "550 5.7.515," do this (don't guess)
That code means "you didn't meet authentication requirements," not "your subject line is spammy."
Fix in this order:
- Confirm the visible From domain matches what you intend to authenticate.
- Make sure SPF passes for the actual sending service.
- Make sure DKIM passes and the d= domain aligns with From.
- Publish DMARC p=none or stricter and validate alignment.
I've watched teams lose a full week arguing about copy changes while that one DMARC alignment issue sat there, quietly wrecking Outlook delivery the whole time.
How to check domain reputation in 2026 (without a score)
The old mental model was: "Check Postmaster Tools, see High/Medium/Low/Bad, adjust." That model's dead.
In 2026, you monitor outcomes and inputs: spam rate, authentication/alignment, rejection codes, and blocklist exposure.
A practical tool stack (with pricing signals)
| Tool | What it tells you | What it doesn't | Pricing signal |
|---|---|---|---|
| MxToolbox | DNS/auth/RBL checks | Inbox placement | Free + ~$10-30/mo monitoring |
| Spamhaus lookup | Threat intel context | Not a deliverability grade | Free lookups; enterprise feeds vary |
| Talos Intel | Reputation/category context | Not inbox placement | Free |
| Google Postmaster Tools | Spam rate + auth/compliance | No rep bars now | Free |
| Microsoft SNDS | Microsoft IP telemetry | Not domain reputation | Free |
| MultiRBL / MultiRBL.valli | Many RBLs in one scan | Root cause analysis | Free |
| BarracudaCentral | Barracuda reputation/listing | Gmail/Yahoo specifics | Free lookup |
| SURBL / URIBL checks | Link-domain reputation | Sender identity reputation | Free |
| Feedback loops (FBLs) | Complaint events (where offered) | Not universal coverage | Setup time cost |
| SenderScore | IP-centric score | Not domain truth | Free; paid monitoring often ~$20-100/mo |
The 10-minute triage workflow (do this in order)
If you need a repeatable "check domain reputation" routine, this is it:
Confirm what domain surfaces you're actually using
- From domain, DKIM d= domain, Return-Path domain, tracking/link domains.
- If these changed recently, assume that's the trigger until proven otherwise.
Validate authentication + alignment (SPF/DKIM/DMARC)
- Use MxToolbox to catch syntax errors and missing records fast.
- Then validate alignment: passing isn't enough if it doesn't align with From.
Scan blocklists (broad, then specific)
- Run MultiRBL for a quick "are we listed anywhere obvious?" sweep.
- If Barracuda matters in your ecosystem, check BarracudaCentral directly.
- If you need a broader workflow, see our blacklist alert triage guide.
Check provider dashboards (if you have volume)
- Gmail Postmaster: focus on spam rate + auth/compliance.
- Microsoft SNDS: look for volume anomalies and complaint patterns by IP.
Look for complaint signals and unsubscribe friction
- If complaints rise, stop that segment immediately.
- Make List-Unsubscribe (RFC 8058 one-click) easy. Unsubscribe friction turns into spam clicks.
Audit link domains (SURBL/URIBL) and redirects
- A clean sender domain can still get filtered if your links look phishy.
- Avoid URL shorteners and messy redirect chains.
Compare timing against changes
- New ESP, new tracking domain, new list source, new cadence - these are the usual culprits.
- "Nothing changed" is almost always wrong; something changed.
Real talk: most "domain reputation checks" fail because people start with blocklists. Start with alignment and list quality. Blocklists are a symptom check, not a diagnosis.
Why you can't find a "domain reputation score" anymore (and what to monitor instead)
The simplest dashboards are gone, and that's why operators feel blind.
Gmail Postmaster Tools used to give you a clean reputation bar. That UI ended on Sept 30, 2025, and the replacement experience pushes you toward monitoring inputs and outcomes instead of a single label.
Monitor this instead:
- Spam rate (complaints)
- Authentication pass + alignment (SPF/DKIM/DMARC aligned to From)
- Rejection codes and temp fails (especially Microsoft-style hard rejects)
- Bounce rate trends (hard bounces and unknown users)
- Consistency (volume spikes, new domains, new link patterns)
- Rolling averages (improvements lag; don't expect same-day recovery)
What practitioners are seeing in 2026 (the pattern's consistent)
A few themes keep coming up among operators:
- Postmaster "v2" feels like it removed the one chart people actually used day-to-day.
- Seed tests and "green" tool results don't match reality when opens suddenly collapse.
- Deliverability tanks right after operational changes: new ESP, new tracking domain, new list source, or a rushed ramp-up.
That last bullet is the one to tattoo on your process: treat changes like migrations, not toggles.
How to improve domain reputation fast (fix-first playbook)
This is the order that works in the real world. Not the order vendors sell.
1) Authentication + alignment (do this before anything else)
- Ensure SPF passes for the actual sending infrastructure.
- Ensure DKIM passes and the DKIM d= aligns with your From domain (or a controlled subdomain strategy).
- Publish DMARC p=none or stricter, then tighten once stable.
- Keep domain surfaces consistent. Randomly rotating domains looks like evasion.
If you only do one technical thing this week: make alignment boring. Boring is good. If you need a setup walkthrough, start with our SPF DKIM & DMARC guide.
2) Unsubscribe compliance (it's reputation protection)
- Implement List-Unsubscribe and one-click where supported (RFC 8058).
- Honor unsubscribes fast - within 2 days is the Yahoo bar for bulk senders.
- Don't hide the link. People who can't unsubscribe will complain.
3) Complaint rate control (this is the thermostat)
- Operate to <0.1% spam complaints.
- Treat >=0.3% as a hard ceiling where filtering and blocking risk jumps.
- If complaints spike: stop sending to that segment, tighten targeting, and reduce frequency.
If you want the exact limits and what providers enforce, see spam complaint thresholds.
4) List hygiene + bounce control (fastest lever for most teams)
If you need a quick win, this is it. Hard bounces and spam traps accelerate reputation damage.
We've tested a lot of list workflows over the years, and the pattern's always the same: the teams that verify before they send don't end up in "why are we in spam?" fire drills every quarter.
Prospeo - "The B2B data platform built for accuracy" - is the best pick we've used for email accuracy, data freshness, and self-serve B2B data. It has 300M+ professional profiles, 143M+ verified emails, and 125M+ verified mobile numbers, with 98% verified email accuracy and a 7-day data refresh cycle (the industry average is about 6 weeks). If you're building outbound lists, you can use Prospeo's real-time verification and its 5-step verification (including catch-all handling, spam-trap removal, and honeypot filtering) to keep hard bounces from snowballing into reputation damage.
If you're comparing vendors, use our email verifier websites roundup and the best email scrubbing services guide.
Skip this if you're only sending a tiny internal newsletter to a few hundred known contacts and you never import lists. Everyone else should treat verification as non-negotiable.
5) If/then diagnostics (so you don't guess)
- If delivery is fine but opens cratered: you've got a placement problem - look at complaints, engagement, and link domains.
- If you see Microsoft hard rejects (550 5.7.515): authentication/alignment is failing Microsoft's bar; fix SPF/DKIM/DMARC first. (More detail: 550 Recipient Rejected.)
- If bounces jumped after a new list upload: stop the campaign, verify the list, and re-segment.
- If you changed ESPs or tracking domains: expect turbulence unless alignment stayed consistent.
6) Volume spikes and warm-up (secondary, not primary)
Warm-up tools are rarely the first fix. If complaints or bounces are high, warm-up won't save you - it just trains providers that your domain generates negative signals.
Do this instead:
- Increase volume gradually.
- Keep targeting tight.
- Keep patterns consistent (same From, stable domain surfaces, stable link behavior).
If you're doing outbound, pair this with a real sending plan: email pacing and sending limits.
7) Content and link hygiene (don't look like a phish)
- Avoid URL shorteners and sketchy redirect chains.
- Keep branding consistent across domains.
- Don't bolt on random widgets and link farms in footers.
The "one-week recovery" expectation setting
You can usually stop the bleeding in a week (bounces down, complaints down, auth aligned). Full recovery often takes longer because reputation is trend-based and laggy, and mailbox providers reward sustained good behavior far more than a single clean send.
Two-sentence wrap-up that's actually true: align SPF/DKIM/DMARC, keep complaints under 0.1%, and stop sending to bad addresses. Everything else is optimization.

List quality is the #1 deliverability lever for outbound teams - you said it yourself. Prospeo refreshes all 300M+ records every 7 days (not the 6-week industry average), so you're never sending to stale addresses that spike complaints and bounces. At $0.01 per email, clean data costs less than one spam folder disaster.
Fresh data every 7 days means your domain stays clean.
FAQ
Is domain reputation the same as IP reputation?
Domain reputation is trust in your sending domain identity, while IP reputation is trust in the infrastructure IP that delivers your mail. They influence each other, but they aren't interchangeable: domains can move across ESPs, while IPs change with infrastructure and can be shared or rotated.
What's a "good" spam complaint rate for protecting domain reputation?
A strong operating target is keeping spam complaints under 0.1%, because it gives you buffer for normal variance. Treat 0.3% or higher as a hard ceiling where filtering and blocking risk jumps, especially under modern Yahoo/Microsoft/Gmail enforcement.
Did Google remove domain reputation from Postmaster Tools?
Yes. Gmail Postmaster Tools' old domain and IP reputation charts (the High/Medium/Low/Bad UI) were retired on Sept 30, 2025. In 2026, you monitor spam rate, authentication/alignment, and compliance status instead of a simple reputation bar.
How can I reduce bounces quickly to protect domain reputation?
Stop sending to unverified addresses: verify new lists before launch, re-verify older lists, and suppress risky patterns (role accounts, dead domains, obvious typos). Prospeo helps by verifying emails in real time with 98% accuracy and filtering spam traps and honeypots, so bounces don't snowball into reputation damage.
Summary: what is domain reputation (the useful definition)
What is domain reputation in practice? It's the trust different systems assign to your domain based on behavior and history - especially mailbox providers deciding whether your messages belong in the inbox.
In 2026, you don't "find the score." You manage the inputs: alignment, complaints, bounces, consistency, and clean data.