Email Sending Infrastructure: The 2026 Practitioner's Guide
You built the sequences. You wrote the copy. You A/B tested the subject lines. Then deliverability cratered - 95% inbox placement in month one, under 50% within three to six months. The emails didn't get worse. The email sending infrastructure underneath them couldn't handle the scale.
Teams invest in messaging and ignore the plumbing. Then they blame the copy, the tool, or the ICP when the real problem is a misconfigured DNS record, a cold IP, or a list full of spam traps. About 16.9% of legitimate emails never reach inboxes. That's one in six emails vanishing into nothing.
What follows covers authentication, IP strategy, provider selection, warm-up protocols, monitoring, and the data quality layer that most infrastructure guides completely ignore. No glossary padding. Just the decisions that matter and how to get them right.
What You Need (Quick Version)
Four decisions determine whether your emails reach the inbox. Get any one wrong and the other three can't save you.
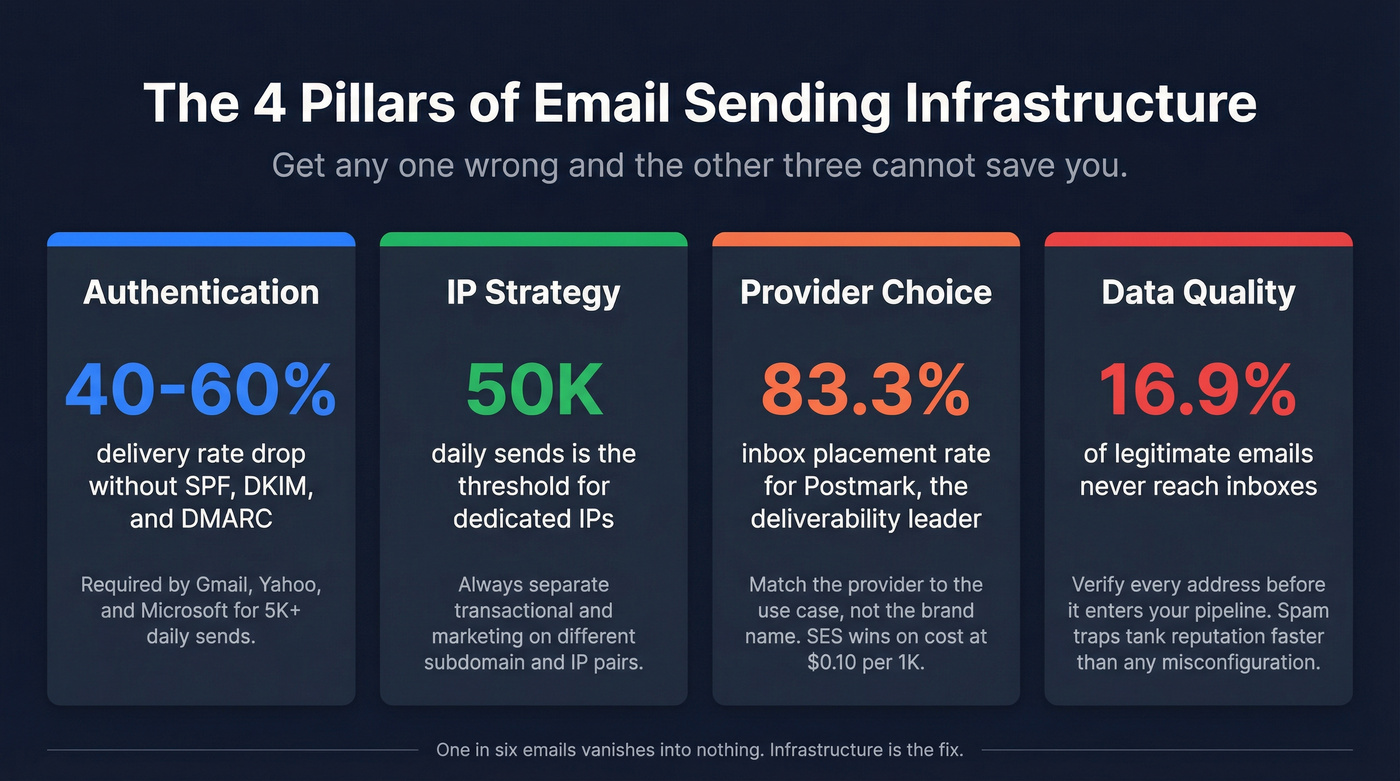
Authentication stack. SPF, DKIM, and DMARC are non-negotiable. Gmail, Yahoo, and Microsoft now require all three for bulk senders. If you're still on DMARC p=none, you're running without a seatbelt. Move to [p=quarantine](https://dmarcian.com/policy-modes-quarantine-vs-reject/) within 90 days, p=reject within 6 months.
IP strategy. Shared IPs if you're under 50K sends/day. Dedicated IPs above that - but only with a 30-day warm-up plan. Never send from your root domain. Segregate transactional and marketing on separate subdomain/IP pairs. (If you're debating this split for outbound, see dedicated vs shared IP.)
Provider choice. Postmark leads on deliverability (83.3% inbox placement in independent testing). Amazon SES is unbeatable on cost ($0.10/1K emails). For cold email, Google Workspace resellers plus shared SMTP is the default stack. Match the provider to the use case, not the brand name.
Data quality. This is the layer most guides skip - and it's the fastest way to destroy everything else you build. Sending to invalid addresses, spam traps, and honeypots tanks your sender reputation faster than any misconfiguration. Verify every address before it enters your sending pipeline, and use a provider with a fast refresh cycle so "verified" doesn't mean "verified six weeks ago." (If you need a process, use an email verification list SOP.)
What Email Sending Infrastructure Actually Is
The full technical stack that moves an email from your application to a recipient's inbox isn't one thing. It's a chain of components where any weak link kills deliverability.
Here's how the pieces connect:
Your application hands a message to a Mail Transfer Agent (MTA) - the software that routes email. The MTA connects to an SMTP server (yours or a provider's) that handles the actual transmission. Before sending, the SMTP server references your DNS records - SPF, DKIM, DMARC - to prove you're authorized to send from that domain. The importance of DNS in email delivery can't be overstated: these records are the first thing receiving servers check, and failures here cascade into every downstream metric. The email travels over TLS-encrypted connections from your sending IP (shared or dedicated) through the internet to the recipient's mail server, which checks your authentication, IP reputation, and content before deciding: inbox, spam, or reject.
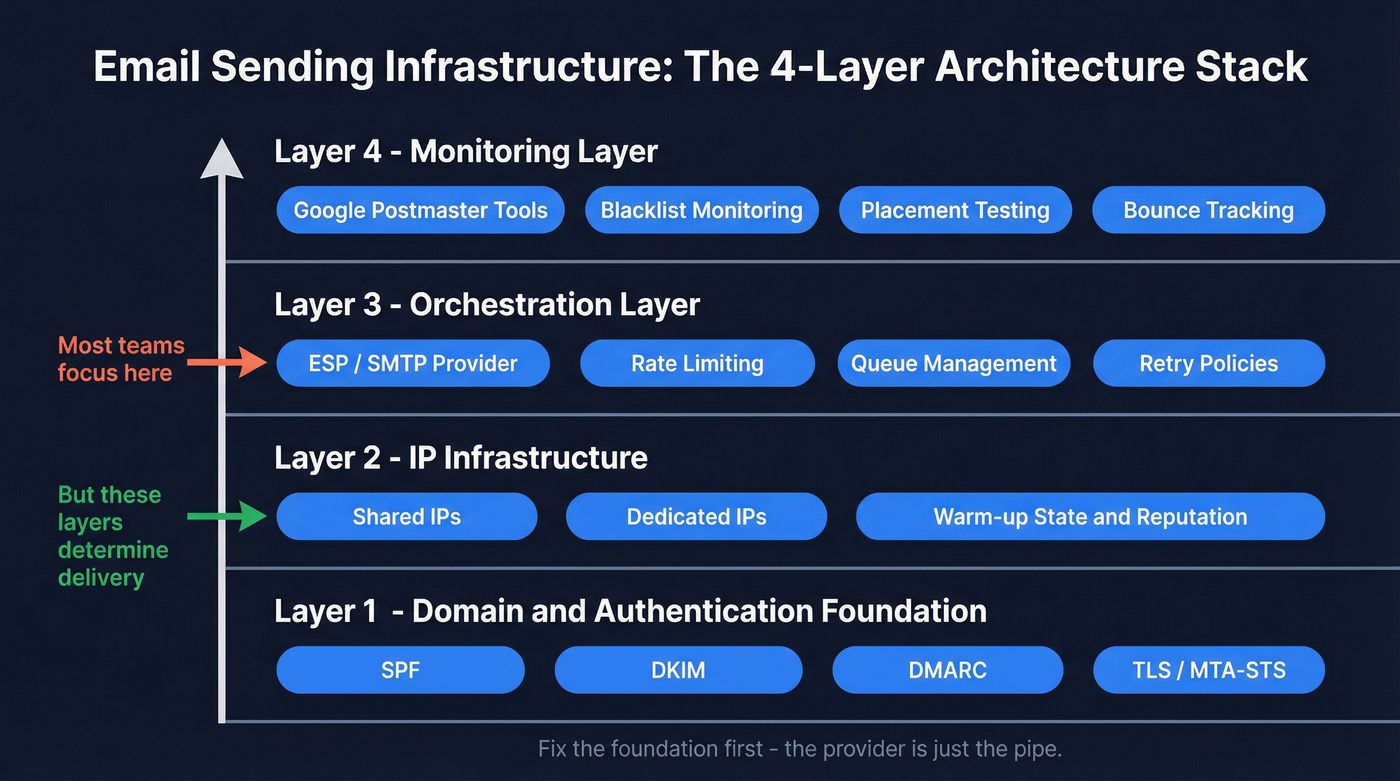
Think of it as a four-layer architecture:
- Domain & Authentication Foundation - Your domains, subdomains, DNS records (SPF, DKIM, DMARC), and transport security (TLS, MTA-STS)
- IP Infrastructure - Shared or dedicated IPs, warm-up state, reputation scores
- Orchestration Layer - Your ESP or SMTP provider, sending logic, rate limiting, queue management, and retry policies
- Monitoring Layer - Google Postmaster Tools, blacklist monitoring, placement testing, bounce tracking
Most teams obsess over layer 3 (which provider to pick) and ignore layers 1 and 2 (which actually determine whether emails land). The provider is just the pipe. Authentication and IP reputation are the gatekeepers.
It also helps to think about the three categories of email your infrastructure handles: user-to-user (internal communication), application-driven (transactional - password resets, receipts, notifications), and marketing/outbound (campaigns, sequences, cold email). Each category has different volume patterns, reputation implications, and provider requirements. Mixing them on the same infrastructure is one of the most common mistakes we see - and it's especially dangerous when your marketing sends share IPs with transactional messages, since a spam complaint on a campaign can delay password resets.
Without authentication, delivery rates drop 40-60% on major providers. That's not a gradual decline. It's an immediate penalty.
Authentication - The Non-Negotiable Foundation
Gmail, Yahoo, and Microsoft now require authentication for anyone sending 5,000+ emails per day. About 40% of senders either aren't implementing both SPF and DKIM or don't know whether they are - which is arguably worse. If that's you, stop reading and fix it today. Everything else in this guide is pointless without authentication. BEC losses exceeded $1.8 billion in 2020, largely enabled by weak email authentication. The stakes aren't theoretical.
SPF, DKIM, and DMARC Setup
SPF (Sender Policy Framework) tells receiving servers which IPs are authorized to send email for your domain. One SPF record per domain - that's a hard rule. You get a maximum of 10 DNS lookups per SPF check, so use include mechanisms for third-party services rather than listing individual IPs.
A basic SPF record looks like:
v=spf1 include:_spf.google.com include:sendgrid.net ~all
Every ESP you add eats into that 10-lookup limit. If you're using four or five services, you'll hit it fast. SPF flattening (replacing includes with explicit IPs) works but creates a maintenance headache - IPs change, and your record goes stale. (If you want the syntax details, see SPF record.)
DKIM (DomainKeys Identified Mail) adds a cryptographic signature to every email, proving the message hasn't been altered in transit. Your sending server signs with a private key; the receiving server verifies against a public key published in your DNS.
The critical detail most guides skip: key rotation. Use selector-based rotation with a 2-week overlap period. Publish the new key, wait two weeks while both old and new selectors are active, then retire the old one. This prevents verification failures during the transition.
DMARC (Domain-based Message Authentication, Reporting & Conformance) ties SPF and DKIM together and tells receiving servers what to do when authentication fails. Start with a monitoring-only record:
v=DMARC1; p=none; rua=mailto:dmarc-reports@yourdomain.com; ruf=mailto:dmarc-failures@yourdomain.com; pct=100
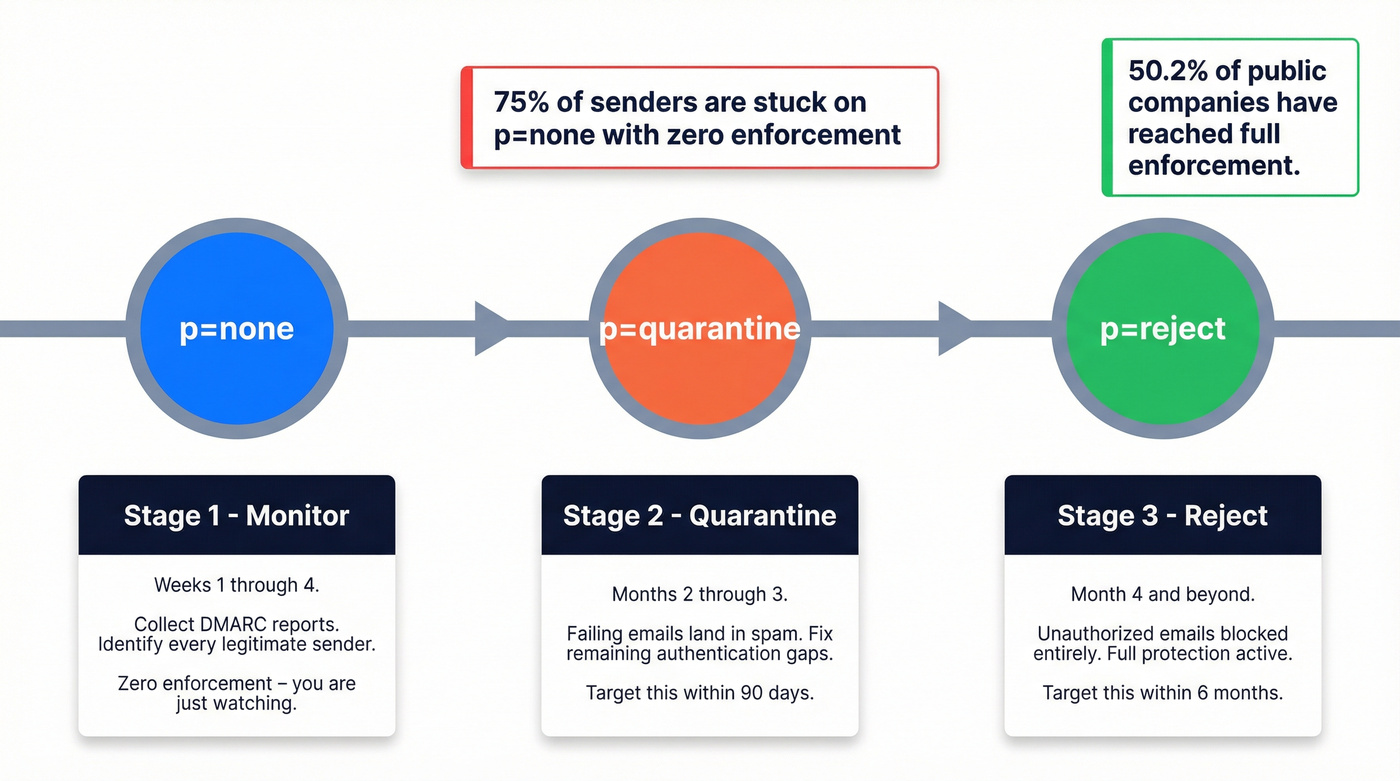
Wait 48-72 hours for initial reports to come in. Then follow this progression:
| Stage | Policy | Timeline | Action |
|---|---|---|---|
| Monitor | p=none |
Weeks 1-4 | Collect reports, identify all legitimate senders |
| Quarantine | p=quarantine |
Months 2-3 | Failing emails go to spam; fix remaining auth gaps |
| Reject | p=reject |
Month 4+ | Unauthorized emails blocked entirely |
The Quick Version section recommends quarantine within 90 days and reject within 6 months - that's the conservative timeline for teams with complex sending ecosystems. The table above is an aggressive schedule that works for teams with fewer third-party senders to audit.
75% of senders are still stuck on p=none - monitoring mode with zero enforcement. Meanwhile, 50.2% of public companies have reached full enforcement. The gap between "we have DMARC" and "DMARC actually protects us" is enormous. Don't be in the 75%. (If you're operationalizing reports, use a DMARC monitoring workflow.)
BIMI - The Optional Extra
BIMI (Brand Indicators for Message Identification) displays your brand logo next to emails in supported inboxes. It requires DMARC at p=quarantine or p=reject plus a Verified Mark Certificate (VMC). Nice for brand recognition, but it's a cherry on top - not a priority until your authentication is fully enforced.
Transport Security (TLS, MTA-STS, DANE)
This is the section no one else covers. Every competitor article on the SERP stops at DMARC. But transport security is what prevents your authenticated emails from being intercepted in transit.
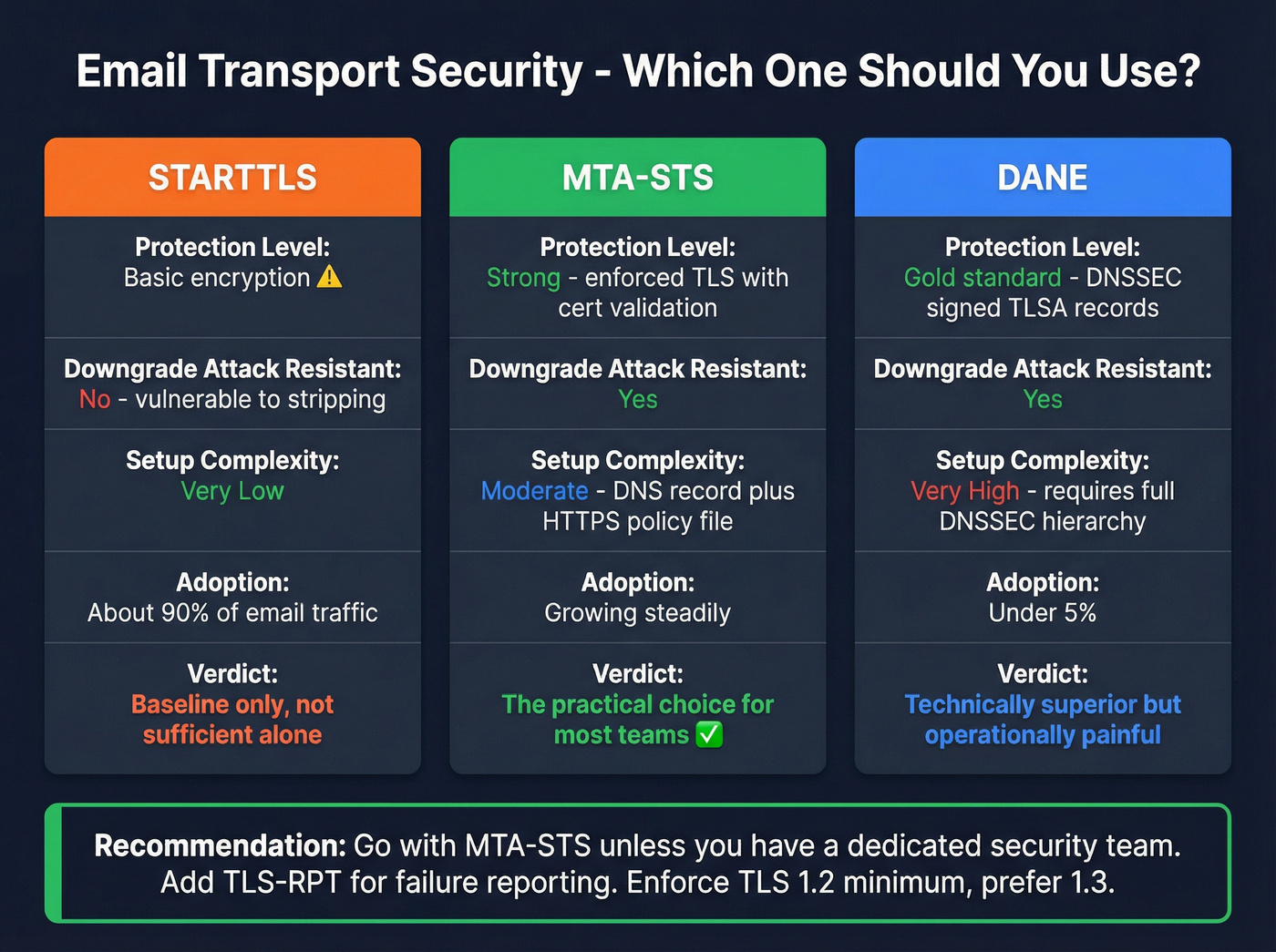
STARTTLS upgrades a plaintext SMTP connection to TLS encryption. About 90% of email traffic uses it. The problem: STARTTLS is vulnerable to downgrade attacks. A man-in-the-middle can strip the STARTTLS command and force plaintext transmission. Your email is authenticated but not encrypted.
MTA-STS fixes this. You publish a DNS TXT record plus an HTTPS-hosted policy file that tells sending servers: "Only deliver to us over TLS with a valid certificate." It prevents downgrade attacks and can be implemented in days. Set max_age to 2-4 weeks initially.
DANE is the gold standard - DNSSEC-signed TLSA records that specify exactly which certificates are valid, eliminating reliance on the public CA system entirely. But it requires DNSSEC throughout your entire DNS hierarchy. Adoption is under 5% because the complexity is brutal.
Here's the thing: MTA-STS is the practical choice for most teams. DANE is technically superior but operationally painful. Unless you have a dedicated security team that wants this project, go MTA-STS.
Set up TLS-RPT alongside either option - it sends you aggregate reports about TLS negotiation failures so you can catch issues before they affect delivery. Enforce TLS 1.2 minimum, prefer 1.3, and disable SSLv3, TLS 1.0, and 1.1.

You just read that 16.9% of legitimate emails never reach inboxes - and bad data is the fastest way to tank sender reputation. Prospeo's 5-step verification with spam-trap removal and honeypot filtering means every address entering your sending pipeline is verified at 98% accuracy, refreshed every 7 days - not 6 weeks ago.
Stop feeding spam traps into the infrastructure you spent months building.
IP and Domain Strategy
Shared vs. Dedicated IPs
The shared-vs-dedicated decision comes down to volume:
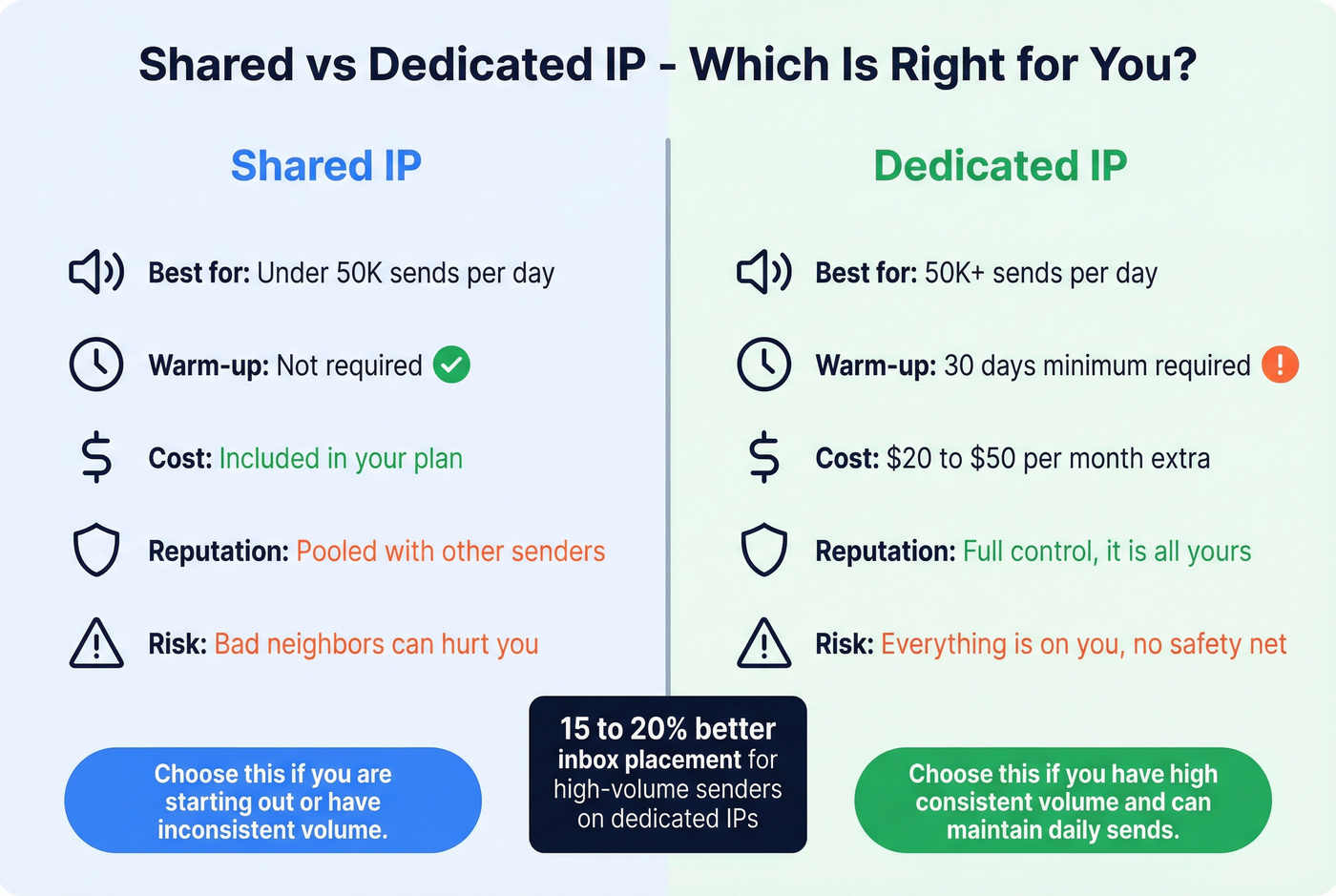
| Factor | Shared IP | Dedicated IP |
|---|---|---|
| Best for | Under 50,000 sends/day | 50,000+ sends/day |
| Warm-up required | No | 30 days minimum |
| Cost | Included in plan | $20-50/mo extra |
| Reputation control | Pooled with others | Full control |
| Risk | Bad neighbors | All on you |
Dedicated IPs achieve 15-20% better inbox placement for high-volume senders. But that advantage only materializes if you have enough volume to maintain consistent sending patterns. A dedicated IP that goes quiet for a week starts losing reputation.
A note on thresholds: providers like Amazon SES and SendGrid typically offer dedicated IPs starting around 50K sends/day. But having access to one doesn't mean you should use it. If you don't have enough consistent volume, you won't build and maintain a strong standalone reputation. You're often better off on a shared IP with a reputable provider like Postmark or Amazon SES.
Domain Strategy - Subdomains, TLDs, and Cold Email Domains
Never send from your root domain. Full stop.
If acme.com gets flagged, your entire brand email is compromised - password resets, invoices, everything. Segregate by function:
mail.acme.comfor transactional emailnews.acme.comfor marketing- Separate domains entirely for cold outbound
For cold email, use brand variants: tryacme.com, acme-mail.com, getacme.co. Avoid cheap TLDs like .info and .biz - mailbox providers treat them as spam signals.
.com has the best deliverability and credibility across the board. The volume math matters too: instead of sending 1,000 emails per week from one domain, send ~200 per week from five domains. This distributes reputation risk and keeps per-domain volume in the safe zone.
Domain-to-inbox ratio: 1 domain per 2-3 inboxes. Three mailboxes per domain is the sweet spot for Google Workspace. More than that and you're creating patterns that look automated.
TLD alignment for international sending: If you have domain.fr and domain.com, use news.domain.fr for French-language newsletters and news.domain.com for global sends. The TLD of your links should match the TLD of your sending domain.
Set up redirects from all cold email domains to your main website. It adds legitimacy when prospects check the domain.
IP Warm-Up Protocol
Skip warm-up and nothing else in this guide matters.
A brand-new dedicated IP has zero reputation. Mailbox providers don't trust it. Sending 10,000 emails on day one from a cold IP is the fastest way to land on a blacklist.
Here's a 30-day warm-up schedule based on Inboxroad's protocol for 2 dedicated IPs:
| Day | Hourly Limit | Daily Limit | Cumulative |
|---|---|---|---|
| 1 | 20 | 480 | 480 |
| 3 | 39 | 936 | 2,832 |
| 7 | 158 | 3,792 | 14,064 |
| 14 | 726 | 17,424 | 88,200 |
| 21 | 1,802 | 43,488 | 345,000 |
| 30 | 4,694 | 112,656 | ~1,013,832 |
Gmail is more conservative. If Gmail is your primary audience (at 48.5% of all mailboxes), use this schedule instead:
| Day | Gmail Daily Limit |
|---|---|
| 1 | 100 |
| 7 | 400 |
| 14 | 1,000 |
For cold email specifically, the week-by-week targets are even more gradual:
- Week 1: 10-20 emails per inbox per day
- Week 2: 20-40
- Week 3: 40-60
- Week 4: 60-100
Start with your most engaged segments - contacts who've opened or clicked in the last 30-90 days, double opt-ins, VIP accounts. These recipients are most likely to engage, which sends positive signals to mailbox providers.
Common warm-up mistakes:
- Sending to purchased or unverified lists during warm-up (instant reputation damage)
- Scaling too fast because "we need to hit quota this month"
- Inconsistent sending patterns - blasting Monday, silent Tuesday through Friday
One more thing: an IP goes cold again after 30 days of no sending. If you pause campaigns for a month, you're essentially starting over. Plan for consistent volume or accept the re-warm cost. (If you want the mailbox-level version, follow how to warm up an email address.)
The 4 Types of Bulk Email Infrastructure (and What Each Costs)
Not all infrastructure is created equal. The type you choose depends on your use case, volume, and risk tolerance.
| Type | Cost | Send Limit | Warm-Up | Best For |
|---|---|---|---|---|
| GW/M365 resellers | $2.50-3.50/box | 15-25/box/day | 14 days | Cold email default |
| Azure inboxes | ~$1-2/box | 5-10/box/day | Required | Nothing (avoid) |
| Shared SMTP | $3-15/inbox | Varies by plan | Provider-managed | Supplemental volume |
| Dedicated SMTP | $50-200+/mo | 50K+/month | 30 days | High-volume ops |
Google Workspace / M365 resellers are the default cold email stack. Set up 3-5 mailboxes per domain, warm each for 14 days minimum, and send 15-25 emails per mailbox once warmed. At $2.50-3.50 per mailbox, it's cheap and reliable. The constraint is per-mailbox volume - you scale by adding domains and mailboxes, not by pushing more through existing ones.
Azure inboxes deserve a special callout: avoid them. You get ~10 inboxes per domain but only 5-10 sends per day per inbox. At least two companies building Azure-based cold email infrastructure have shut down completely. Don't build on it.
Shared SMTP providers - Mailforge, Mailscale, Mailreef - run $3-15 per inbox and handle warm-up on their end. They're good as a supplemental layer alongside GW/M365, adding volume capacity without the per-mailbox limits of Google.
Dedicated SMTP (Infraforge, mailin.ai, Halon) only makes sense for teams doing 50K+ sends per month. You get full control over IP reputation and sending patterns, but you're responsible for warm-up and monitoring. Choosing the right tool at this tier matters - the wrong one can leave you managing queue failures and bounce handling manually.
The diversification rule: Never put all your eggs in one basket. Use 2-3 domain registrars, 2-4 ESPs minimum, and never put hundreds of accounts in one Google Panel or Microsoft tenant. That screams "spammer" to the provider and risks a single point of failure taking down your entire operation.
Build vs. Buy - The Decision Framework
Self-hosted email is a trap for 95% of teams.
| Factor | Self-Hosted | Cloud/Managed |
|---|---|---|
| Inbox placement | 40-60% | 90-99% |
| Monthly cost (100K-500K) | $500-2,000 | $10-90 |
| DevOps time | 5-10 hrs/month | Near zero |
| IP reputation | Build from scratch | Inherited/shared |
| Control | Total | Provider-dependent |
The self-hosted math: AWS storage runs $0.08-0.16/user/month. Add an EC2 instance ($20-100/month), dedicated IPs ($2-5/IP/month), and - here's the killer - DevOps time. At 5-10 hours per month and $75-150/hour for someone who actually knows mail servers, you're looking at $375-1,500/month just in labor. Plus the ongoing burden of monitoring queues, handling abuse reports, updating configurations, and managing storage.
The deliverability gap is the real problem. Professional infrastructure achieves 90-99% inbox placement. A basic self-hosted SMTP server? 40-60%. That's not a small difference - it's the difference between a working outbound program and one that's burning money.
I've seen exactly one company under 500K monthly sends make self-hosted work, and they had a former Postfix maintainer on staff. The math only pencils out above 500K-1M emails per month with a dedicated DevOps engineer who actually wants to manage a mail server. That engineer doesn't exist at most companies.
Self-hosted makes sense for military, healthcare with strict data residency requirements, or organizations with a strong DevOps team and clear privacy mandates. Everyone else should buy.
Email Sending Infrastructure Providers Compared
Here's what you're actually paying across the major providers:
| Provider | Free Tier | Starting Price | ~Cost/100K | Best For |
|---|---|---|---|---|
| Amazon SES | 3K/mo (12 mo) | $0.10/1K | ~$10 | Budget + AWS teams |
| Postmark | None | $15/mo | ~$15 | Transactional reliability |
| Mailtrap | 4K/mo | $15/mo | Varies | Testing + sending |
| Brevo | 300/day | $15/mo | Varies | Marketing + transactional |
| Mailgun | 100/day | Flex (pay-as-you-go); Foundation $35/mo | ~$35-90 | Developer-first |
| SendGrid | 100/day | $19.95/mo | ~$40-90 | Brand recognition |
| Resend | 3K/mo | $20/mo | ~$40 | Modern DX / React |
| SparkPost/Bird | None | $20/mo | Varies | Enterprise volume |
| Mailchimp Trans. | None | $20/mo* | Varies | Mailchimp users |
*Requires a Mailchimp Marketing subscription on top.
Now here's what actually matters - independent deliverability testing. These results come from tests run on free plans with shared IPs, same email template across all providers:
| Provider | Inbox % | Spam % | Missing % | Tabs % |
|---|---|---|---|---|
| Postmark | 83.3% | 14.3% | 0.9% | 1.0% |
| Mailtrap | 78.8% | 14.4% | 2.0% | 4.8% |
| Amazon SES | 77.1% | 20.0% | 1.0% | 1.9% |
| Mailgun | 71.4% | 23.8% | 1.0% | 3.8% |
| SendGrid | 61.0% | 17.1% | 20.9% | 1.0% |
Look at SendGrid's numbers. 61% inbox placement and 20.9% missing - meaning one in five emails just vanished. SendGrid processes 60 billion emails per month and has massive brand recognition, but its reputation exceeds its current performance. I've seen teams default to SendGrid because "everyone uses it" and then wonder why deliverability is mediocre.
My hot take: If your deals average under $10K, you probably don't need a premium ESP at all. Google Workspace resellers for cold outbound and Amazon SES for transactional will outperform most $200/month ESP plans - and cost a fraction. The expensive providers justify themselves at scale, not at startup volumes.
Quick recommendations by use case:
Transactional email: Postmark is the clear #1. 83.3% inbox placement, purpose-built for transactional, and they actively reject bulk marketing senders - which keeps their shared IP reputation clean. Amazon SES is #2 if you're already on AWS and want to save money.
Cold email: Google Workspace resellers + shared SMTP (Mailforge, Mailscale) as the default stack. Don't use traditional ESPs for cold outbound - they'll shut you down. (If you're building sequences, start with a B2B cold email sequence that’s deliverability-first.)
Budget-conscious: Amazon SES at $0.10 per 1,000 emails is unbeatable. The free tier gives you 3,000/month for the first year. The tradeoff is setup complexity - SES assumes you know what you're doing.
Developer experience: Resend is the modern pick. React Email integration, clean API, and a developer-first approach that makes SendGrid's API feel dated.
Enterprise volume: SparkPost (now Bird) handles 40% of commercial email globally. But their customer support is rated 3.0/5 - the weakest area by far. If you're sending millions per day and have internal deliverability expertise, it works. If you need hand-holding, look elsewhere.
Postmark is the quiet winner in this space. It doesn't have SendGrid's marketing budget or Amazon's ecosystem lock-in, but it delivers more emails to inboxes than either of them.
Data Quality as Infrastructure - The Layer Most Guides Skip
You can nail authentication, warm up your IPs perfectly, choose the right provider, and still destroy your sender reputation by sending to invalid addresses.
This is the infrastructure layer that every other guide treats as an afterthought. It shouldn't be. Bad data is the problem you don't see until your IP is already damaged - a single campaign sent to a list with spam traps and honeypots can tank an IP reputation you spent 30 days building. The bounce rate threshold is 2%. Go above that consistently and mailbox providers start throttling or blocking you.
Tools like Prospeo catch these problems before they enter your sending queue - handling catch-all domains (where the server accepts everything but most addresses are dead), removing known spam traps, filtering honeypots, and confirming deliverability at 98% accuracy with a 7-day data refresh cycle. The industry average refresh is 6 weeks, which means most "verified" lists are already decaying by the time you send. (If you’re comparing vendors, start with email verifier websites.)
The proof is in the numbers. Meritt saw bounce rates drop from 35% to under 4% after switching to verified data. Stack Optimize maintains 94%+ deliverability with under 3% bounce rates and zero domain flags across all their clients. These aren't marginal improvements - they're the difference between a functioning outbound program and one that's actively damaging your domain.
Here's how we think about it: authentication is your ID card. IP warm-up is your credit history. Data quality is whether you're sending mail to real addresses or shouting into a void. Skip any one of them and the other two can't compensate. (To go deeper on the ops side, see data quality.)

You configured SPF, DKIM, and DMARC. You warmed your IPs for 30 days. Then one batch of stale contacts destroyed your domain reputation overnight. Prospeo's 7-day data refresh cycle and catch-all domain verification ensure your list stays clean - at $0.01 per email, not $1.
Great infrastructure deserves data that won't wreck it.
Monitoring Your Email Sending Infrastructure
Building infrastructure is half the job. Monitoring it is the other half - and the half that prevents slow-motion disasters.
Google Postmaster Tools (Free, Essential)
Gmail holds 48.5% of all mailboxes. Google Postmaster Tools is the only way to see how Gmail specifically treats your email. It's free. It's non-negotiable.
Setup: add your sending domain, verify via DNS TXT record, grant team access. Takes 10 minutes.
As of late 2025, Google permanently removed the IP Reputation and Domain Reputation dashboards. What's left - and what matters - are two dashboards:
Compliance Status shows pass/fail on SPF, DKIM, DMARC, PTR records, TLS, and one-click unsubscribe. The enforcement phase is now live. A "Fail" on this dashboard allows Google to reject your mail with 5xx errors - not just filter to spam, but actively bounce it.
Spam Rate tracks the percentage of your emails that recipients manually report as spam. The threshold is 0.3%. Stay below it or face throttling. (For the full set of limits, track the spam rate threshold.)
Here's the critical limitation most people miss: the spam rate only counts manual user reports. It does NOT include emails that Google automatically filters to spam. You can have a "healthy" 0.1% spam rate while the majority of your emails are landing in spam folders. That's why you can't rely on Postmaster Tools alone.
Feedback Loops (FBLs)
Register for Feedback Loops with major ISPs - Microsoft, Yahoo, and Comcast all offer them. FBLs send you notifications when recipients mark your email as spam, giving you real-time data to suppress complainers before they damage your reputation. Most ESPs handle FBL registration automatically, but if you're on dedicated infrastructure, set these up manually on day one.
Blacklist Monitoring
Getting blacklisted is often a silent event. Most detections happen after hours or on weekends. By the time you notice on Monday morning, you've been blocked for 48 hours and your warm-up progress is wrecked.
MXToolbox checks 120+ blacklists with continuous monitoring and delisting assistance. Runs about $930/year - worth it for any team sending at volume.
Spamhaus Blocklist Explorer is free and covers the most influential blacklist in the industry. Self-service removal process. Check it weekly at minimum.
SenderScore (Validity) gives you a 0-100 reputation score - think of it as a credit score for your sending IP. Free to check. (If you want a workflow for this, use a sender score checker.)
GlockApps tests inbox placement across 30+ blocklists with a free 14-day trial. This is the tool that tells you where your emails actually land, not just whether they were "delivered" (which can mean spam folder).
Key Metrics to Watch
Three numbers matter:
- Spam complaint rate: Below 0.3% (Google's threshold). Below 0.1% is ideal.
- Bounce rate: Below 2%. Consistently above that and you're damaging your IP.
- Inbox placement rate: Test with GlockApps, not open rates.
Open rates are a vanity metric. Apple Mail Privacy Protection pre-loads tracking pixels, making every Apple Mail user look like they opened your email. Image proxy caching does the same across other clients. If you're using open rates to gauge deliverability, you're flying blind.
Common Mistakes That Kill Deliverability
I've watched teams build solid infrastructure and then sabotage it with avoidable errors. Here are the ten that come up most often:
1. Skipping or rushing IP warm-up. "We need to hit quota" isn't a reason to blast 10,000 emails from a week-old IP. A 30-day warm-up isn't optional - it's the cost of doing business with dedicated IPs.
2. Too many inboxes per domain. Three mailboxes per domain is the sweet spot for Google Workspace. Five or more creates patterns that look automated to spam filters.
3. All domains from one registrar. If that registrar flags your account or has an outage, your entire sending operation goes dark. Spread across 2-3 registrars.
4. All inboxes in one Google Panel or Microsoft tenant. Hundreds of accounts in a single tenant screams "spammer." Diversify across multiple tenants.
5. Not verifying your email list. This is the most expensive mistake because it compounds. Every bounce, every spam trap hit, every honeypot detection chips away at your IP reputation. Verify before you send - always. (If you need the full workflow, read how to verify an email address.)
6. Pushing volume on existing inboxes instead of adding domains. When you need more capacity, add domains and mailboxes. Don't crank up sends per inbox from 20 to 50 - that's how you get flagged.
7. Using open rates as a deliverability metric. Apple MPP and image proxy caching have made open rates meaningless. Use placement testing tools instead.
8. No placement testing or blacklist monitoring. "Delivered" doesn't mean "inbox." It can mean spam folder. If you're not testing placement, you don't know where your emails land.
9. Sending from your root domain. If acme.com gets flagged, your transactional email (password resets, invoices, receipts) goes down with it. Always use subdomains.
10. Outdated TLS certificates or no transport security. Expired certificates cause delivery failures. No MTA-STS means you're vulnerable to downgrade attacks. Both are fixable in hours.
FAQ
How long does email infrastructure setup take from scratch?
Budget 6 weeks total: 2-4 weeks for authentication, domain setup, and DNS propagation, plus 30 days for full IP warm-up on dedicated IPs. Using shared IPs eliminates the warm-up phase, compressing the timeline to roughly 2 weeks.
How much does email infrastructure cost per month?
Cloud providers range from $10/month (Amazon SES at 100K emails) to $90+ (SendGrid Pro). Cold email setups run $2.50-15 per mailbox. Self-hosted costs $500-2,000/month when you factor in DevOps labor at $75-150/hour.
What's the difference between shared and dedicated IPs?
Shared IPs pool reputation across senders - good for under 50K emails/day with no warm-up needed. Dedicated IPs give full reputation control but require 30-day warm-up and consistent daily volume above 50K to maintain that reputation.
How do I know if my emails are landing in spam?
Use Google Postmaster Tools for Gmail-specific spam rate data and GlockApps for actual inbox placement testing across providers. Don't rely on open rates - Apple Mail Privacy Protection inflates them by pre-loading tracking pixels.
How does email verification protect sending infrastructure?
Invalid addresses, spam traps, and honeypots spike bounce rates above the 2% threshold and destroy IP reputation - often irreversibly. Verifying emails before sending with a tool like Prospeo (98% accuracy, 7-day refresh cycle) keeps bounce rates low and protects the domain health you've spent weeks building.