How to Set Up SPF, DKIM & DMARC for Cold Email - The Complete 2026 Guide
1 in 6 legitimate emails never reaches the inbox. That's the Validity benchmark, and it's gotten worse since Gmail, Yahoo, and Outlook all started enforcing authentication. If you're running cold outbound without proper SPF, DKIM, and DMARC records, you're lighting money on fire.
98% of spam filters check authentication records before they look at anything else. Your subject line, your copy, your offer - none of it matters if your emails fail authentication. Properly authenticated cold emails pull 15-20% response rates. Unauthenticated ones see 10-20% lower inbox placement, and that gap widens every quarter.
Most guides walk you through the DNS records and stop. They skip the domain strategy that keeps your primary domain safe, the 10-lookup limit that silently breaks SPF, the warmup cadence that builds reputation, and the list verification step that prevents bounces from undoing all your work. We've set up authentication across dozens of cold email domains, and the same mistakes keep showing up. This guide covers all of them.
What You Need for Cold Email Domain Authentication
Think of it this way: SPF is your guest list (who's allowed to send), DKIM is a wax seal (proves the message wasn't tampered with), and DMARC is the bouncer (decides what happens when someone fails the check).
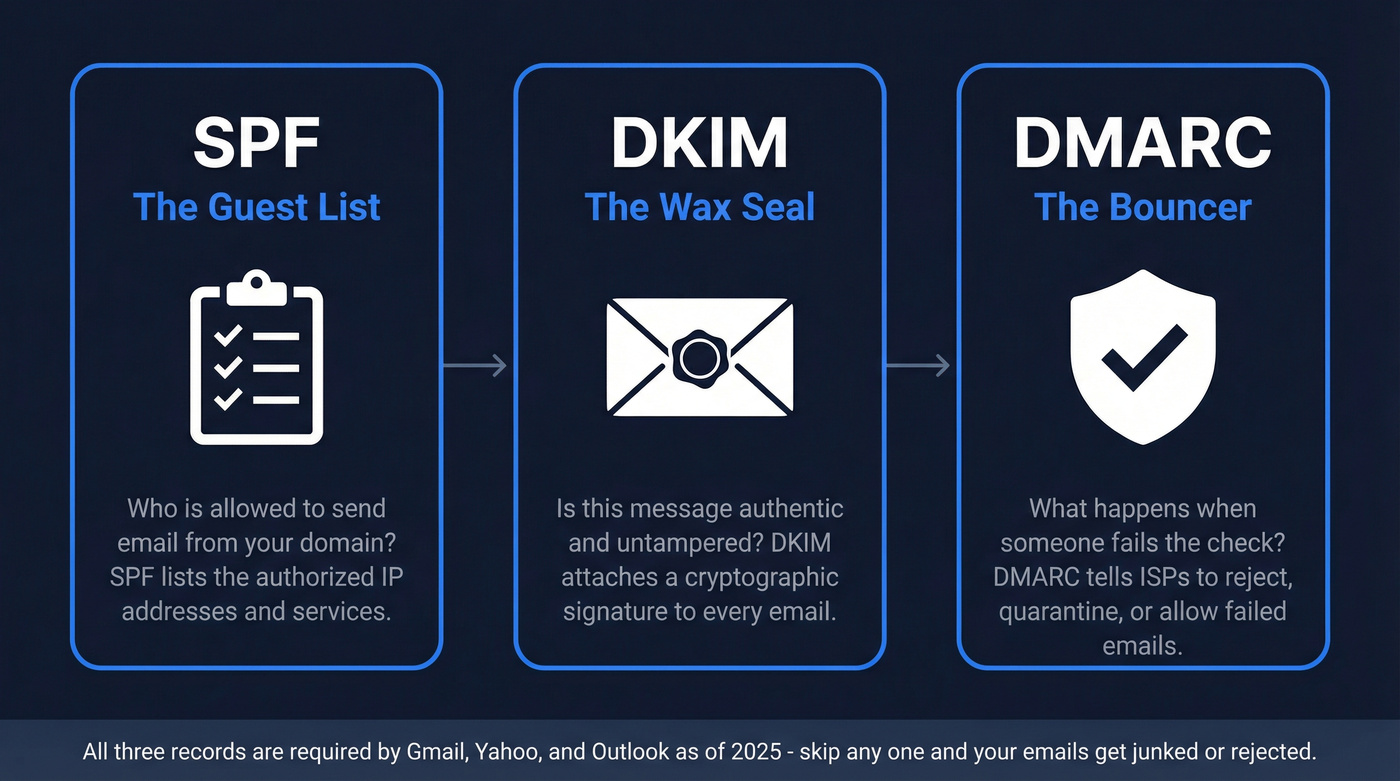
Here's the checklist:
- Three DNS records: SPF, DKIM, DMARC
- A dedicated sending domain - never your primary business domain
- An email provider: Google Workspace (~$6/user/month) or Microsoft 365
- A cold email tool: Instantly, Smartlead, Lemlist, or similar
- 30-60 minutes for the full setup
Three ISPs now enforce authentication: Gmail (February 2024), Yahoo (February 2024), and Outlook (May 2025). Skip any of the three records and your emails get junked or rejected outright. This isn't optional anymore.
The ISP Enforcement Landscape in 2026
Gmail and Yahoo moved first. In February 2024, both started requiring SPF, DKIM, and DMARC for bulk senders. Microsoft followed in May 2025, targeting domains sending over 5,000 emails per day to Outlook.com addresses (including Hotmail and Live). 60.3% of businesses identify spam filtering as their top inbox placement barrier - and these enforcement changes are why.
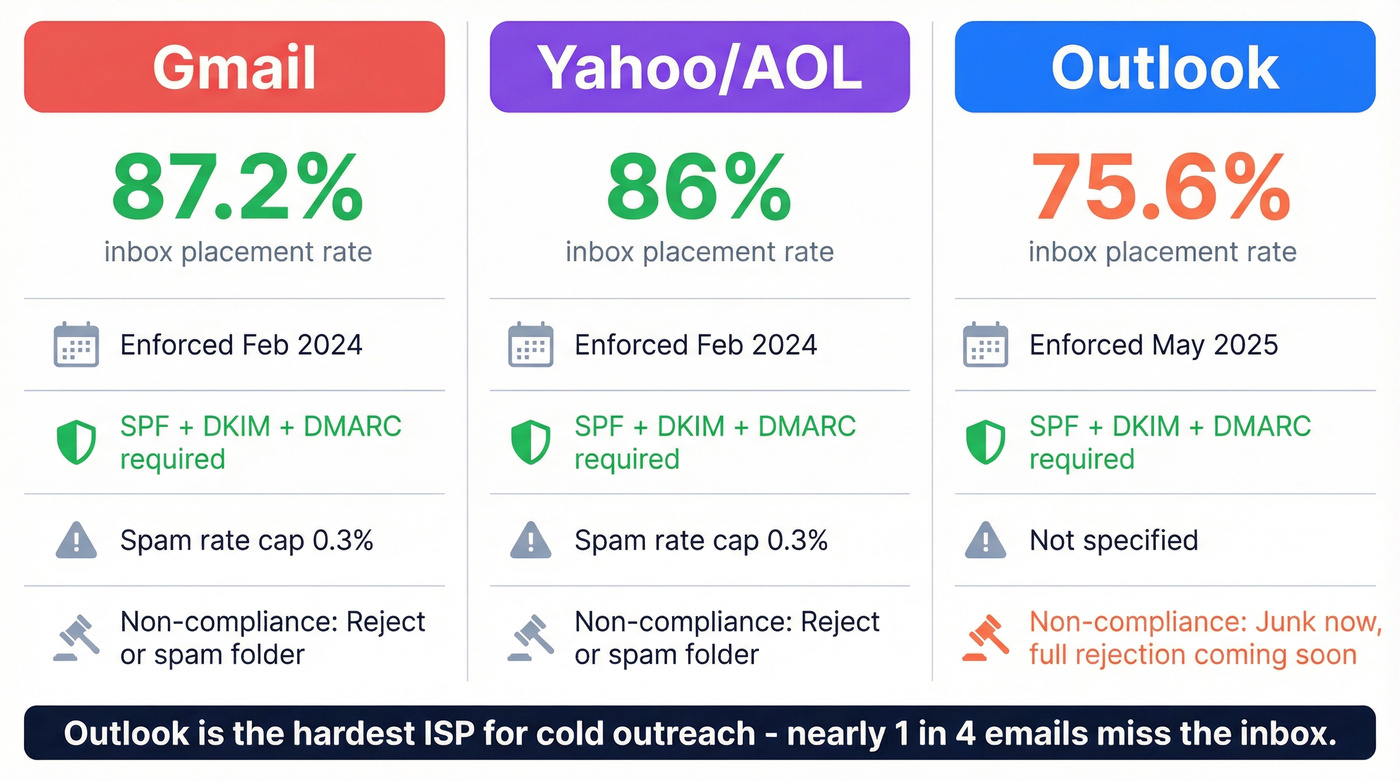
Here's what each ISP demands:
| Requirement | Gmail | Yahoo/AOL | Outlook |
|---|---|---|---|
| Enforcement date | Feb 2024 | Feb 2024 | May 2025 |
| Threshold | Bulk senders | Bulk senders | 5,000+/day |
| SPF required | Yes | Yes | Yes |
| DKIM required | Yes | Yes | Yes |
| DMARC required | p=none min | p=none min | p=none min |
| Spam rate limit | 0.3% | 0.3% | Not specified |
| One-click unsub | Yes | Yes (RFC 8058) | Recommended |
| Non-compliance | Reject/spam | Reject/spam | Junk then rejection |
| Inbox placement | 87.2% | 86% | 75.6% |
Look at Outlook's inbox placement: 75.6%. Nearly 1 in 4 emails sent to Outlook addresses doesn't land in the inbox. Microsoft's AI-based filters and user feedback loops make it the hardest ISP for cold outreach. Their April 2025 update announced escalation from junk-routing to outright rejection (550; 5.7.515 error) - the rejection phase hasn't been dated yet but is confirmed coming. (If you’re seeing this now, use our guide to the 550; 5.7.515 error.)
Gmail's 87.2% is better but dropped from 89.8% in early 2024. Yahoo sits at 86% and is generally more forgiving with clean authentication.
The takeaway: all three ISPs treat authentication as table stakes. The differences are in how aggressively they punish failures - and Outlook is particularly brutal about technical setup.
Before You Touch DNS - Domain Strategy
Before you configure a single record, you need the right domain structure. This is where most teams make their first mistake.
Subdomain vs. Separate Domain
Never use your main business domain for cold email. One spam complaint and suddenly your CEO's emails bounce. You need a buffer.
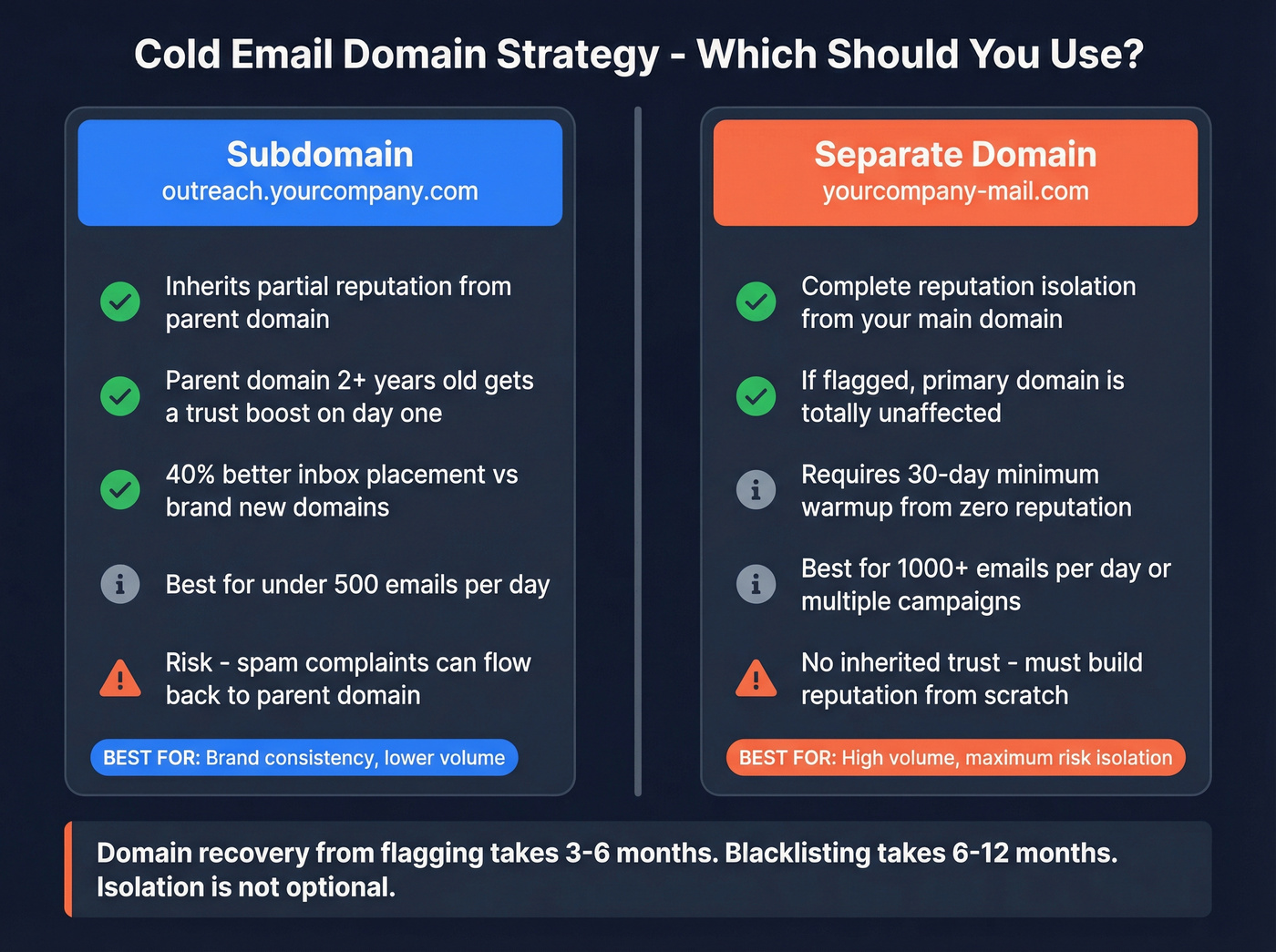
You've got two options: a subdomain (outreach.yourcompany.com) or a completely separate domain (yourcompany-mail.com).
Subdomains inherit partial reputation from the parent domain. If your parent domain is 2+ years old with clean history, a subdomain gets a trust boost from day one. Domains aged 2+ years see 40% better inbox placement than new domains. Use a subdomain when you're sending under 500 emails per day and want brand consistency.
Separate domains are better for higher volume - 1,000+ emails daily or multiple concurrent campaigns. They require a 30-day minimum warmup from zero reputation, but they completely isolate risk. If a separate domain gets flagged, your primary domain doesn't feel it.
Domain recovery from flagging takes 3-6 months. Blacklisting? 6-12 months. That's why isolation matters. (If you need triage steps, see our blacklisting guide.)
Each subdomain or separate domain needs its own SPF, DKIM, and DMARC records. No shortcuts.
How Many Domains, Mailboxes, and Warmup
Serious cold outreach teams operate 3-5 domains rotating daily, each with 4-6 inboxes, capped at 40-50 emails per inbox per day. That's not paranoia - it's math. Spreading volume across multiple domains and mailboxes keeps each one under ISP radar.
Don't skip warmup. Start at 10-15 emails per day per inbox and ramp over 2-3 weeks to your target of 40-50/day. New domains and mailboxes have zero reputation - blasting 50 emails on day one is the fastest way to get flagged. Most cold email tools (Instantly, Smartlead, Lemlist) have built-in warmup features. Use them. (For a full cadence, use our email warmup playbook.)
Choosing a Domain and Email Provider
Stick to simple extensions: .com, .co, .io. Avoid .xyz or .site - they carry spam associations.
Google Workspace is the best option for cold email deliverability at ~$6/user/month. Resellers offer 20-30% cheaper rates. Microsoft 365 works too, but I've consistently seen better inbox placement with Google Workspace across dozens of domain setups.

You just spent 30-60 minutes perfecting SPF, DKIM, and DMARC. Don't waste that setup by sending to bad addresses. Bounces above 3% destroy sender reputation faster than missing authentication. Prospeo's 5-step email verification delivers 98% accuracy - teams using it cut bounce rates from 35%+ to under 4%.
Protect your domain reputation with emails that actually exist.
SPF Setup - Step by Step
SPF (Sender Policy Framework) tells receiving servers which IP addresses and services are authorized to send email from your domain. Without it, anyone can spoof your domain. Getting your SPF record right is the foundation everything else builds on. (If you want a deeper syntax breakdown, see our SPF record guide.)
Building Your SPF Record (With Multi-Tool Examples)
Your SPF record is a single TXT record on your domain's DNS. Here's the syntax:
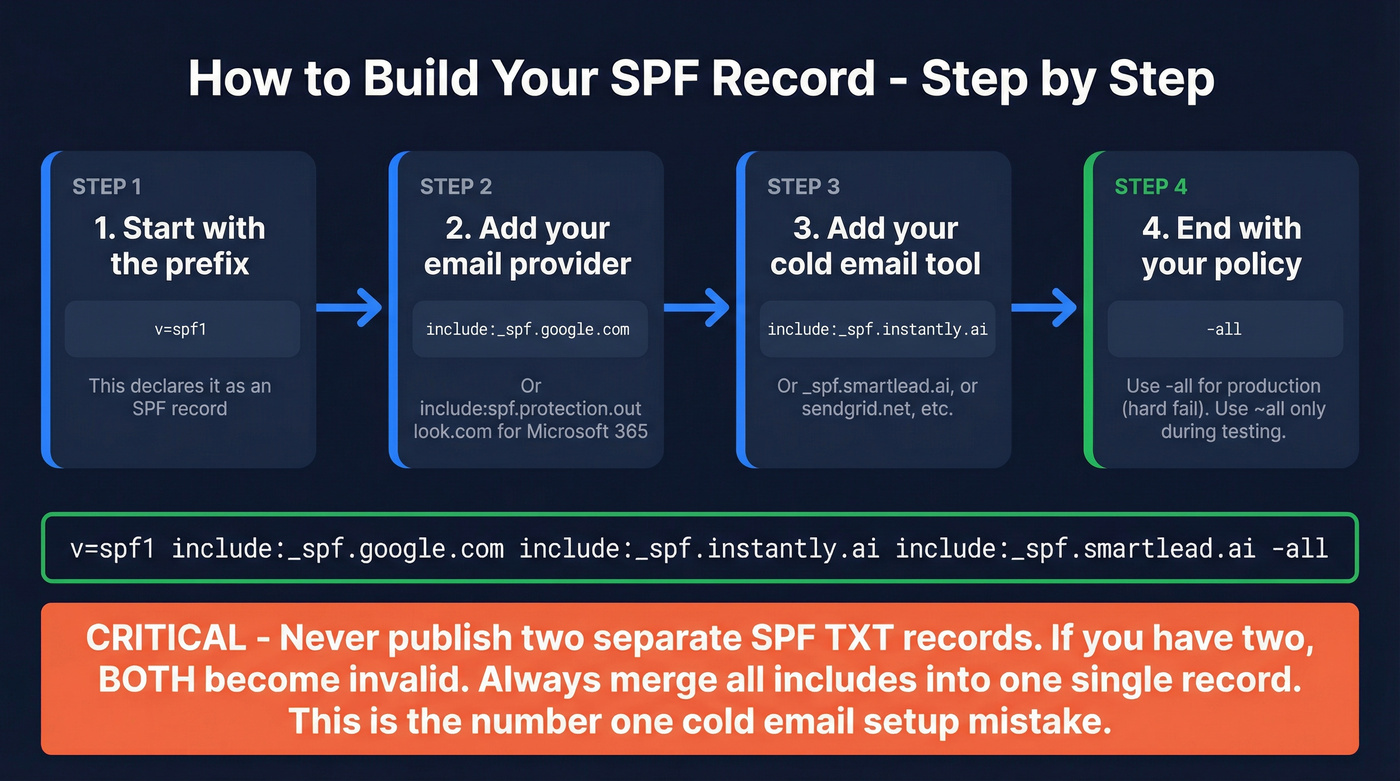
v=spf1 include:_spf.google.com include:_spf.instantly.ai ~all
That record authorizes Google Workspace and Instantly to send on your behalf. The ~all at the end means "soft fail anything else" (useful during testing). For production cold email, switch to -all (hard fail) - it tells ISPs to reject unauthorized senders outright.
Here are the include values for common services:
- Google Workspace:
include:_spf.google.com - Microsoft 365:
include:spf.protection.outlook.com - Instantly:
include:_spf.instantly.ai - Smartlead:
include:_spf.smartlead.ai - SendGrid:
include:sendgrid.net
A typical multi-tool SPF record looks like this:
v=spf1 include:_spf.google.com include:_spf.instantly.ai include:_spf.smartlead.ai -all
Critical rule: never publish two SPF TXT records. If you have two, both become invalid. Merge all your includes into a single record. This is the #1 setup mistake in cold email infrastructure - teams add a new tool's SPF record as a separate entry instead of merging it into the existing one.
Where to Add Your TXT Record (By Registrar)
If you know you need a TXT record but can't find the DNS settings, here's where to go:
- GoDaddy: My Products -> DNS -> Manage Zones -> select domain -> Add Record -> TXT
- Cloudflare: Select domain -> DNS -> Records -> Add Record -> TXT
- Namecheap: Domain List -> Manage -> Advanced DNS -> Add New Record -> TXT
Set the Host/Name to @ (root domain), paste your SPF record as the Value, and set TTL to automatic or 3600. The process is identical for DKIM and DMARC TXT records - just change the host and value.
The 10 DNS Lookup Limit (and How to Fix It)
Per RFC 7208, SPF records are limited to 10 DNS lookups. Every include statement triggers one or more lookups. Exceed the limit and the receiving server stops checking - your SPF record becomes invalid (PermError), which is treated as having no SPF at all.
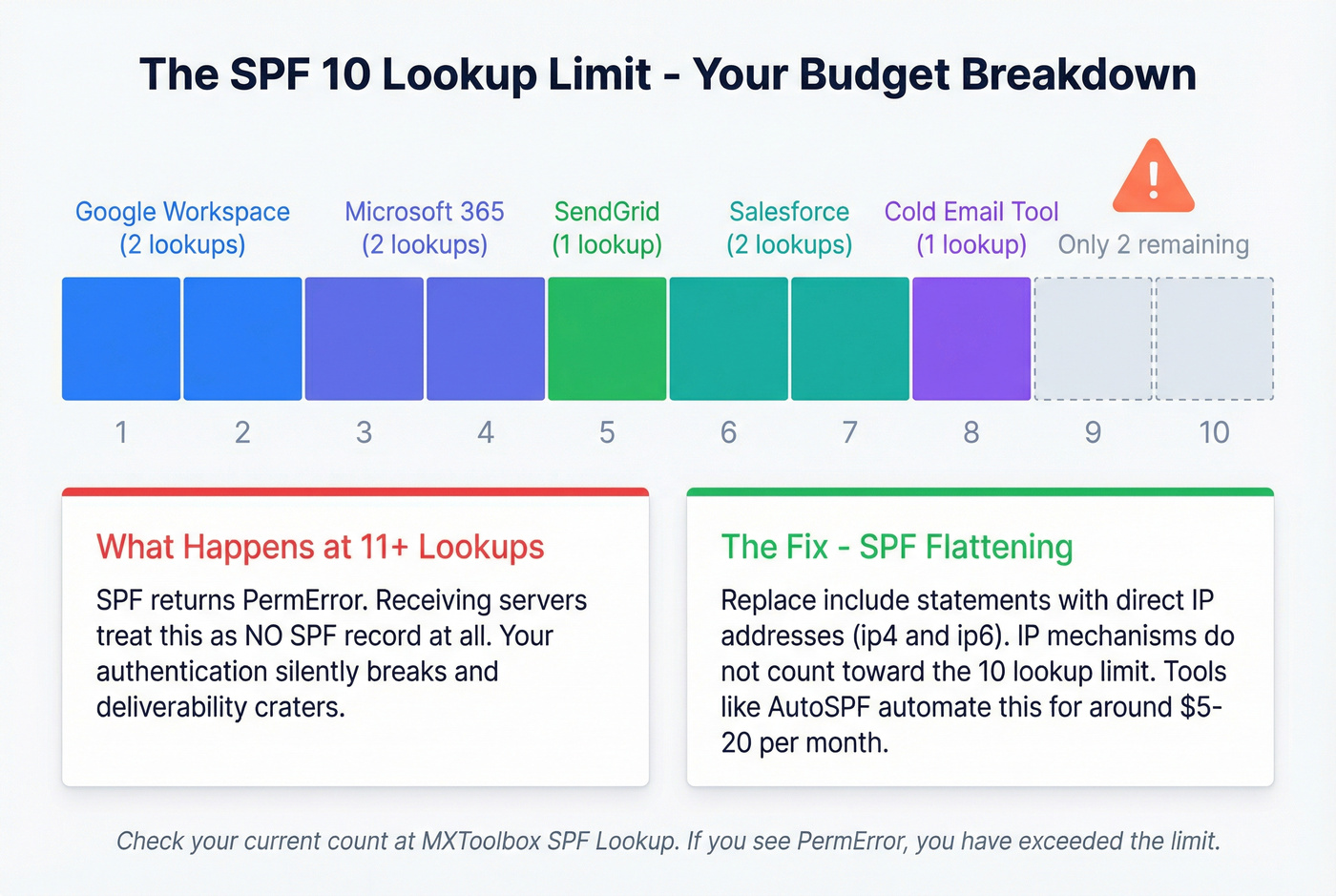
Here's a typical lookup budget:
- Google Workspace: 1-2 lookups
- Microsoft 365: 1-2 lookups
- SendGrid/SES: 1 lookup
- Salesforce: 1-2 lookups
- Cold email tool: 1 each
A typical enterprise stack consumes 7-9 lookups before you even add your cold outreach tool. That leaves almost no headroom.
The 10-lookup limit is the silent killer. Teams don't know they've hit it until deliverability craters.
The fix: SPF flattening. Replace include statements with direct IP addresses (ip4 and ip6 mechanisms). IP mechanisms don't count toward the 10-lookup limit. Tools like AutoSPF (~$5-20/month) automate this - they resolve your includes to IPs and keep the record updated as those IPs change.
To check your current lookup count, use MXToolbox's SPF lookup tool. If you see a PermError, you've exceeded the limit.
DKIM Setup - Step by Step
DKIM (DomainKeys Identified Mail) adds a cryptographic signature to every email you send. The receiving server checks this signature against a public key in your DNS. If it matches, the email hasn't been tampered with.
Here's the thing most guides bury: you need DKIM configured for every service that sends as your domain. Adding DKIM for Google Workspace but forgetting your cold email tool means half your emails fail DKIM alignment. Incomplete authentication configurations are the reason most outbound campaigns underperform. (If you want the conceptual overview, see SPF, DKIM & DMARC explained.)
Google Workspace DKIM
- Go to Admin console -> Apps -> Google Workspace -> Gmail -> Authenticate email
- Select your domain and click Generate new record
- Choose 2048-bit key length (Google's recommendation)
- Copy the generated TXT record
- Add it to your DNS as a TXT record at the selector hostname Google provides (usually
google._domainkey.yourdomain.com) - Return to the Admin console and click Start authentication
Microsoft 365 DKIM
- Go to Microsoft Defender portal -> Email & collaboration -> Policies -> DKIM
- Select your domain
- Enable DKIM signing
- Microsoft generates two CNAME records (selector1 and selector2)
- Add both to your DNS
- Return to the portal and confirm
Microsoft supports multiple selectors for different business units - useful if you're running separate campaigns from different teams.
Cold Email Tool DKIM (Instantly, Smartlead, Lemlist)
Each tool generates its own DKIM selector and key. The process is similar across all of them:
Smartlead: Navigate to the dashboard's DKIM settings. Smartlead generates a selector and public key - add the TXT record to your DNS.
Instantly and Lemlist: Both require you to add their DKIM selector to your domain's DNS. Check each tool's setup documentation for the exact selector value.
Use unique selectors per service. And always use 2048-bit keys - 1024-bit is the minimum, but 2048-bit is the standard in 2026.
DMARC Setup - Step by Step
DMARC (Domain-based Message Authentication, Reporting & Conformance) ties SPF and DKIM together. It tells receiving servers what to do when authentication fails - and sends you reports about it.
Your First DMARC Record
Add this TXT record at _dmarc.yourdomain.com:
v=DMARC1; p=none; rua=mailto:dmarc@yourdomain.com; adkim=r; aspf=r
Breaking it down:
v=DMARC1- version identifierp=none- policy (monitor only, no enforcement)rua=mailto:dmarc@yourdomain.com- where aggregate reports goadkim=r- relaxed DKIM alignment (correct for cold email with subdomains)aspf=r- relaxed SPF alignment
Relaxed alignment means the organizational domain just needs to match - outreach.yourcompany.com aligns with yourcompany.com. Strict alignment requires an exact domain match, which breaks subdomain setups.
The p=none vs p=reject Debate (Settled)
This is the #1 confusion point for cold emailers. Tools like EasyDMARC and MXToolbox flag p=none as "weak" or "monitoring mode" and push you toward p=reject. That's technically correct for security - but jumping straight to p=reject on a cold email domain is a mistake.
You probably have services sending as your domain that you've forgotten about. Your CRM sends notifications. Your support desk sends tickets. Your website sends form confirmations. If any of those aren't authenticated and you set p=reject, those emails get blocked.
Start with p=none. Monitor for 4 weeks. Fix everything that fails. Then escalate. I've tested this progression across dozens of domains - 4 weeks at p=none catches everything you missed. (If you want a workflow for this, see DMARC monitoring.)
DMARC Policy Progression Timeline
| Phase | Weeks | Policy | What Happens |
|---|---|---|---|
| Monitor | 1-4 | p=none | Reports only. Watch for legit senders failing. |
| Quarantine | 5-8 | p=quarantine; pct=50 | 50% of failures go to spam. Fix remaining issues. |
| Enforce | 9+ | p=reject | Unauthorized emails rejected. Full protection. |
The EasyDMARC and MXToolbox warnings about p=none being "weak" are expected during the monitoring phase - that's not a problem, it's the plan.
How to Verify Your Email Authentication Records
DNS changes can take 24-48 hours to propagate, though some take effect within an hour. Don't send campaigns until you've verified everything passes.
Here's the verification sequence:
- Check SPF: Go to MXToolbox -> SPF Record Lookup -> enter your domain. You should see a single valid SPF record with all your includes. Confirm the lookup count is 10 or under.
- Check DKIM: MXToolbox -> DKIM Lookup -> enter your domain and selector (e.g.,
googlefor Google Workspace). You should see a valid public key. - Check DMARC: MXToolbox -> DMARC Lookup -> enter your domain. You should see your DMARC record with the correct policy.
- Send a test email: Send from your cold email setup to a personal Gmail and Outlook address. Open the email, click the three dots -> "Show original" (Gmail) or view message headers (Outlook). Look for
spf=pass,dkim=pass, anddmarc=pass. - Run Mail-tester.com: Send an email to the address Mail-tester gives you. It returns a deliverability score out of 10 and flags specific issues.
- Use Google Admin Toolbox for deeper header analysis if anything looks off.
All three records need to show "pass." If any shows "fail" or "none," go back and fix it before sending a single campaign email.
The 5 Mistakes That Kill Cold Email Deliverability
A Reddit practitioner who audited 47 cold email setups in a single month found the same five problems over and over.
1. Multiple SPF records instead of one merged record.
Teams add a new tool and create a second SPF TXT record instead of merging the include into the existing one. Two SPF records = both invalid. Your domain effectively has no SPF at all.
2. Exceeding 10 DNS lookups.
Every include counts. Nested includes count too. If you're using Google Workspace + a CRM + a cold email tool + a transactional sender, you're probably at 8-9 lookups already. Add one more and everything breaks silently - no error message, just PermError in your DMARC reports. Outlook punishes this harder than any other ISP.
3. DKIM configured for email provider but not cold email tool.
You set up DKIM for Google Workspace. Great. But your Instantly or Smartlead emails are going out without DKIM signatures. Half your outbound fails DKIM alignment, and DMARC reports it as unauthorized.
4. Sending from primary business domain.
I've seen teams spend months recovering from this. One spam complaint and suddenly your CEO's emails bounce. Your support tickets land in spam. Your invoices disappear. Use a dedicated domain. Always.
5. DMARC set to p=none permanently with no enforcement plan.
p=none is a monitoring phase, not a permanent setting. If you leave it there forever, you're telling ISPs you don't care about enforcement. Outlook deprioritizes emails from domains with weak DMARC policies. Set a calendar reminder to escalate to p=quarantine after 4 weeks.
Post-Setup - Monitoring and Maintenance
Configuring email authentication isn't a one-time task. DNS records drift. You add new tools. Services change their sending IPs. Monthly monitoring catches problems before they tank your deliverability.
Google Postmaster Tools v2
Google Postmaster Tools is free and provides data directly from Gmail's internal systems. As of late 2025, Google retired the v1 interface entirely. The v2 dashboard shifted from reputation scores to compliance status - binary pass/fail on SPF/DKIM authentication, DMARC alignment, TLS encryption, and one-click unsubscribes.
Your spam rate is the new North Star metric. Keep it below 0.1% for healthy delivery. Above 0.3% consistently and your messages get blocked. The late-2025 enforcement update means a "Fail" on the compliance dashboard now allows Google to actively reject mail with 5xx errors - not just spam-folder it. (Benchmarks and limits: spam rate.)
Critical limitation: the spam rate only shows manual user reports, not automatic spam filtering. You can have a low spam rate while most emails are being auto-filtered. Focus on the 30-day trend, not individual day spikes. A 100% spam rate on a zero-send day is normal - it's delayed complaints divided by zero volume.
Reading Your DMARC Reports
If you set up the rua tag, you'll start receiving aggregate reports as XML files. They're unreadable in raw form. Use a free parser like EasyDMARC's XML Report Analyzer to make them human-friendly.
What to look for:
- Legitimate senders failing authentication - this means you missed an
includein SPF or forgot DKIM for a service - Unfamiliar sending IPs - someone is likely spoofing your domain
- Policy actions taken - confirms whether ISPs are enforcing your DMARC policy as intended
- PermError for SPF - a clue that you've exceeded the 10-lookup limit
- Outlook RUA vs. RUF gap - Outlook sends aggregate reports but does NOT send forensic (RUF) reports, so you'll get less granular failure data from Microsoft than from Gmail
Monthly Maintenance Checklist
- Run MXToolbox checks on SPF, DKIM, and DMARC
- Review DMARC aggregate reports for new failures
- Check Google Postmaster Tools spam rate trend
- Verify any new sending tools have been added to your SPF and DKIM
- Confirm your DMARC policy progression is on schedule
- Audit DNS for duplicate or stale records
- Apply a sunset policy - re-engage contacts at 60 days inactive, remove at 90 days
Set a recurring calendar reminder. 15 minutes a month prevents the kind of silent failures that take weeks to diagnose.
The Step Most Guides Skip - Verify Your List
You just spent an hour protecting your domain. Don't blow it by sending to dead addresses.
Only 23.6% of teams verify email lists before sending. That's staggering. Bounces above 1% trigger ISP penalties that undo all your authentication work. Authentication protects your domain identity - bad data destroys your sending reputation. (If you need an SOP, use our email verification list workflow.)
9% of webform entries are invalid from the start. Purchased lists are worse. Every bounce tells Gmail and Outlook that you don't maintain your lists, and they respond by throttling your entire domain.
Prospeo handles this with a 5-step verification process that catches invalid addresses, spam traps, and honeypots before they enter your sending sequence - 98% email accuracy, catch-all domain handling included. The platform integrates natively with Instantly, Smartlead, and Lemlist, so verified data flows directly into the tools you're already using for outbound. Upload a CSV or connect via API, and bad addresses get filtered before they ever touch your campaigns. (If you’re evaluating vendors, start with our ranked list of email verifier websites.)
There's a free tier to start: 75 emails and 100 Chrome extension credits per month. Enough to test the workflow before committing.

Running 3-5 domains with 4-6 inboxes each? That infrastructure only pays off if your contact data is clean. Prospeo refreshes 300M+ profiles every 7 days - not the 6-week industry average - so you're never emailing stale addresses that spike your bounce rate and trigger ISP flags.
Fresh data every 7 days means your warmup actually sticks.
Advanced - BIMI, ARC, and What Comes After DMARC Enforcement
Skip this section if your deals are under $15k and you're running cold outreach on fresh domains. The basics done right beat the advanced stuff done half-heartedly every single time.
BIMI (Brand Indicators for Message Identification) displays your brand logo next to emails in the inbox. It's the visual payoff for getting authentication right.
Requirements: DMARC policy at p=quarantine or p=reject (p=none won't work), a Verified Mark Certificate (VMC) from DigiCert (~$1,000-1,500/year), and a registered trademark.
DNS record format:
default._bimi.yourdomain.com TXT "v=BIMI1; l=https://yourdomain.com/logo.svg; a=https://yourdomain.com/vmc.pem"
Gmail, Yahoo, and Apple Mail support BIMI. Microsoft hasn't announced support yet. BIMI is primarily relevant for established brands with high volume - not cold email on fresh domains. But if you're running outbound from a mature subdomain with p=reject, it's a nice credibility boost.
For forwarded emails, ARC (Authenticated Received Chain) preserves DMARC alignment across intermediary servers - Outlook specifically recommends it for mailing lists and forwarding scenarios.
FAQ
How long does SPF, DKIM, and DMARC setup take to start working for cold email?
DNS propagation takes 24-48 hours, though changes sometimes take effect within an hour. Don't send campaigns until you've verified all three records pass using MXToolbox. Send a test email and check the headers for spf=pass, dkim=pass, and dmarc=pass before launching anything.
Can I use p=reject for DMARC right away?
No. Start with p=none for 4 weeks to monitor which services send as your domain. Then move to p=quarantine at 50%, then p=reject. Jumping straight to reject blocks legitimate emails from services you forgot to authenticate, like CRMs, support desks, and form builders.
Do I need separate SPF and DKIM records for each cold email tool?
DKIM yes - each tool needs its own unique selector and key added to your DNS. SPF no - merge all include statements into one single TXT record. Publishing multiple SPF records invalidates all of them. This is the most common setup mistake across cold email infrastructure.
Why are my emails landing in spam even with authentication configured?
Authentication is necessary but not sufficient. Top causes: exceeding 10 SPF lookups (silent PermError), missing DKIM for your cold email tool, sending to unverified lists with bounce rates above 1%, or pushing too much volume too fast on a new domain. Verifying your list before sending catches bad addresses before they trigger ISP penalties.
Does bulk email authentication differ from standard email setup?
The DNS records are identical, but stakes are higher at volume. Sending thousands of emails daily means even a small misconfiguration - exceeding the 10-lookup limit or missing DKIM on one tool - compounding quickly. Outlook specifically targets domains sending 5,000+ messages daily, so authentication has to be flawless before you scale.